When is it OK to be a control freak? It’s not ideal for social interactions, but when it comes to managing application traffic, having as much control as possible can be a good thing.
Exerting precise control over how traffic interacts with an application makes it possible to tailor the function of those applications to specific business needs. The scenarios are myriad: directly specifying the destinations where traffic needs to go; sending traffic to a pool, an individual pool member, a port, or a URI; limiting the number of connections that a client IP can establish, if so desired. With the proper tools, it’s no longer necessary to settle for a cookie-cutter framework of how traffic interacts with applications.
Tools that enable precise control over those interactions improve workflows. Moreover, knowing how and where these tools are applied lets you understand how they can be used even more effectively. Oftentimes, observing how a tool is working is equally as important as having enhanced control over that tool, because it’s critically important to know what’s going on inside the services that drive your organization’s revenue.
Today's digital landscape presents an immense amount of diversity and complexity to mission-critical apps. Having a solution that offers a control and visibility is table stakes for anyone who manages applications and app traffic day in and day out.
The digital world is not made up of square pegs and square holes. Applications are unique—in their design, function, roles, and the environments in which they live. Because of this, it’s necessary to have tools that allow applications to adapt so that they may function at their peak, no matter the traffic or security demands. And that customization may include modifications of how they encounter and handle traffic.
iRules is a powerful scripting language that's part of the BIG-IP system, that gives you the tools to enable programmatic analysis, manipulation, and detection of all aspects of the traffic in a network. It is routinely implemented for security mitigation purposes, to support new protocols, and to fix application-related errors in real time.
In a nutshell, iRules gives users the tools to create custom definitions of how BIG-IP processes traffic so they can tailor network traffic flows to meet specific business and application needs, ensuring efficiency and security.
Putting more tools in your hands with iRules in BIG-IP Next
BIG-IP Next expands on the iRules toolset by giving you better visibility, a more streamlined and resilient revision control process, and improved flexibility in the commit process.
Visibility is key in network management. That’s why providing detailed insights into iRule deployments was a priority for BIG-IP Next. In BIG-IP Next, you can monitor where and how an iRule is deployed to manage complex applications and ensure compliance with organizational policies.
Implementing changes can be a nerve-wracking process, especially with business-critical apps. In BIG-IP Next, you can take a tried-and-tested iRule and use it as a foundation to deploy a new or updated iRule, knowing that your new version is starting from a version that works rather than trying to build a new iRule from scratch.
Enabling faster revisions and a more streamlined workflow saves time and reduces the risk of errors. That’s why iRules now includes a new side-by-side comparison tool. Inspecting changes between versions is now as simple as queuing up two versions of an iRule and using the change finder to spot the differences.
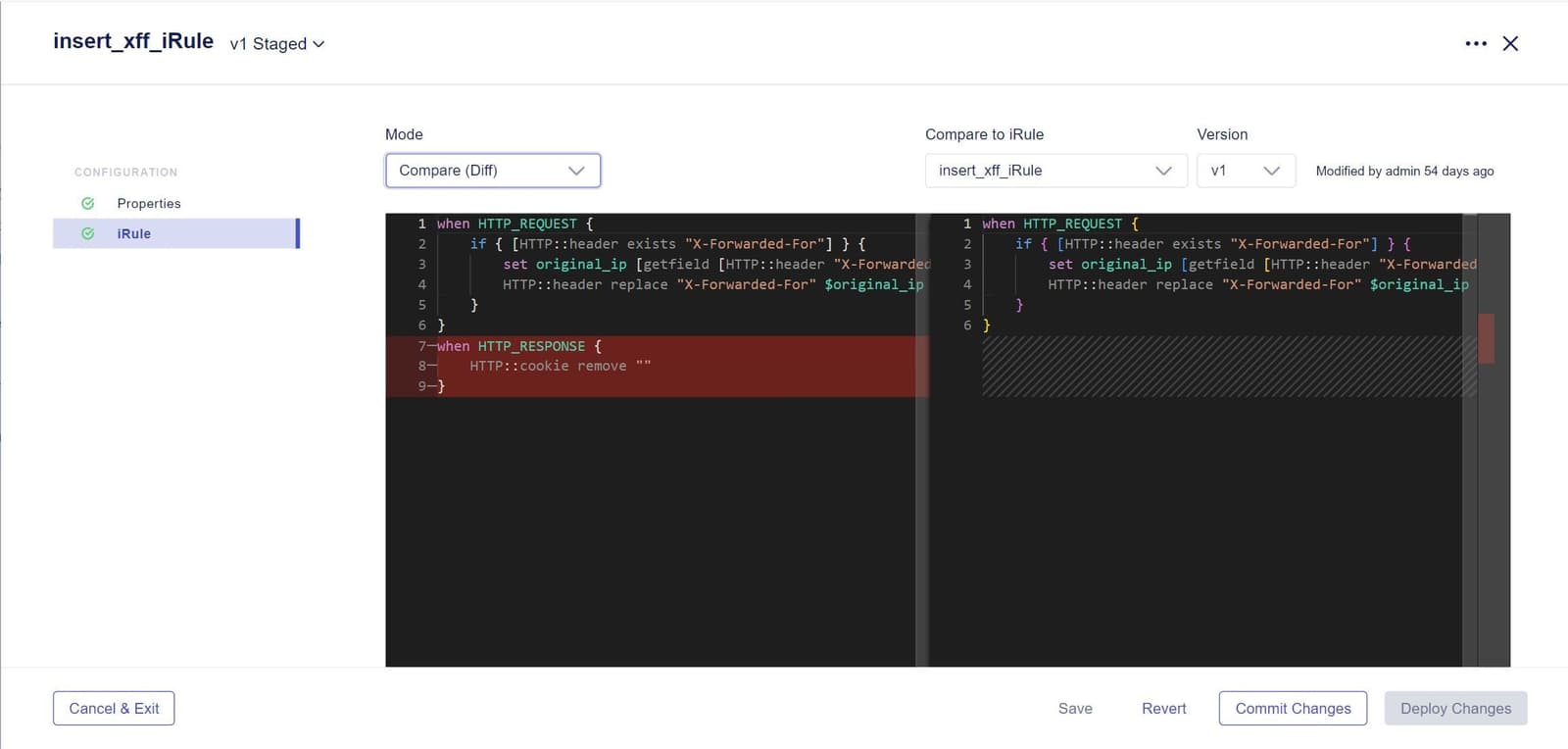
Mistakes are an uncomfortable truth about modern IT management. In BIG-IP Next, you can stop mistakes from having an outsized effect on your workflow. If an iRule update doesn't go as planned, a swift roll-back to a previous, stable version minimizes downtime and maintains the integrity of network operations.
