Bringing Availability & Security Services to an Infrastructure-as-a-Service Environment
Dell EMC VxRail provides a proven virtualized environment for enterprises that want to consolidate workloads on a high-performance platform. As more workloads, including web-facing microservice applications, migrate onto the platform, infrastructure managers need to look beyond Infrastructure-as-a-Service. To support the growing list of workloads, they’ll need to look into services that ensure performance, security and availability for uninterrupted business operations. Taking an ecosystem perspective, our whitepaper focuses on F5 network application services that provide availability and security to web-facing workloads on VxRail. These application services use F5 software that seamlessly integrates into the VxRail VMware environment, making it easy to provision, configure and support F5 services via VxRail vCenter.
In the VxRail environment, infrastructure managers can consolidate applications from legacy and cloud platforms to create a single, integrated environment that is layered on top of the infrastructure for optimal operation. These capabilities could be offered as an integrated “as-a-service” environment to internal stakeholders, ensuring performance and cost efficiency, and enabling seamless extension to the public cloud via VMware Cloud.
Key topics outlined within the whitepaper:
This section focuses on using the vCenter management interface to provision and deploy F5 Advanced Web Application Firewall (Advanced WAF) software onto VxRail. For this example, we have created two web servers hosting a sample workload and have deployed Advanced WAF in front of the servers. The example was designed with the objective of optimizing and protecting the web-facing workload residing within the web servers.
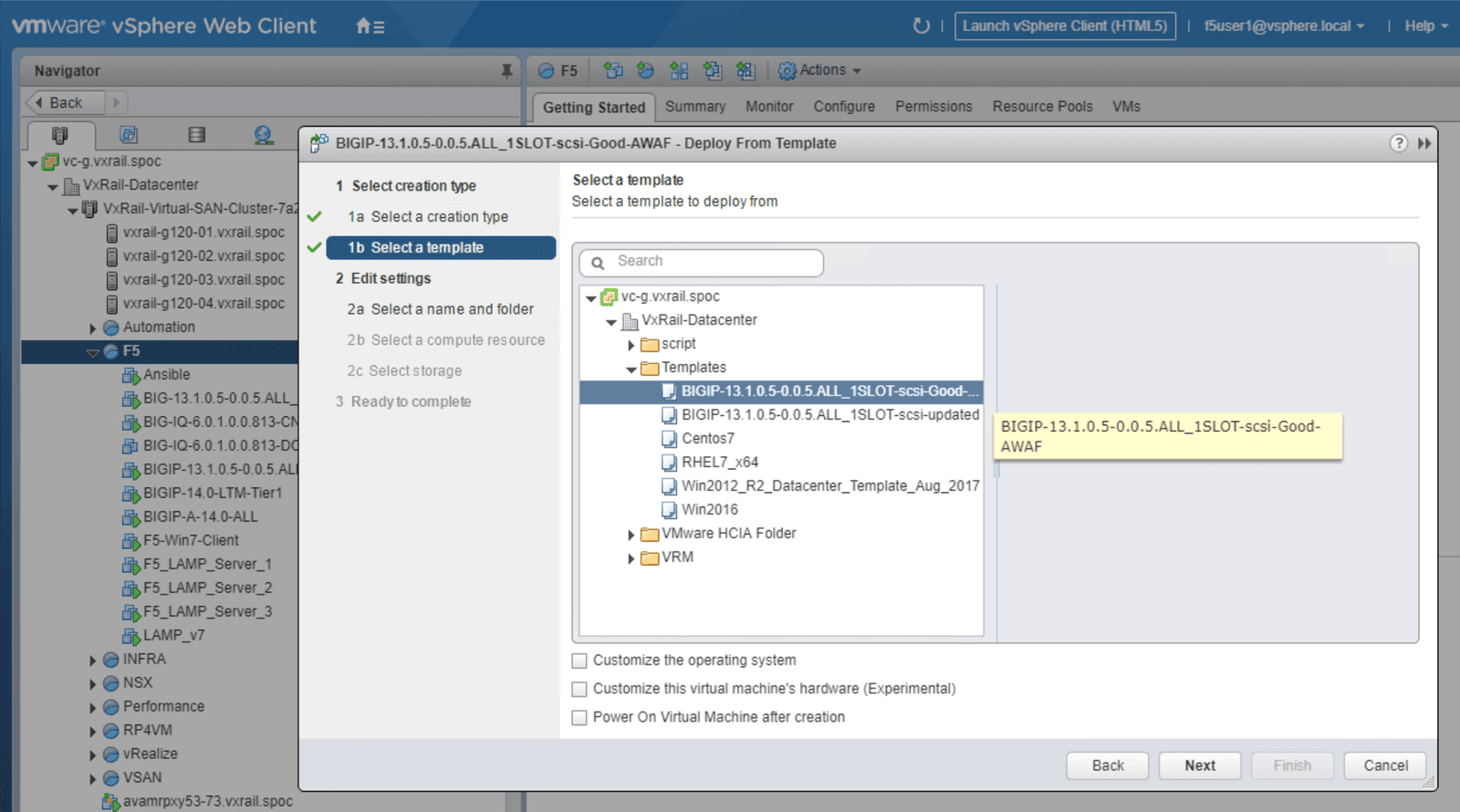
Start by creating an Advanced WAF template within VxRail vCenter, as shown in Figure 1. The Advanced WAF template should be listed in the template folder in VxRail-Datacenter. The template stores the image of the Advanced WAF; the template can be used to launch the application service in the future, allowing for easy service creation.
