The growing number of connected devices in the Internet of Things provides an opportunity for service providers to develop new streams of revenue. To fully capitalize on this opportunity, service providers must architect secure and agile networks that offer connectivity, security, and an optimal customer experience.
The explosive growth of the Internet of Things (IoT) is driving an ongoing digital transformation toward a "connected society" where technologies such as wearables, traffic control, and smart homes and businesses will be ubiquitous. Gartner forecasts that there will be 20.8 billion connected devices worldwide by 2020. The fifth generation of mobile networks (5G) will be a key wireless technology supporting the continued evolution of the IoT.
The IoT will create value by delivering seamless and consistent services that can redefine business models and remove boundaries across industry verticals, including manufacturing, shipping/asset tracking, energy, connected homes, connected cars, and healthcare. Service providers have the opportunity to create new revenue streams by driving efficiencies and improving the way services are delivered across different sectors. They can improve services through the analysis of intelligence they gain from data collection.
To accomplish these goals, service providers will need to deliver on tough requirements such as an ultra-low latency data path for certain use cases and prioritize each IoT device with its corresponding applications. They face tremendous pressure from both regulatory bodies and end users and must build networks and services to offer the seamless, scalable, and secure IoT experience that regulators and end users expect.
For end users, the IoT has the potential to provide solutions that can dramatically enhance productivity and quality of life in security, health, education, and many other areas.
Service providers can take advantage of this opportunity to deliver value to end users if they can create solutions that improve decision-making and productivity in an agile and cost-efficient manner. To monetize these IoT opportunities, service providers need to focus on providing consistent connectivity as well as capturing real-time actionable insights to transform customer engagement and build around the needs of their end users.
The value of service providers lies in their ability to establish themselves as "solution integrators" that build secure and seamless platforms in collaboration with their ecosystem partners. Through the integration and delivery of solutions that meet end users' high expectations for valuable content and user experience, service providers can advance the vision of the connected society—and grow their business at the same time.
IoT Challenges: Priorities, Concerns, Security
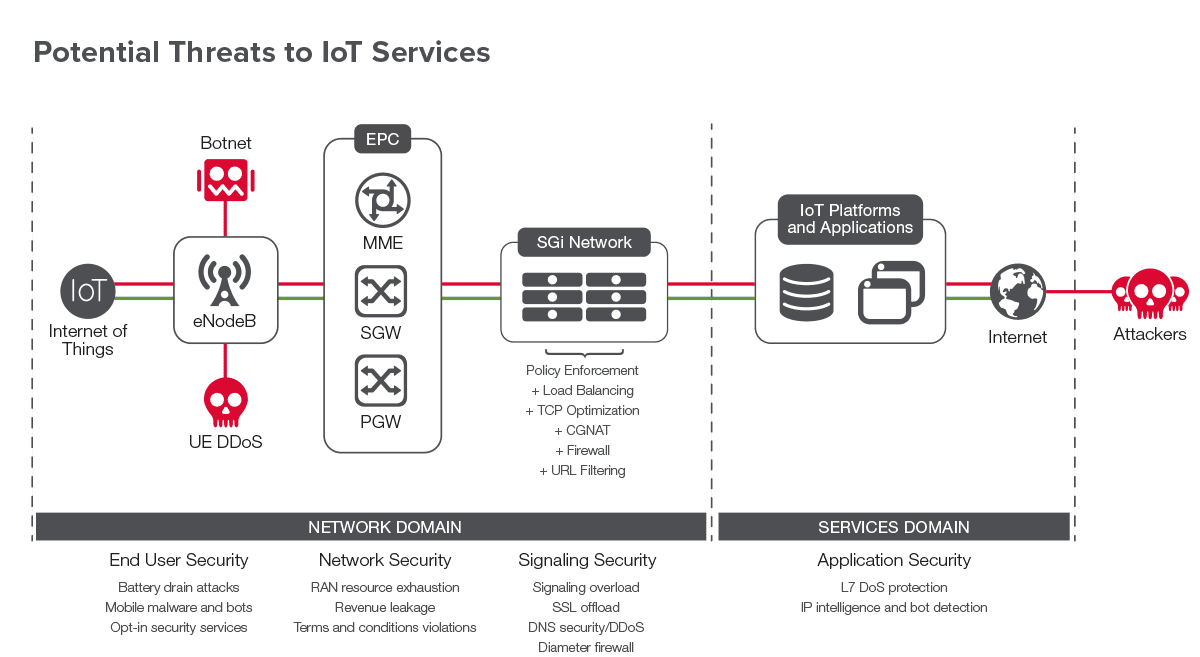
The large number of diverse devices connected to the network will increase network vulnerability and potentially become targets of hacking and denial-of-service attacks.