Controlling the impact radius of a traffic flow change means reducing the likelihood that a scripting error knocks a critical app offline. With new commit options, implementing changes can be an incremental process, avoiding widespread disruptions for peace of mind and consistent application availability.
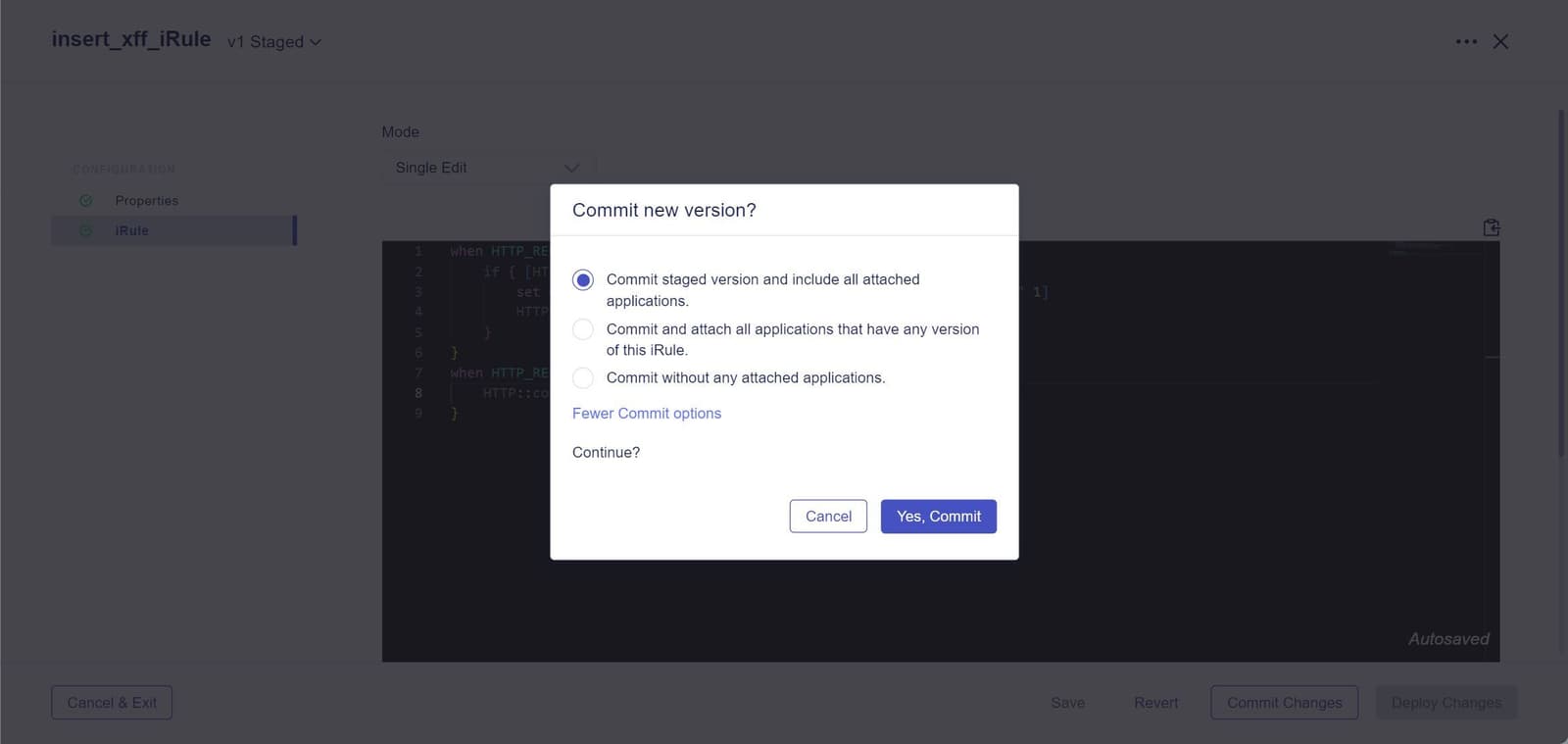
When we developed BIG-IP Next, we strived to enhance the flexibility, precision, and ease of use of iRules. The teams who use these solutions every day deserve tools that make their workflows less demanding and more effective. To learn more about how iRules in BIG-IP Next can make workflows less labor-intensive, read the solution overview or contact us.
To get a taste of iRules in action in BIG-IP Next LTM, try the demo.
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.