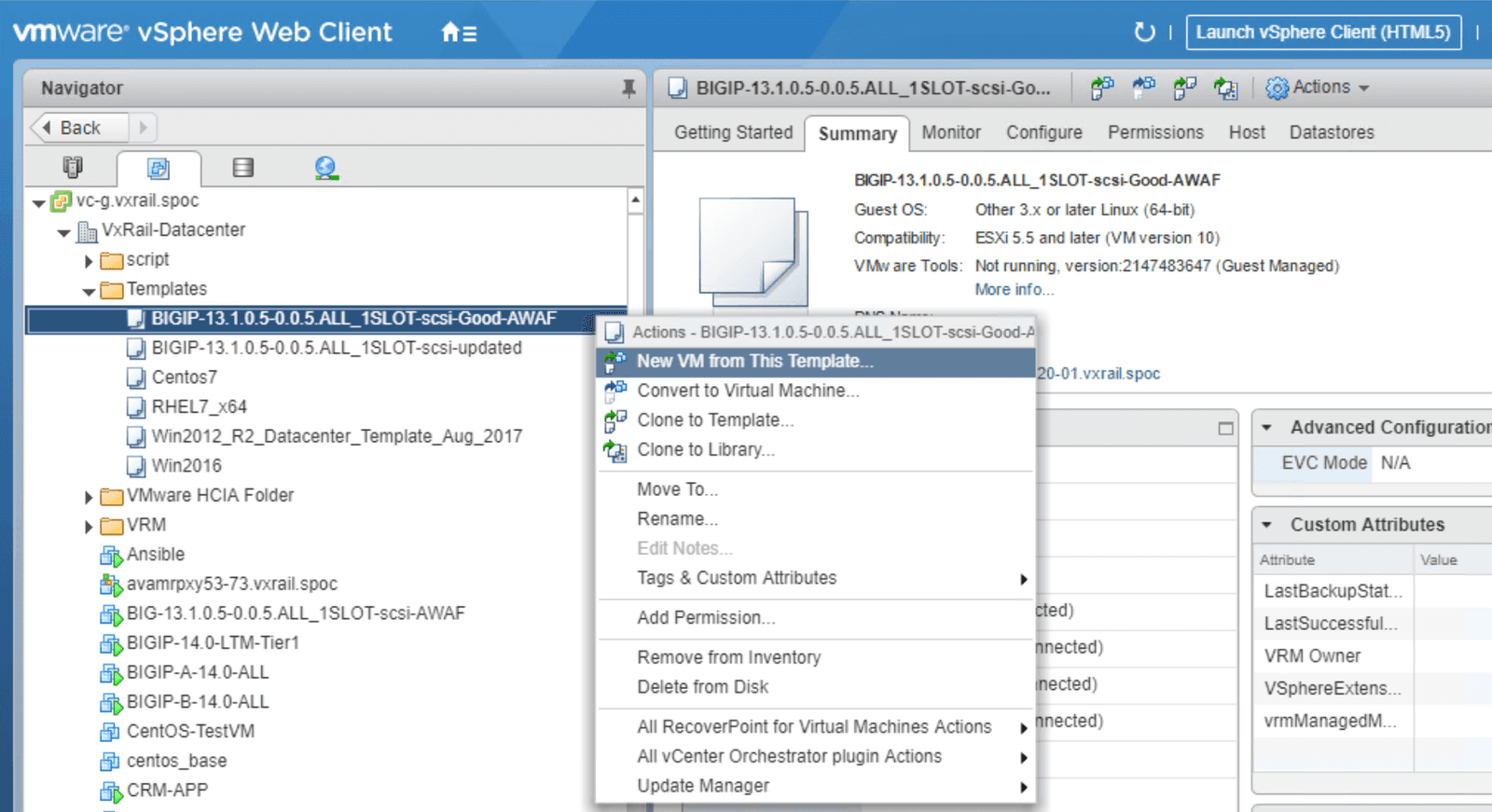
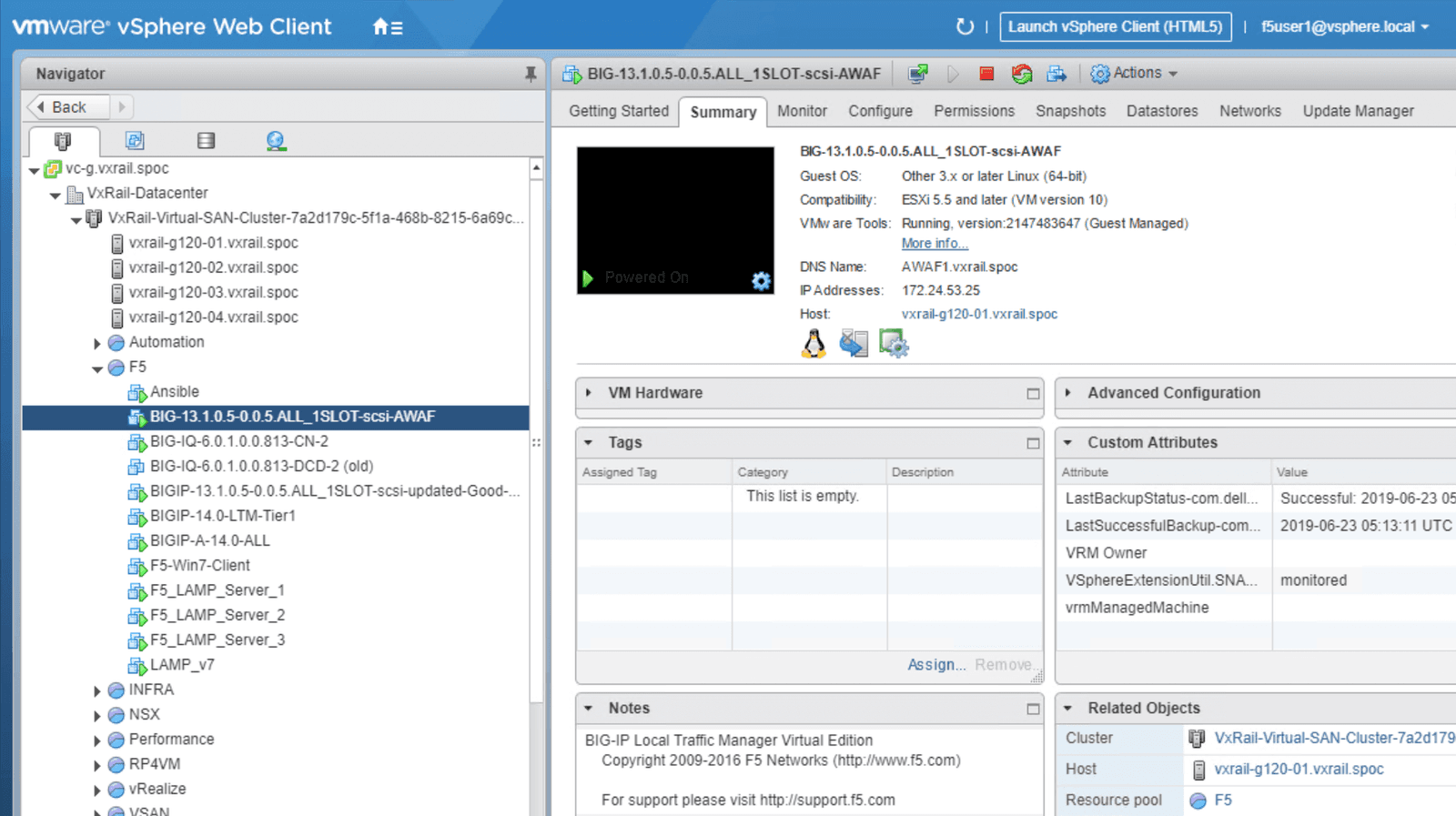
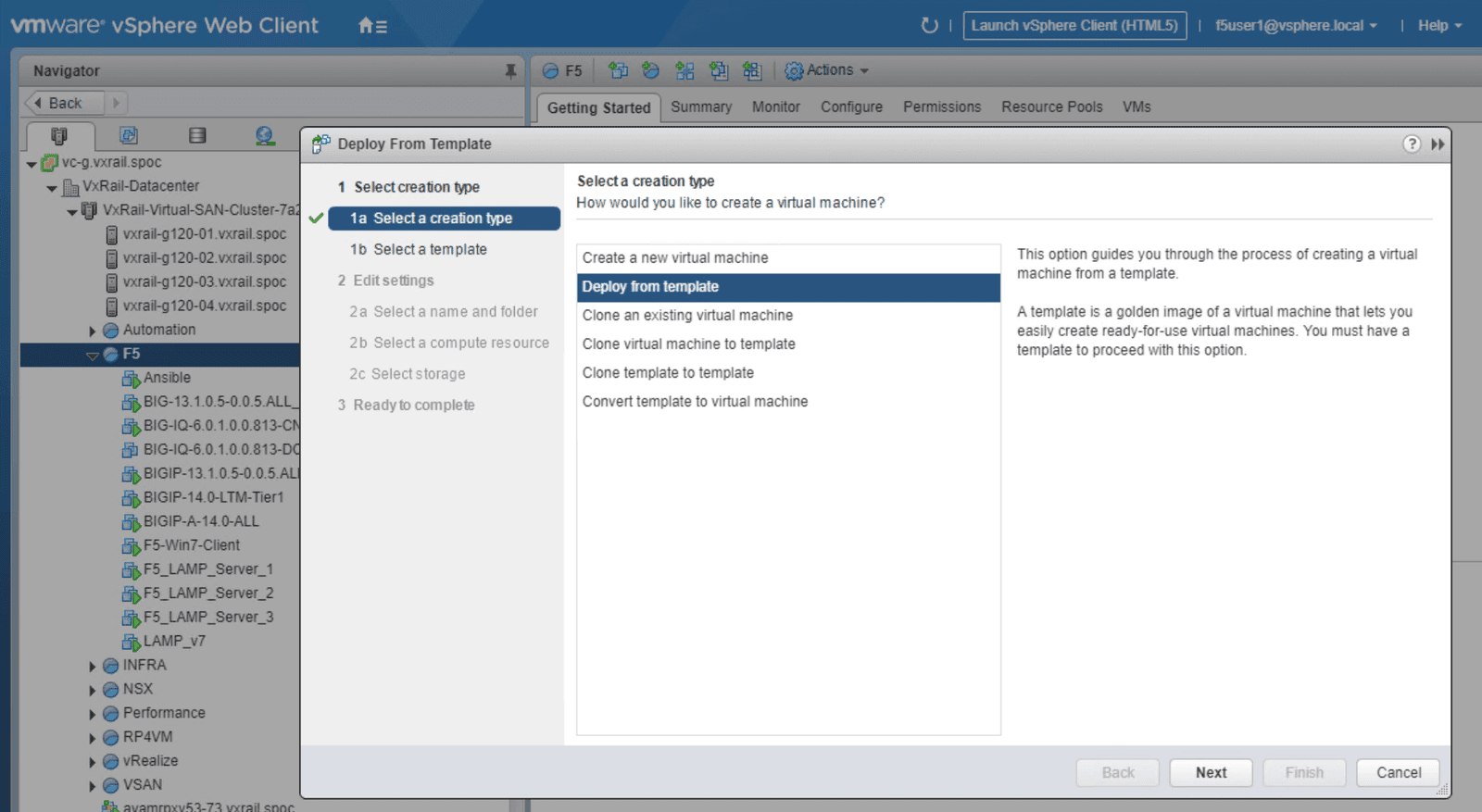
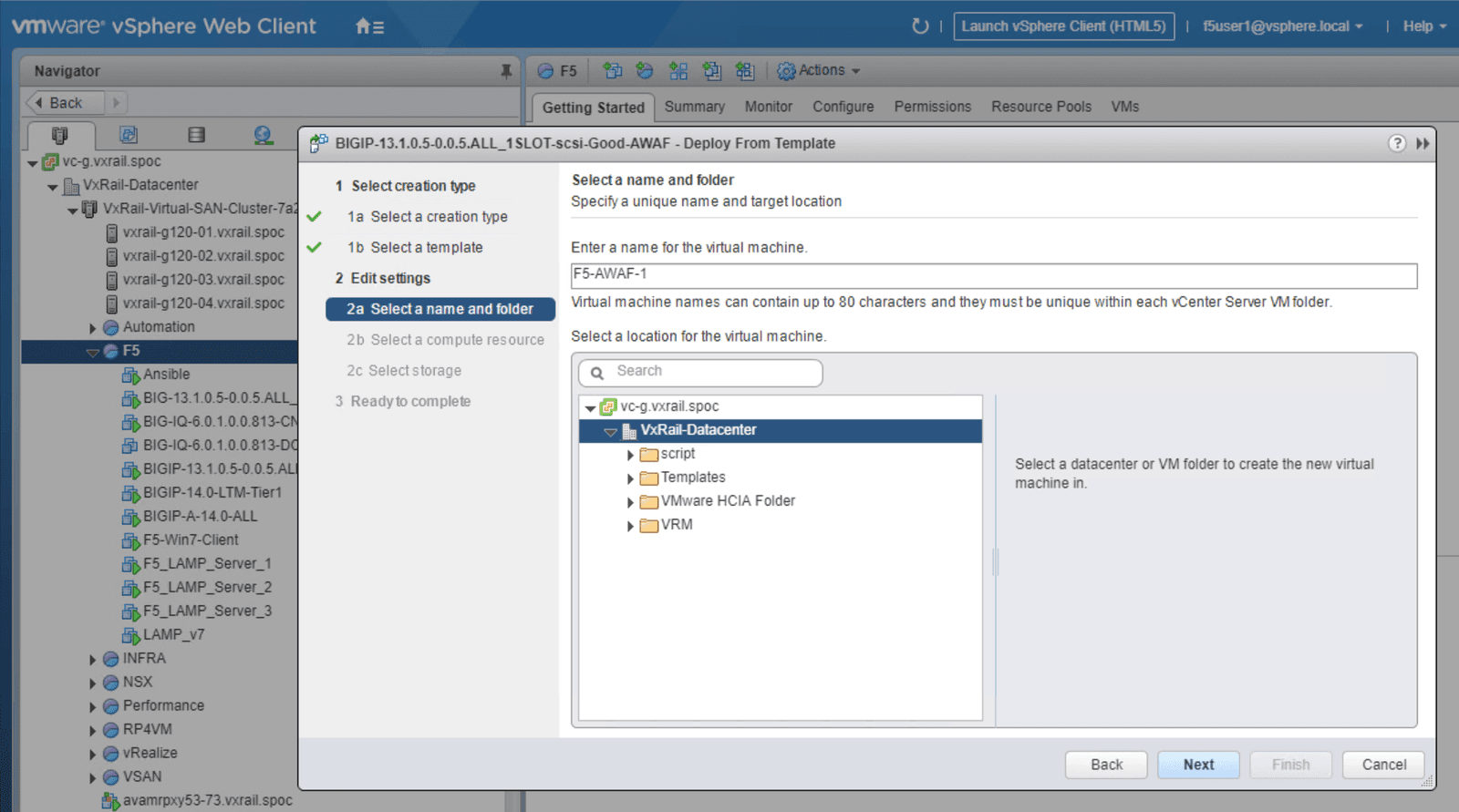
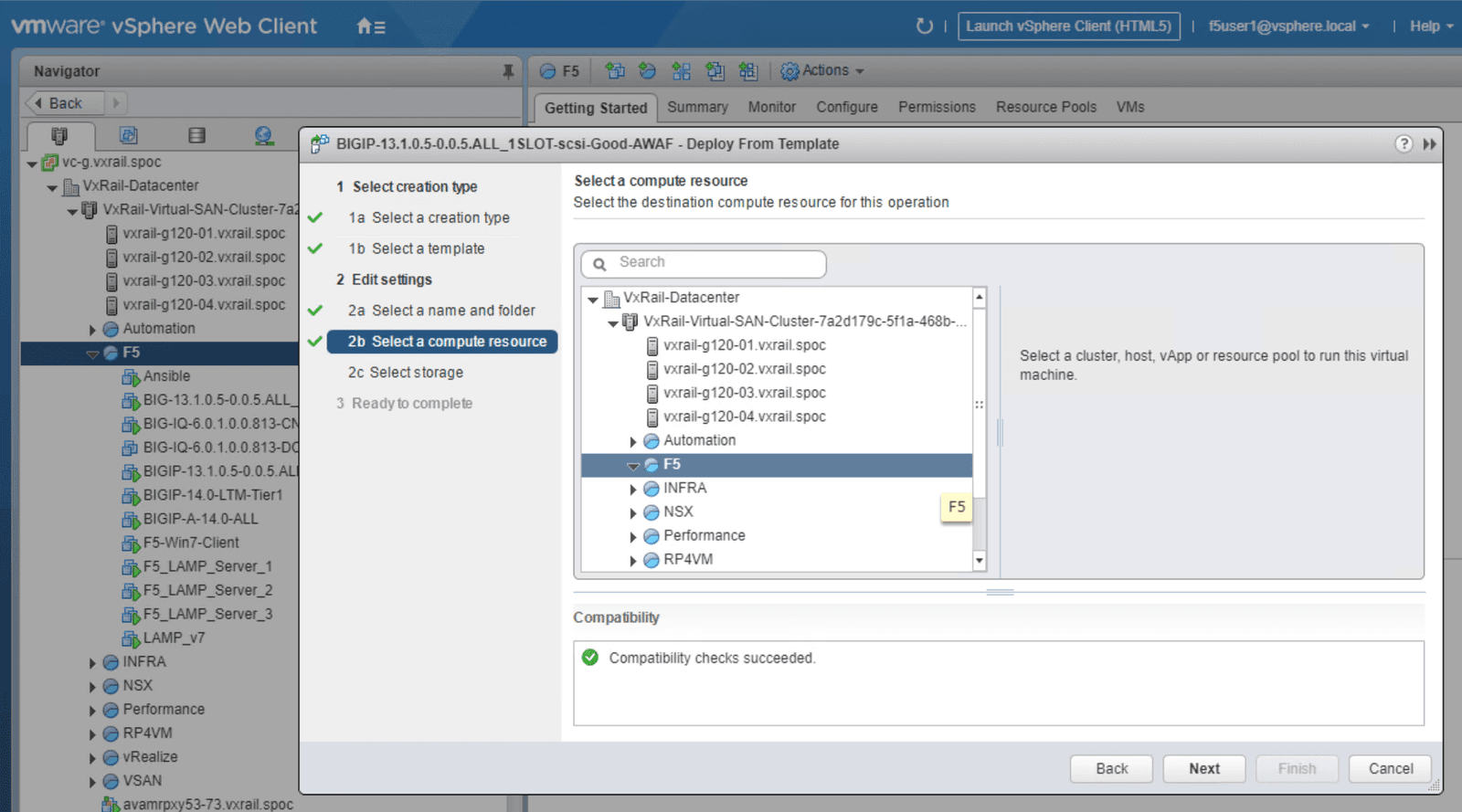
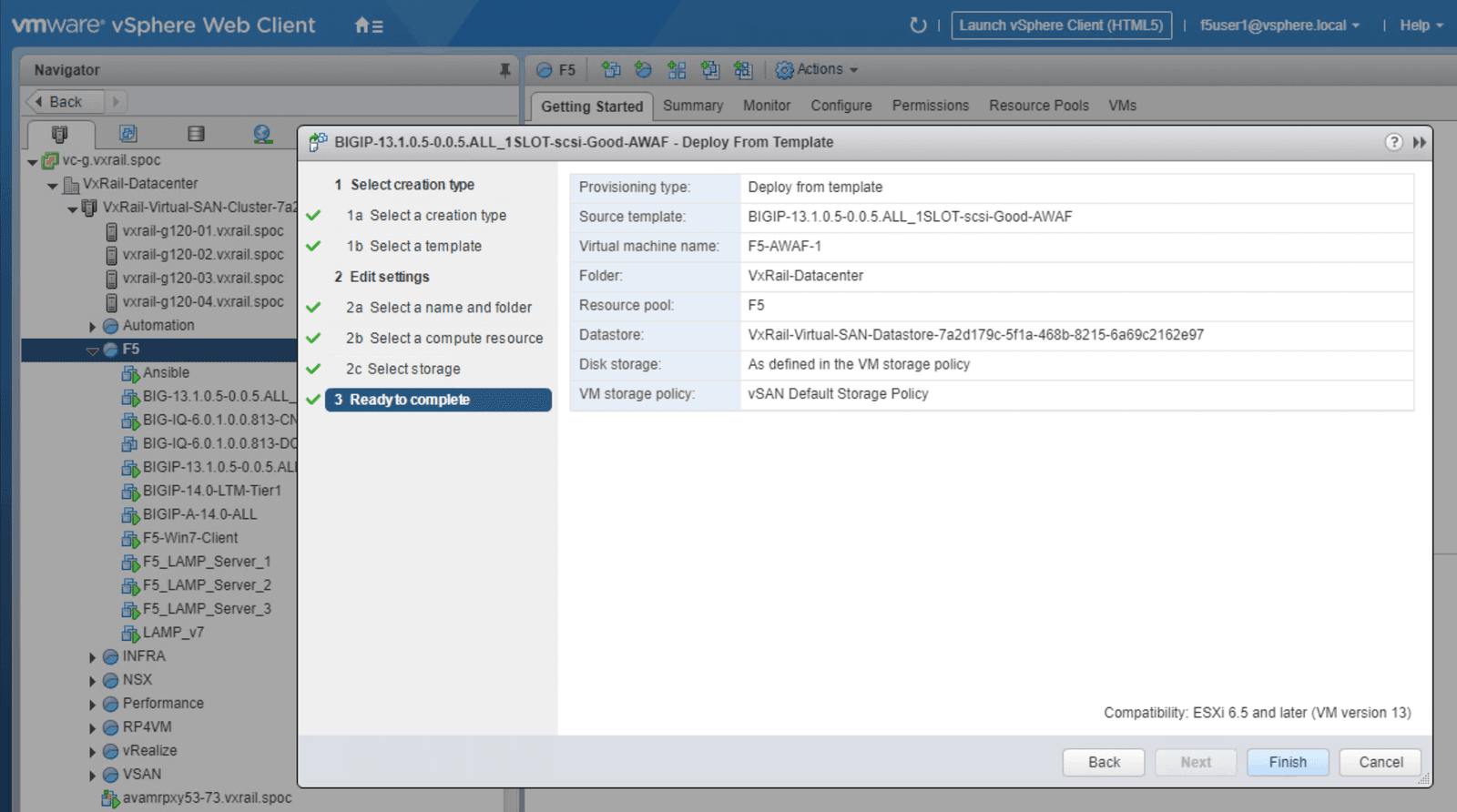
Click on the Advanced WAF template as indicated in Figure 2. From this menu you can launch a new VM, then prepare the services to be used, referring to the steps outlined in screenshots below as needed. We have included individual screenshots of each step to simplify the deployment process.
To ensure a smooth deployment, be sure to follow these guidelines:
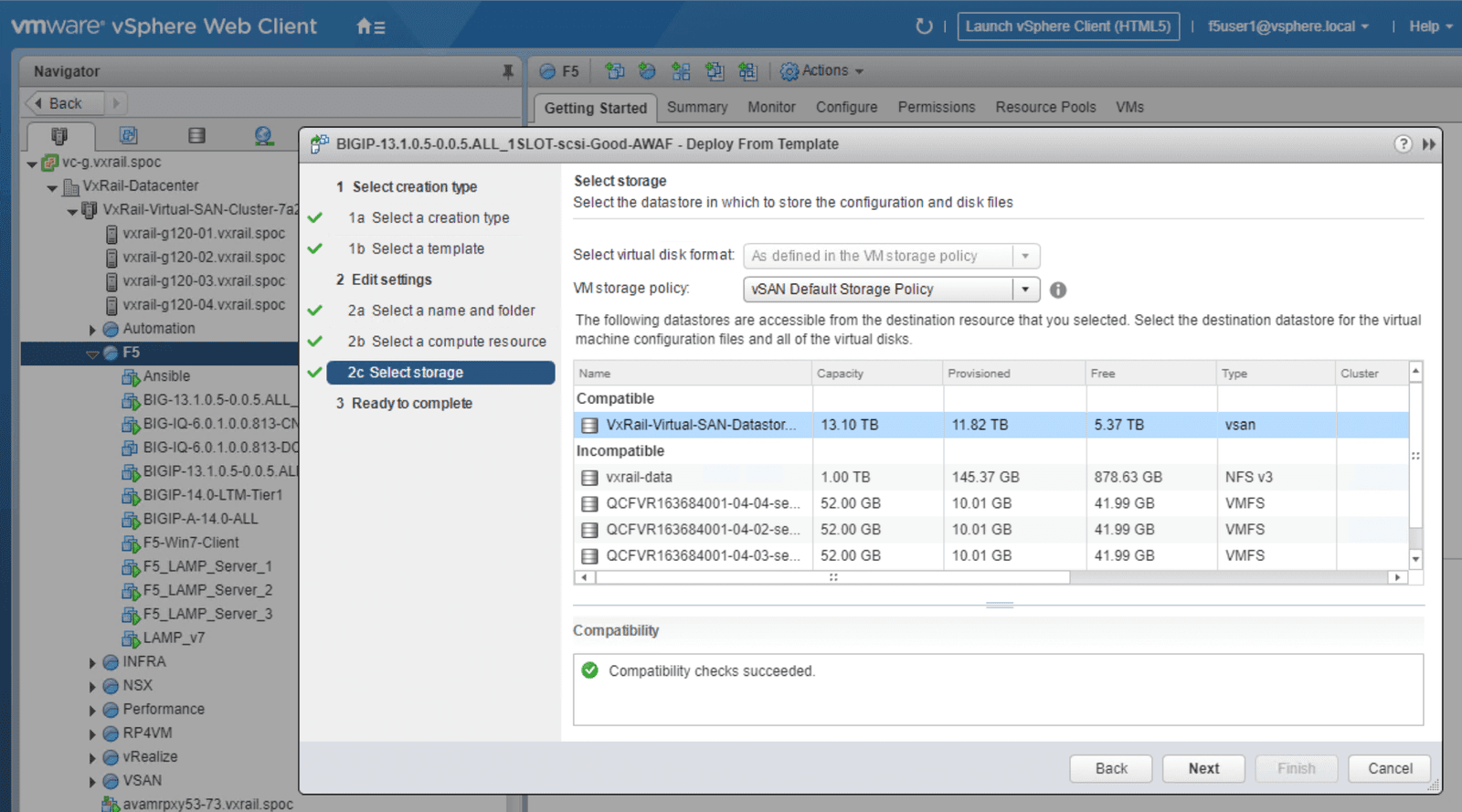
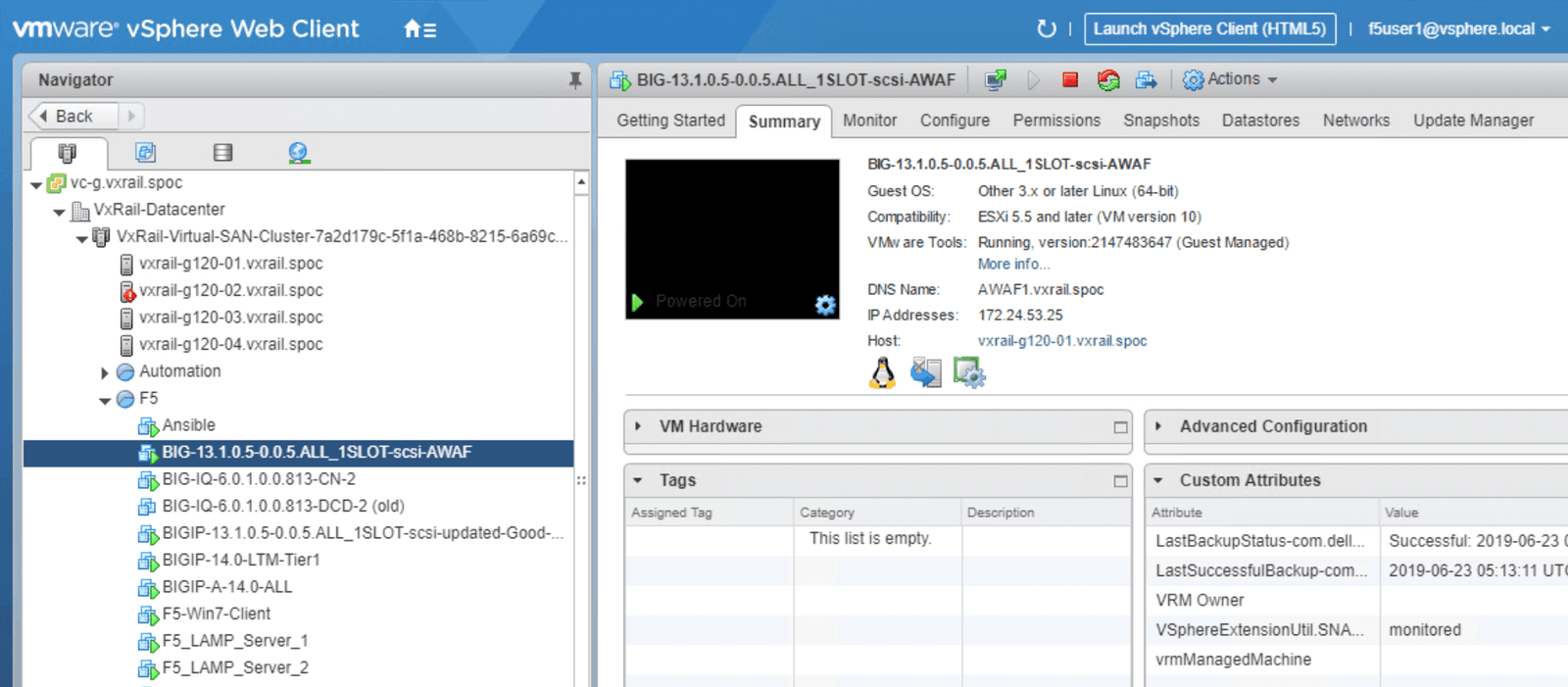
When you have finished the configuration process, you should see Advanced WAF deployed on the VxRail cluster with the IP Address specified in the summary page, including pre-assigned compute resources and storage. See Figure 3 for an example of a successfully configured deployment.