The requirement to handle possibly billions of DNS requests per second, for example, may impact network performance and availability for many service providers. IPv6 network addressing for IoT devices and backwards compatibility with IPv4 applications is essential to support so many new devices.
In addition, DDoS attacks and advanced persistent threats (APTs) could have devastating effects on network availability. The increased number of applications and services will open up new and unknown threat vectors that could expose service provider assets, degrade service availability, and, most importantly, damage reputations and brands.
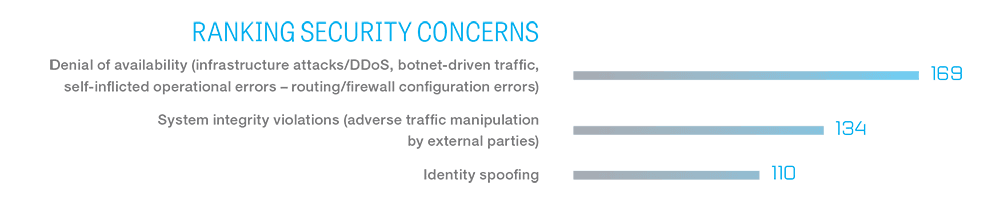
In a February 2016 survey and report on The Future of Mobile Service Delivery, Jim Hodges, senior analyst for Heavy Reading, revealed global service providers' priorities and concerns and explored how they can address security while preparing for a 5G/IoT world.
Hodges pointed out that the top security concern for service providers is outages caused by DDoS and botnet attacks. This fear is followed by threats related to system integrity in which traffic is manipulated by external attackers while spoofing a user's identity.
Service providers recognize that security threats exist across their network domains, with the top area of concern in the data center. But they also understand that devices, the RAN, the EPC, the IMS, and the Gi-LAN must be protected to ensure seamless, end-to-end network security.
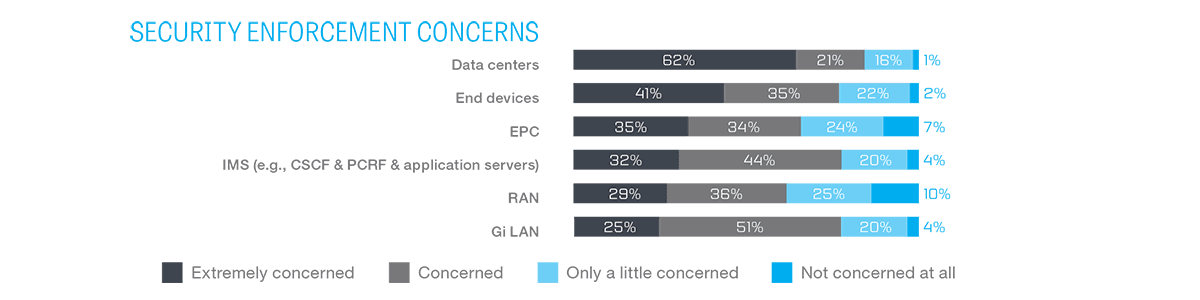
Because the number of connected devices is always increasing, service providers are still learning about the security requirements and challenges of the IoT and 5G networks. Safeguarding DNS remains a key part of any security strategy; almost half of survey respondents believe that DNS attacks are a growing concern.
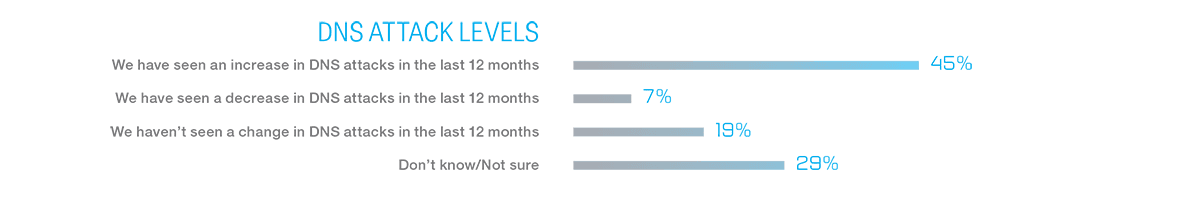
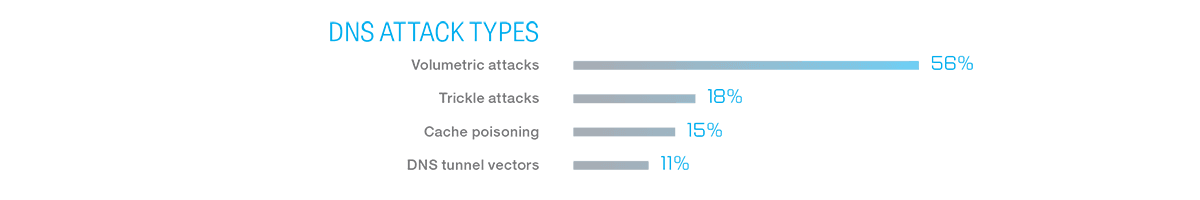
Service providers believe that volumetric DNS attacks pose the greatest risk to their networks, with trickle attacks, cache poisoning, and DNS tunnel vectors are also causes for concern.