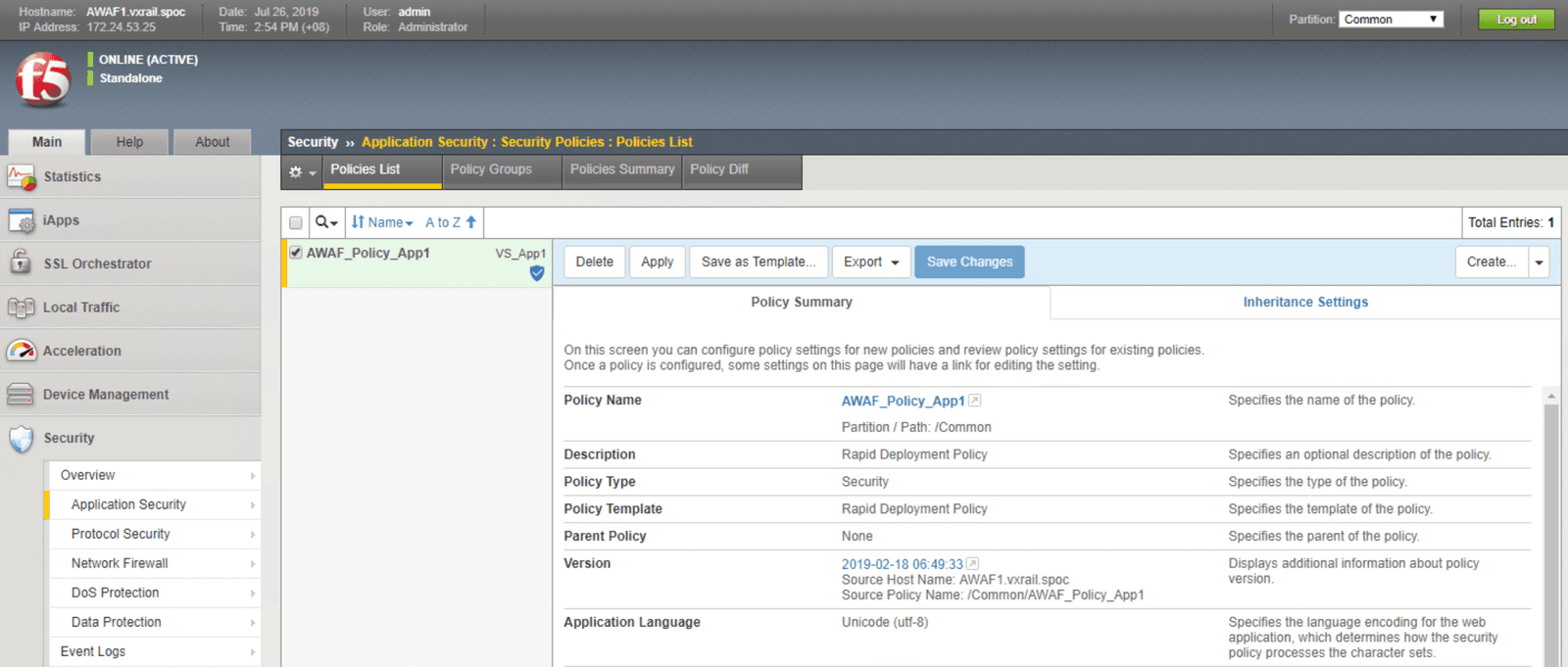
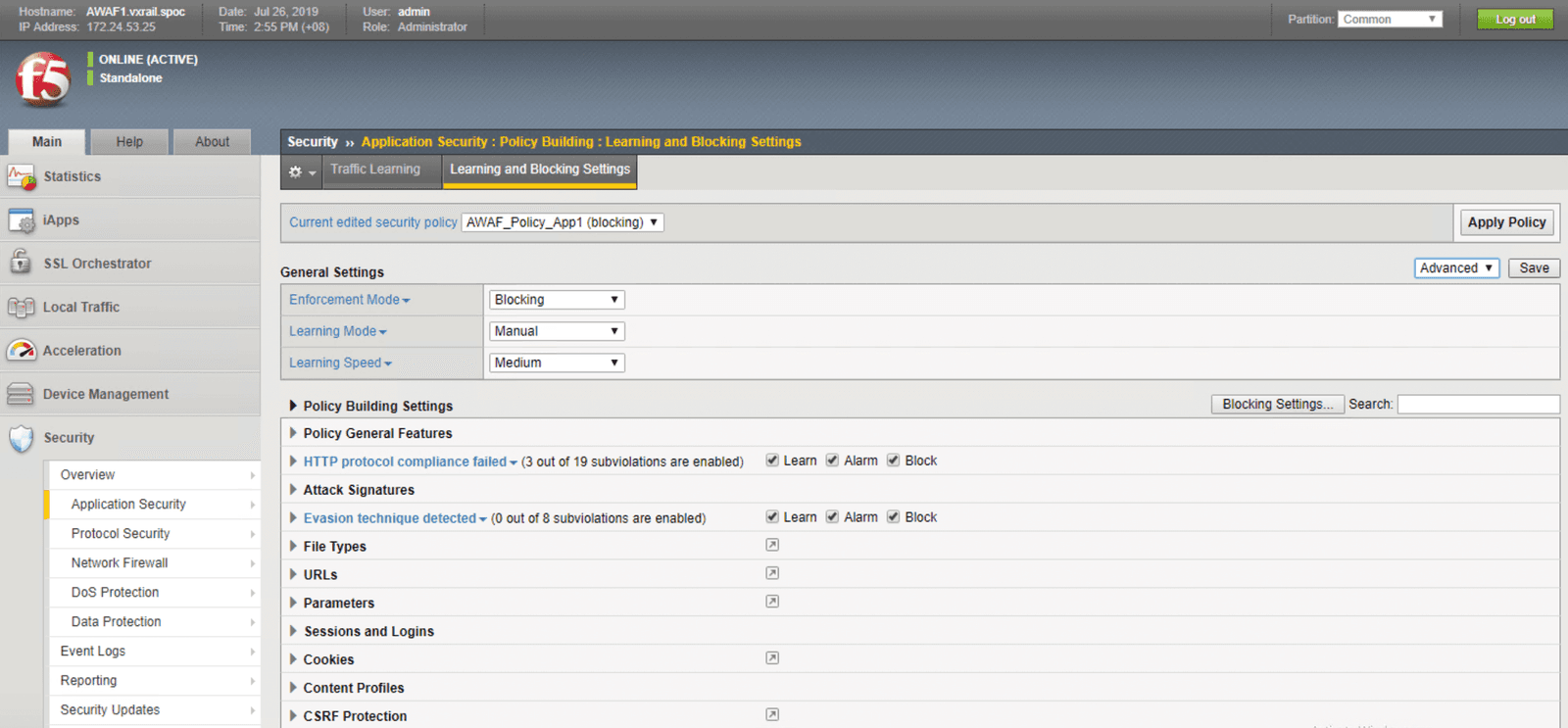
Once the Advanced WAF software has been deployed, we can define the security policy that should be used to screen incoming traffic before it is passed the webservers. Advanced WAF empowers users to craft their own granular security policies, and also includes extensive libraries of threat intelligence and signatures. These libraries are frequently updated to include the most timely security information This enables users to create workload-centric security profiles that are supported by the latest threat intelligence. Users may also choose to enable “listening” mode. This mode uses machine learning to establish an environment-specific baseline security policy, thereby reducing unnecessary alerts triggered by false positives.
BIG-IP High Availability is supported by TMOS, allowing the resiliency methodology and supports to be consistent throughout all product modules.
The figures below will walk you through the steps necessary to configure your system for high availability. These steps include:
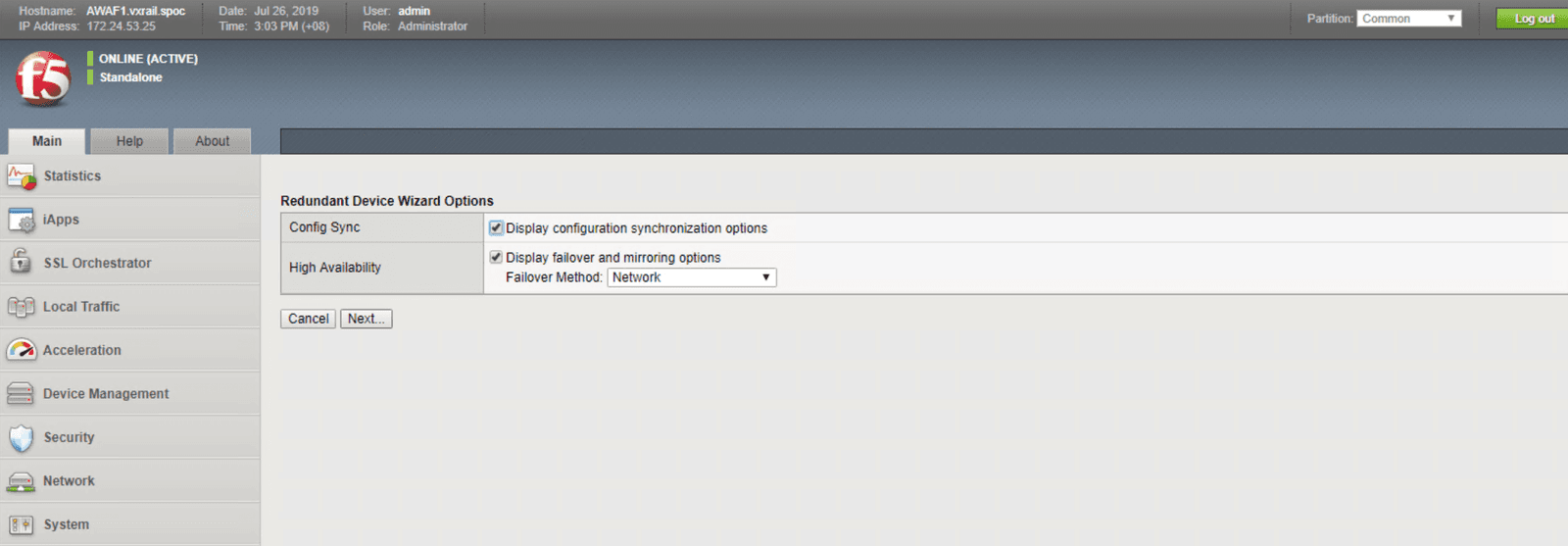
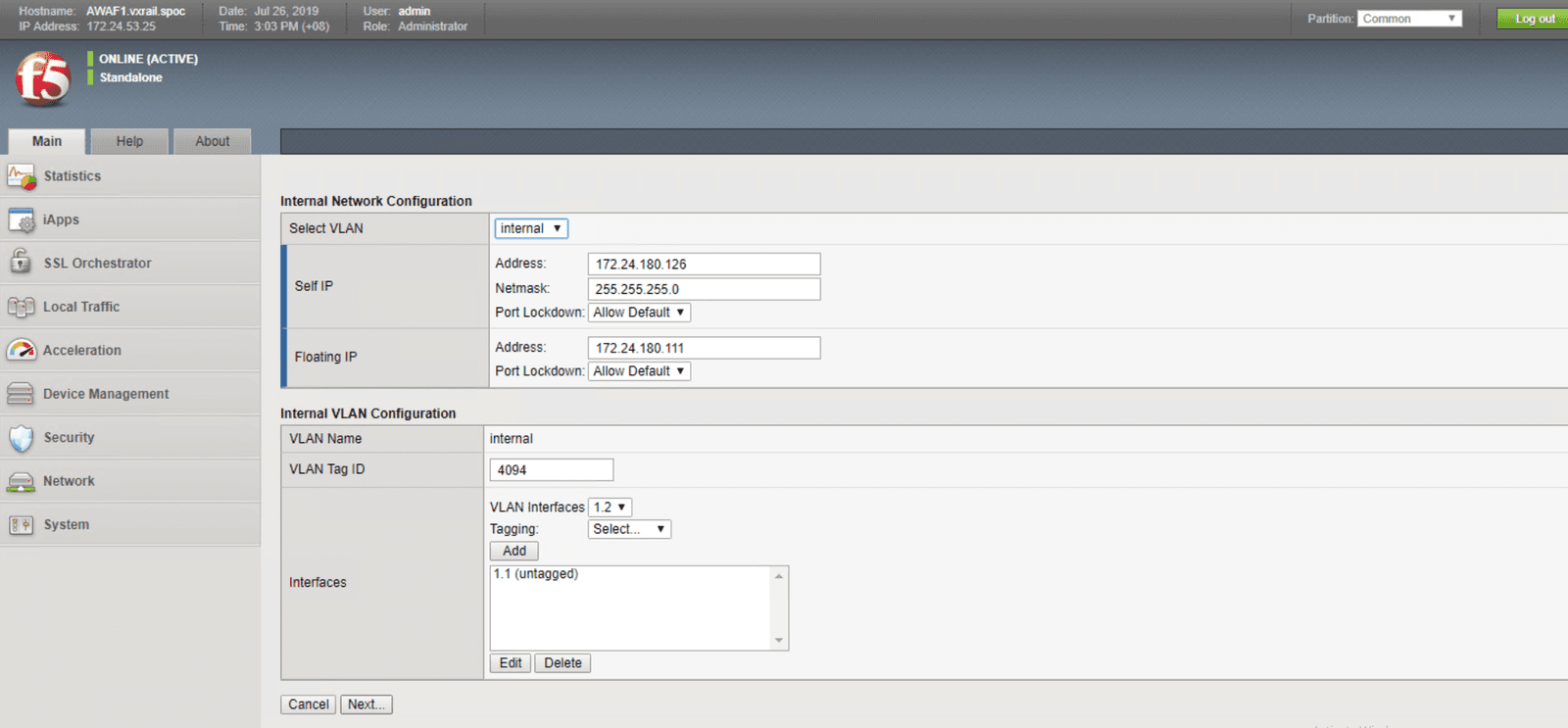
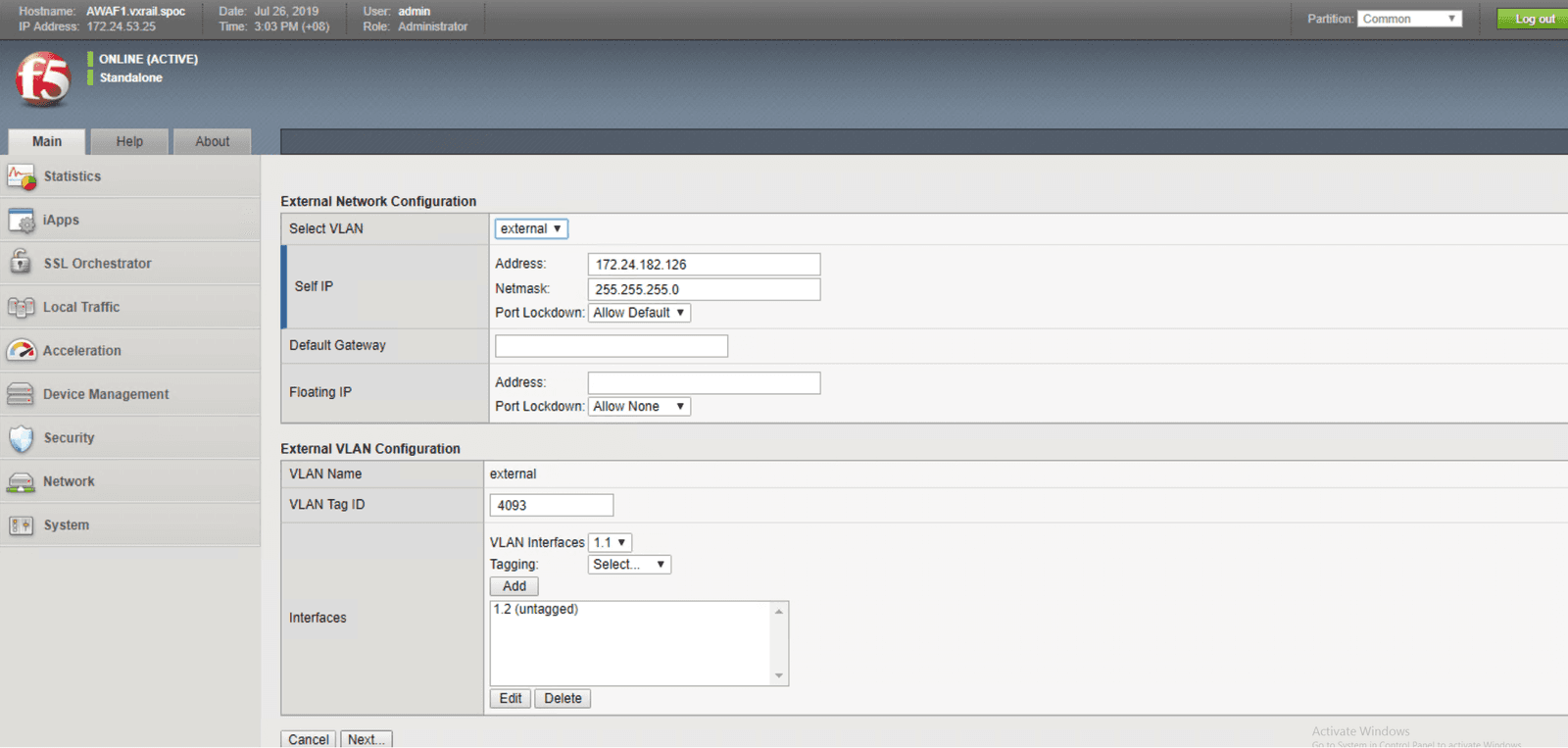
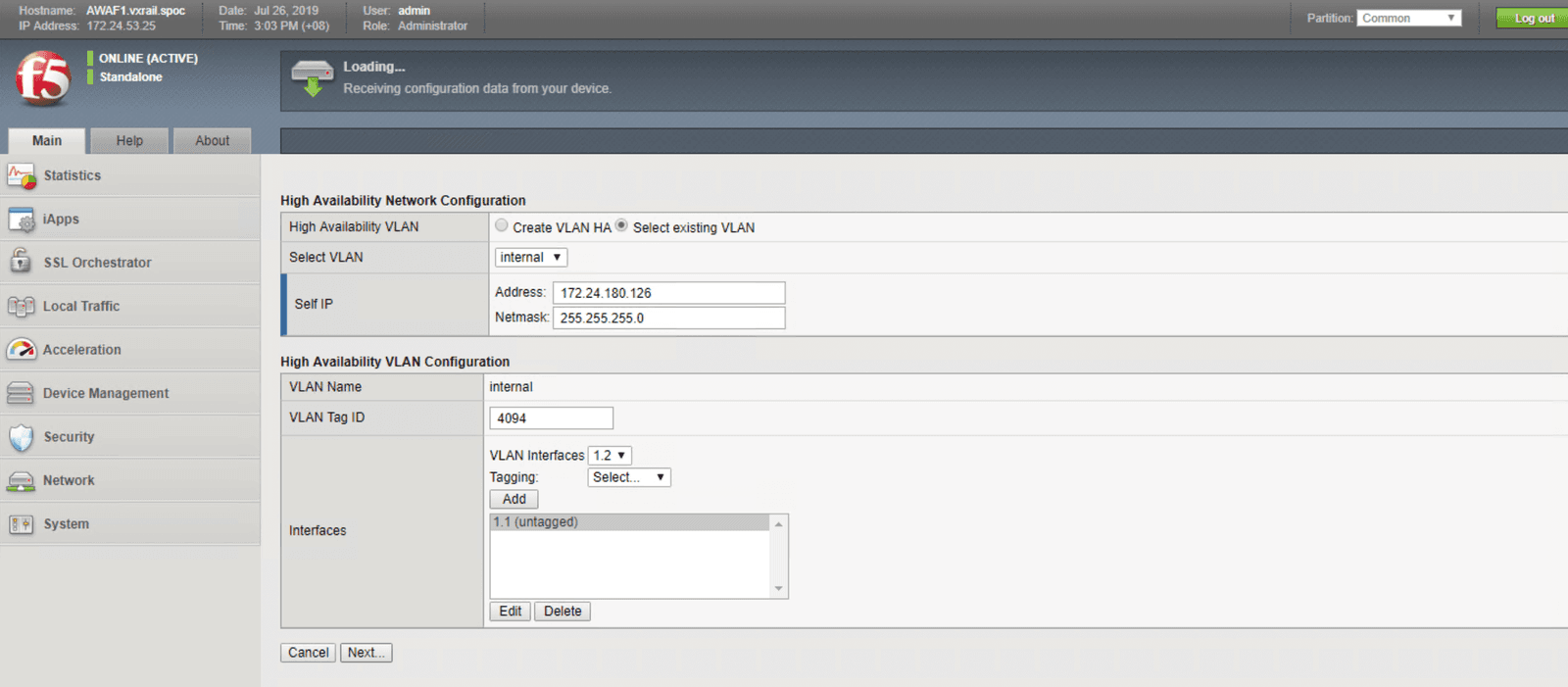
In this section, we use two security features, user credential projection and SQL injection blocking, to illustrate how to implement protection for web-facing workloads. In lieu of a step-by-step guide, we created a that shows how these security features work block out intrusions and threats automatically, keeping the workloads and back end infrastructure safe.