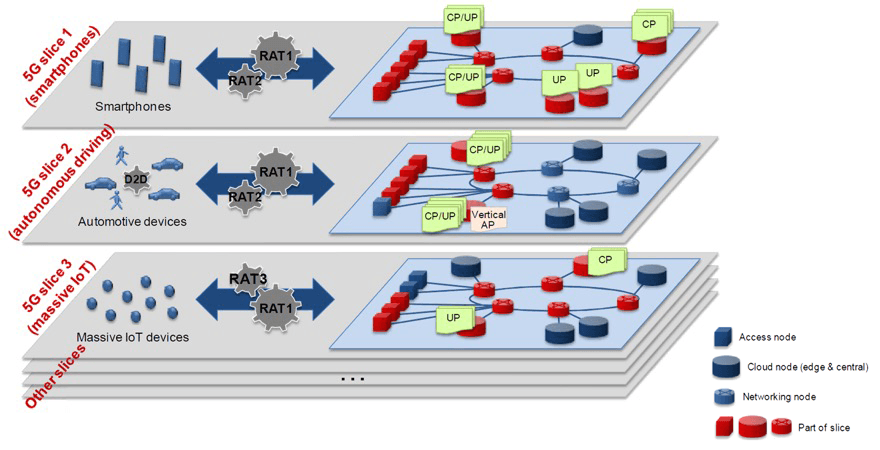
Leading industry thinkers believe that the optimal network architecture to support many types of devices will be a heterogeneous mix of LTE and 5G radios. The architecture will be built with both current and evolving technologies and include new Radio Access Technologies (RATs) optimized for deployments of each of the IoT use cases. For example, the IoT will use millimeter wave (mmWave) and LTE-Advanced for mobile broadband access.
The 3rd Generation Partnership Project (3GPP) is working on standards for three different IoT technologies: LTE-M, NB-IoT, and EC-GSM. In June 2016, 3GPP ratified the NB-IoT standard as a low-power solution that will work with existing wireless infrastructure. Several European carriers have also invested in low-power WAN technologies that are independent of LTE or 3G.
The emergence of low-power WANs like LoRA and Sigfox have motivated service providers and their vendors to explore low-power solutions in order to compete. For example, U.S. cable provider Comcast recently announced that they will trial low-power IoT services with LoRa in a few markets. If the trials prove successful, Comcast plans to deploy LoRa-enabled devices and network services that focus on use cases like utility metering, environmental monitoring, and asset tracking.
On the network side, network slicing will be an important mechanism to handle the diverse IoT application requirements and user groups. Slicing can provide isolated sub-networks, each optimized for specific use case traffic characteristics.
Service providers have embarked on efforts in 4G with Software Defined Networking (SDN) and Network Functions Virtualization (NFV), which will help pave the way toward realizing the 5G visions for the IoT. SDN and NFV introduce significant granularity, visibility, flexibility, and elasticity to networking, and these paradigms can enhance software programmability to create 5G network slices that can be customized per use case.
In addition to evolving the access and core networks to support the connected society, service providers are also evaluating messaging protocols such as MQTT and CoAP based on the requirements and fit of specific IoT use cases.
MQTT is based on TCP and is secured with TLS, while CoAP is UDP based and is secured by DTLS. Both of these protocols are optimized with much simpler and smaller packet size than HTTP for certain IoT applications, such as metering or industrial sensors.
MQTT and CoAP aren't new protocols but they have found a new life with IoT applications based on a publish-and-subscribe model. Devices/sensors will "publish" data to an IoT platform and the IoT application will then "subscribe" to the data that is relevant to its use case. Connectivity and communications between the device and its platform influence the load, control, and security required by each use case.
Service providers must ensure end-to-end security with tight authentication of devices, their access to communication paths, and the encryption of data. Authentication and access control will be essential in the partnering ecosystems to deliver IoT services to end users, while safety and privacy will be critical to the revenue streams of service providers.