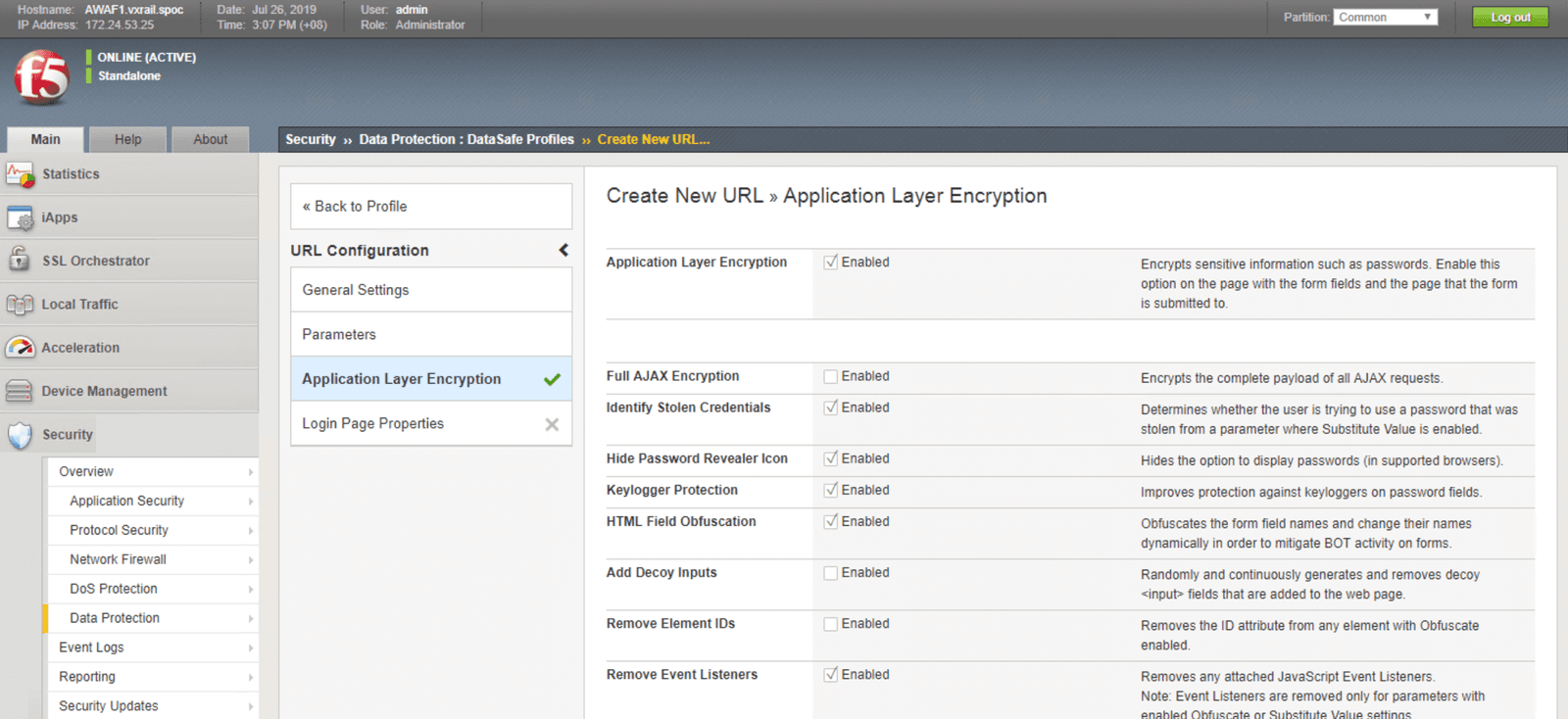
Data Safe allows user credentials and parameter names (for example, ID and password) to be encrypted and obfuscated at the application layer in real-time. No coding changes or adjustments to the application source code are required to implement this security service.
For web-facing assets or applications with HTTP/HTTPS traffic, data encryption with SSL is the first step toward protecting the data against potential exposure to an unlawful third party. SSL encryption during transfer is not enough to ensure data security. Credential theft could also occur at the client level; for example, end users may have compromised their web browsers by clicking on harmful files or accessing malware-infested sites.
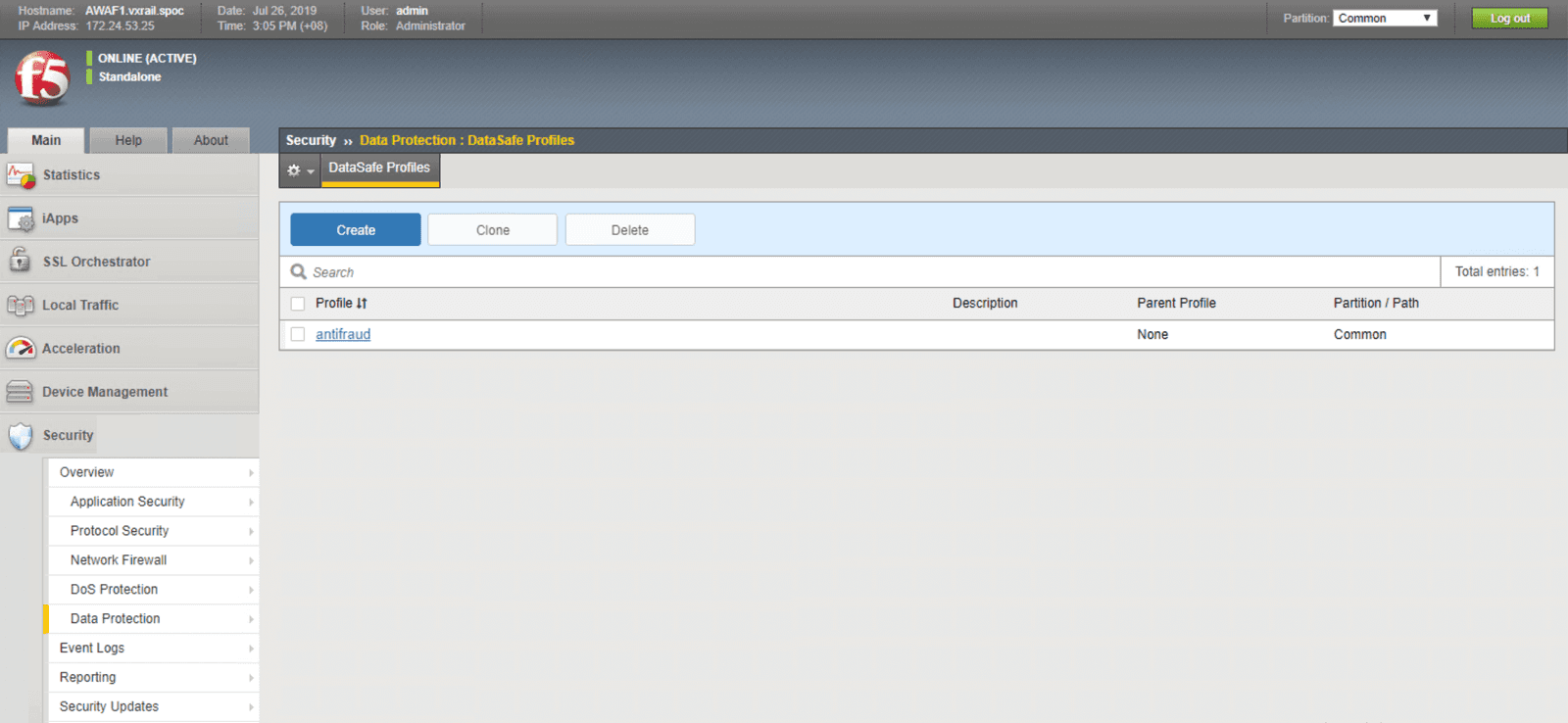
The Data Safe feature can be enabled via the Security section on the Advanced WAF console. Select data protection, then proceed to Data Safe profiles:
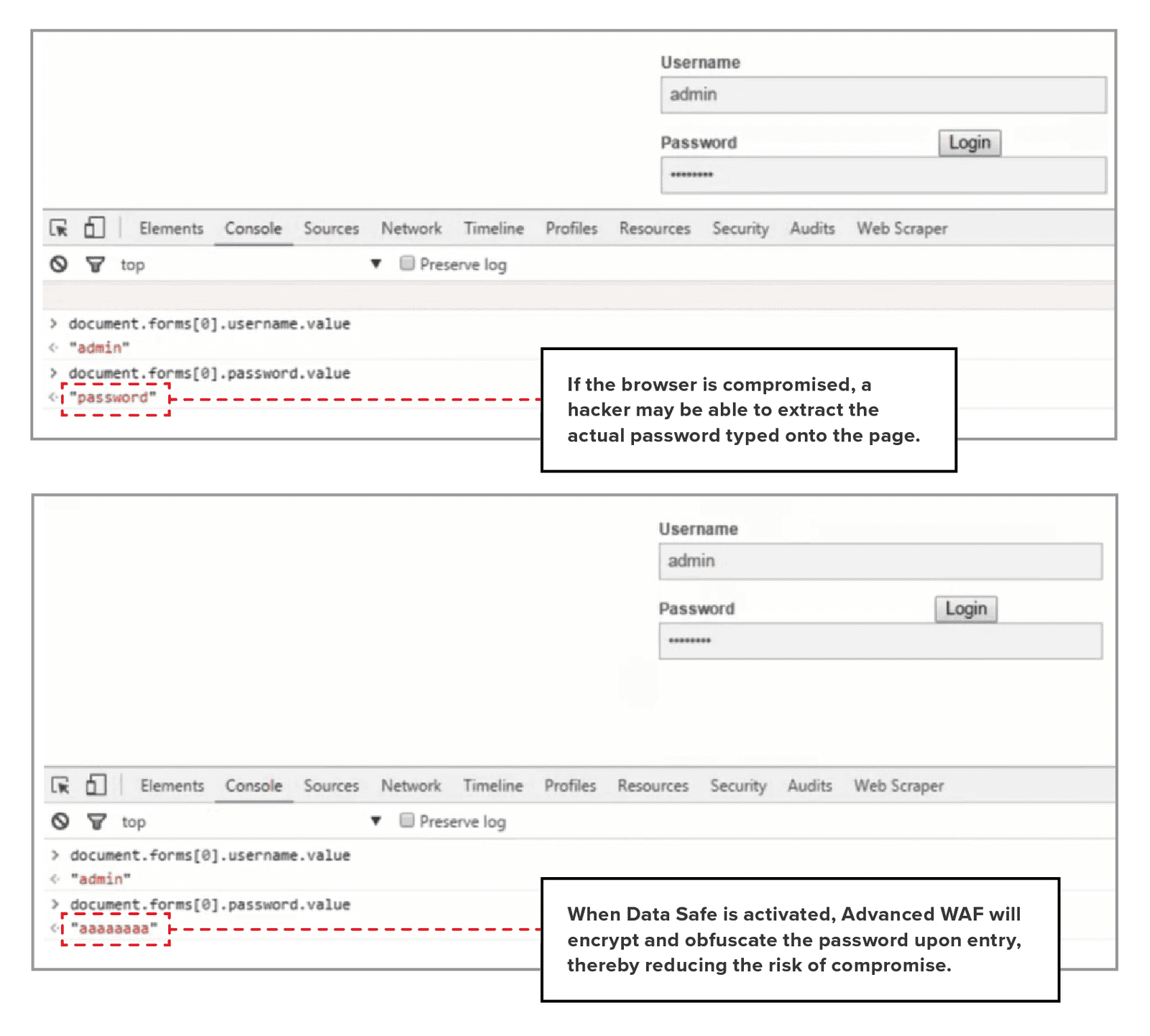
With Data Safe enabled, you can set the criteria to encrypt ID and password at the client level for web-facing assets or services. This reduces the risk of a security breach due to malware-infected browsers. Applications that are protected by Data Safe present web pages via Advanced WAF. ID and password characters are encrypted as they are entered by the user. Even if a browser is compromised, the malware will only be able to extract the encrypted data, which cannot be decrypted without the private key, rather than the actual password (See the illustration below for more details). In addition to client-side web-layer credential protection, Advanced WAF can be upgraded to include mobile-layer protection for workloads from mobile applications.
Part A: User credential protection
Part B: On SQL injection
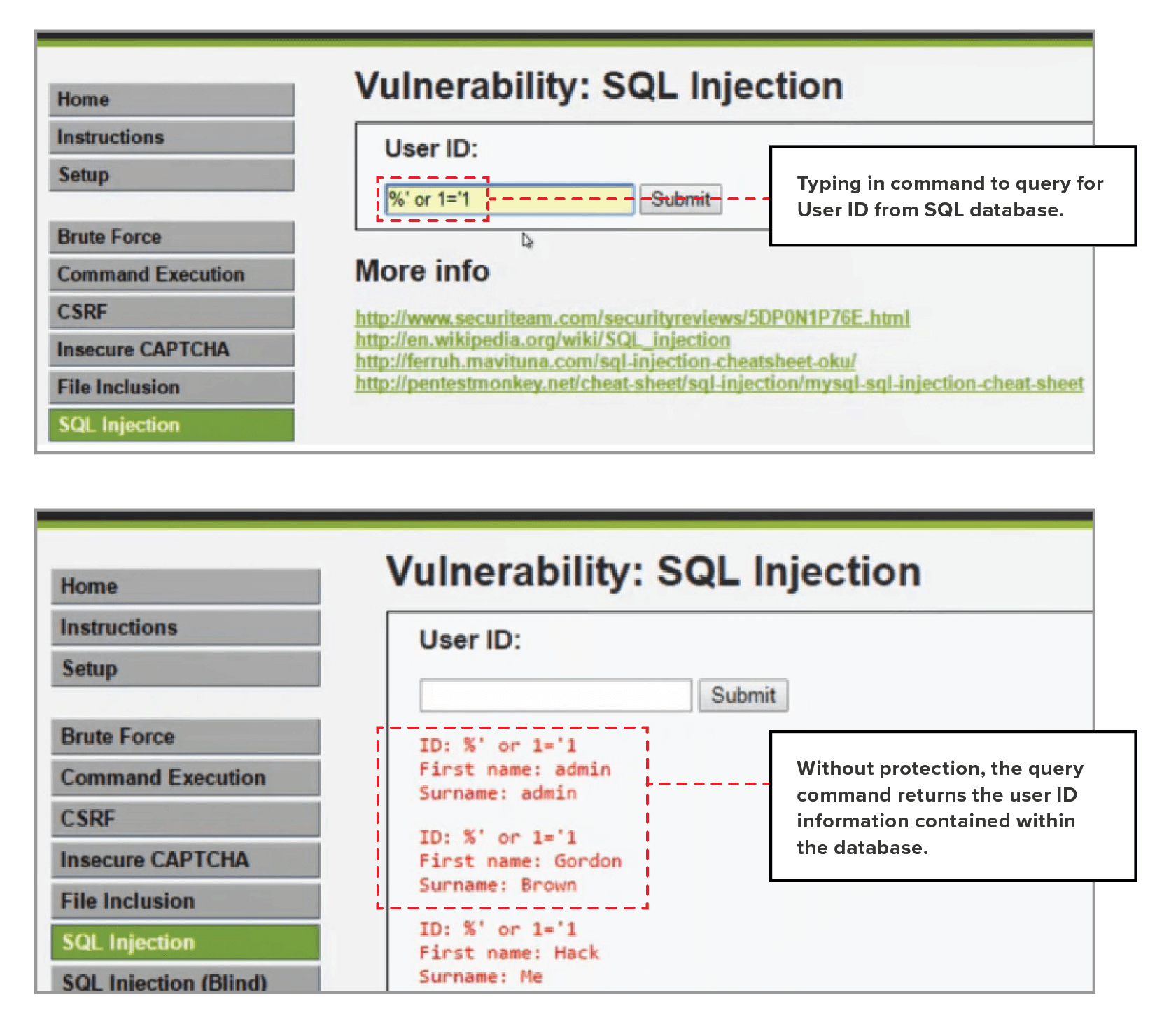
SQL injection always ranks highly on the OWASP Top 10 Threats list. Hackers look for vulnerabilities within application code to find opportunities to extract essential data from the back-end database. The first step to reducing the risk of compromise by SQL injection is to promote coding best practices to ensure “safe-n-secure” coding. You can also apply an extra layer of protection within your infrastructure. Advanced WAF incorporates extensive threat intelligence and includes a library of threat signatures, which can be deployed to safeguard the web-facing workloads from SQL injection.
To enable protection against SQL injection, access the Attack Signatures section from the Application Security menu, and use SQL as the filter keyword. You’ll see list of SQL injection-related signatures within the threat signature database. At the time when this demo was completed, there were 563 related signatures available to protect against SQL related attacks. Select all the relevant threat signatures and add them to your application security policy.
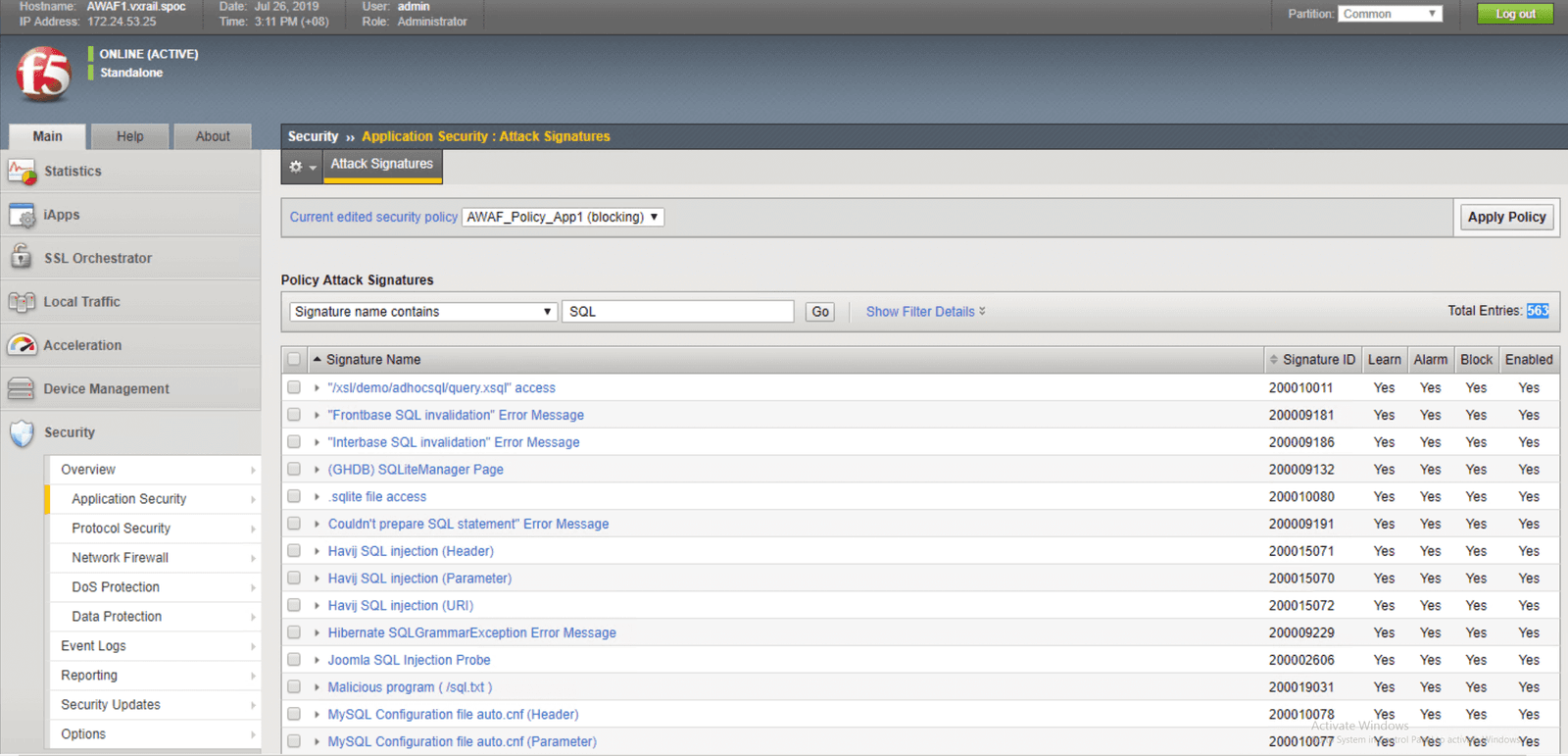
To illustrate the difference, the following figures show the results with and without SQL injection blocking.
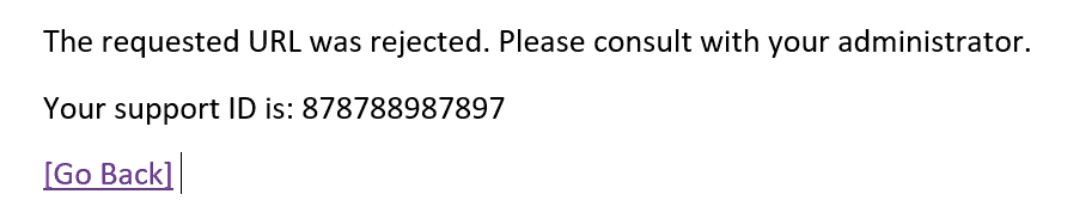
With protection, the query is blocked, and an error message like this one is returned instead.
With SQL injection activated, SQL queries are blocked before they reach the database. The would-be hacker receives an error message instead.
VxRail offers a scalable, easy-to-manage environment that enables users to easily deploy, test, and integrate F5 services. In this section, we focus on the usage details of Advanced WAF, demonstrating how to access a full report of its current state (for example, CPU and memory utilization), and showing how this information can be used to plan for future expansion. Our goal is to ensure F5 software is built to support the ‘as-a-service’ model of VxRail.
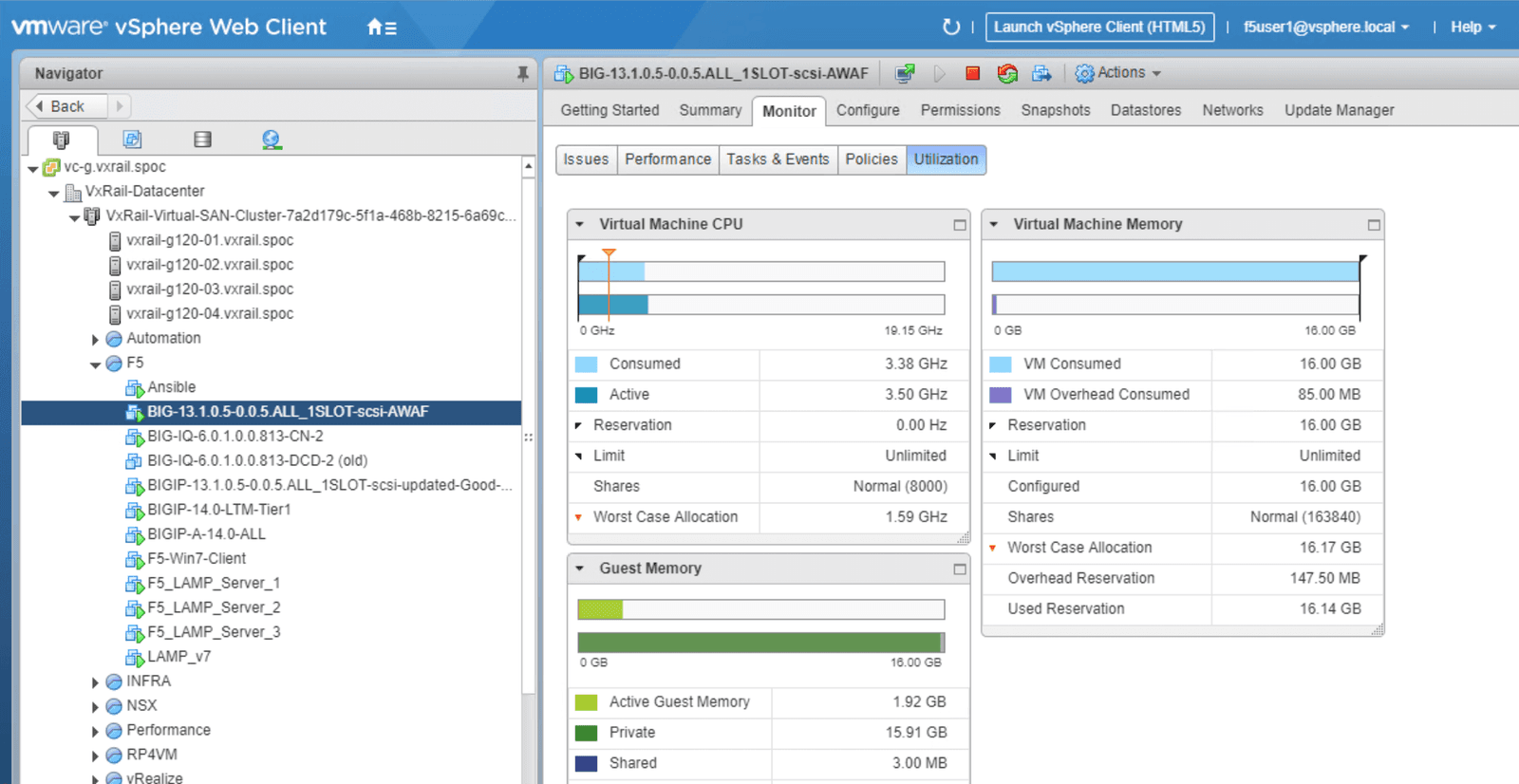
As outlined in Figure 22, within VxRail vCenter, we can have granular visibility of the Advanced WAF Virtual Appliance usage level. From here, users can access details of the Advanced WAF VM, including:
For this Advanced WAF demo, we’ve created 2 web servers (LAMP Server 1 and LAMP Server 2) that are used to illustrate usage scenarios in which Advanced WAF optimizes and protects web-facing assets residing within VxRail.
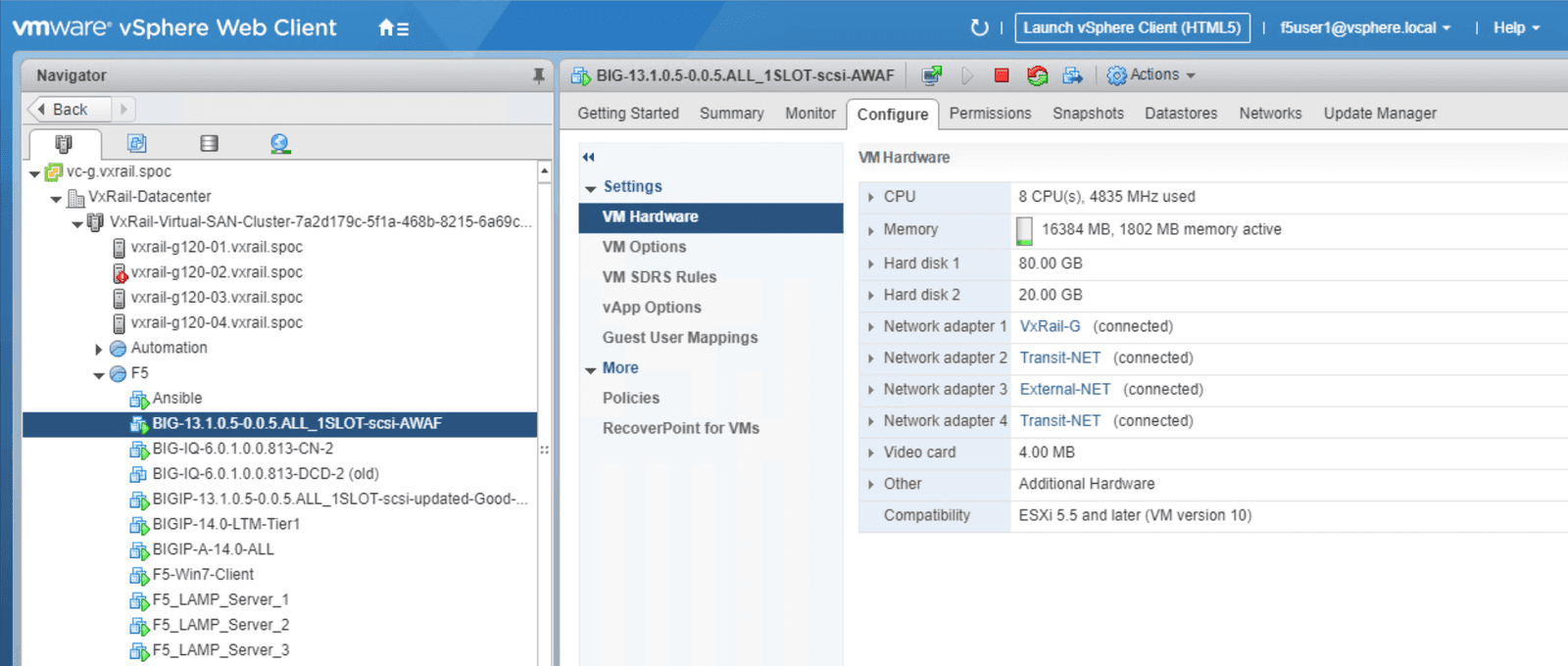
The figures below show the resources allocated to our services, giving readers insight into the resources used for the demo. This allows infrastructure managers to estimate the capacity needed to scale up these services for a production environment. This information may be particularly useful if these tools will be used in a scalable as-a-service environment.

In this whitepaper, we have shown how to set up the F5 Advanced Web Application Firewall (Advanced WAF) within the VxRail environment. We walked through a step-by-step deployment guide, illustrating Advanced WAF security features using before and after comparisons.
This document demonstrates how to deploy third party software on the VxRail environment by setting it up as a service that infrastructure managers can integrate and offer in a service-rich environment. We showed how to configure Advanced WAF in the VxRail environment to provide application security services for web-facing microservices-based applications.
VxRail is a high performance, scalable, easy-to-manage platform that can be used by infrastructure managers to drive business operations. Deploying third party services that ensure a good user experience is critical to business success. F5 Advanced WAF provides seamless support within the VxRail environment that can be extended to the VMware Cloud.
PUBLISHED AUGUST 03, 2020