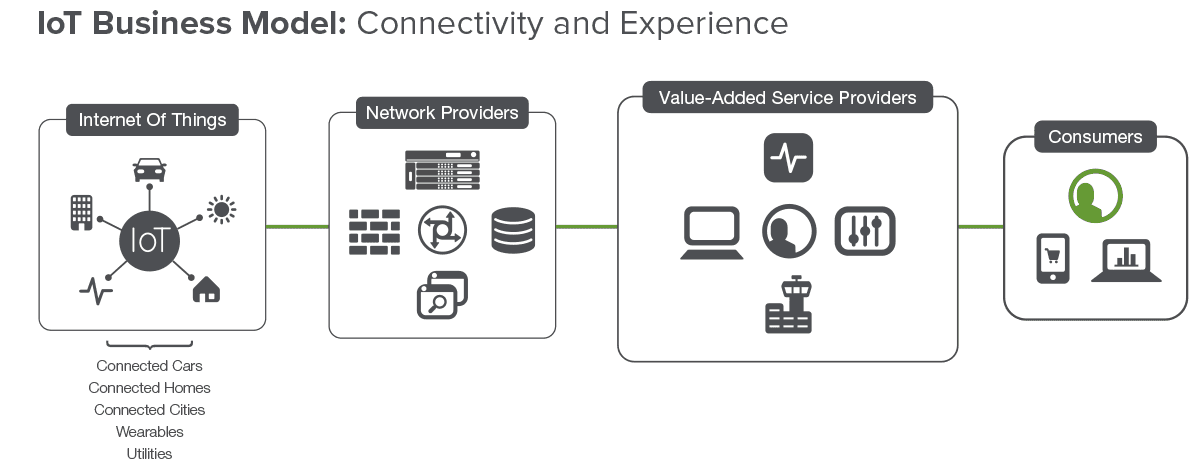
To survive and thrive in the evolving 5G/IoT ecosystem, service providers must deliver connectivity and become "Value Added Services Providers" through partnerships and tight integration of solutions. Below is a potential logical network and services delivery model that service providers could implement in their network—per the network-slicing concept—for each of the industry vertical use cases.
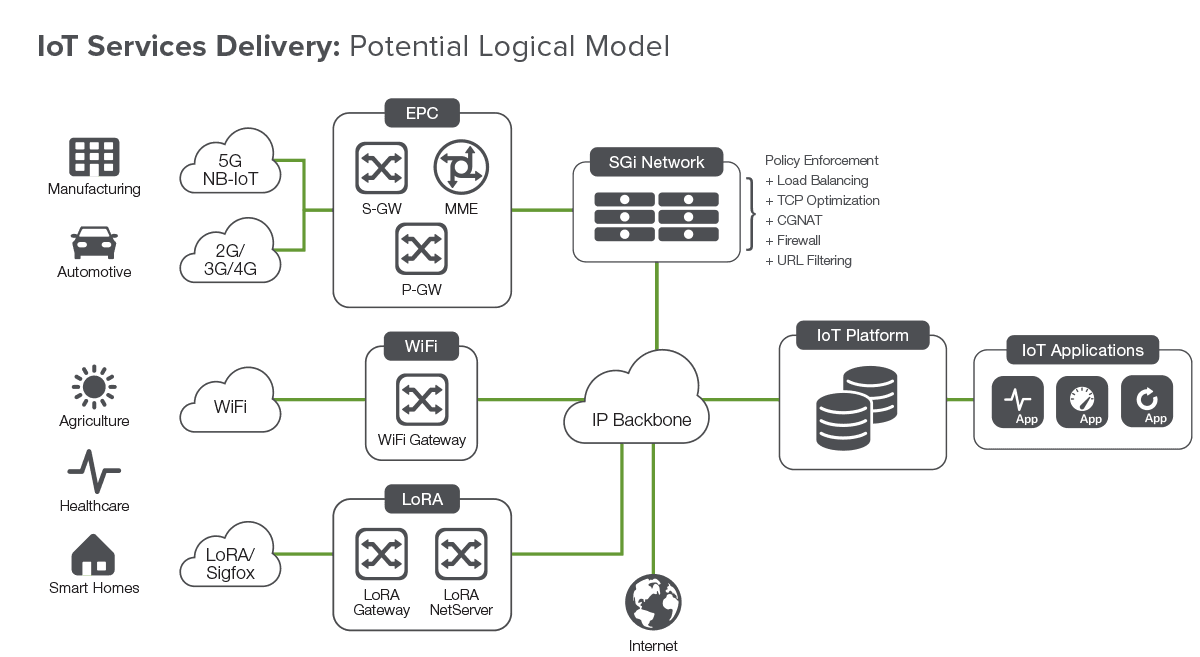
To handle the diverse number of IoT devices, coupled with requirements such as an ultra-low latency for certain use cases, the prioritization of each device, and corresponding requirements for IoT applications, service providers need to deploy secure, scalable, available, and high-performance solutions across their networks—from the device to the applications in data centers.
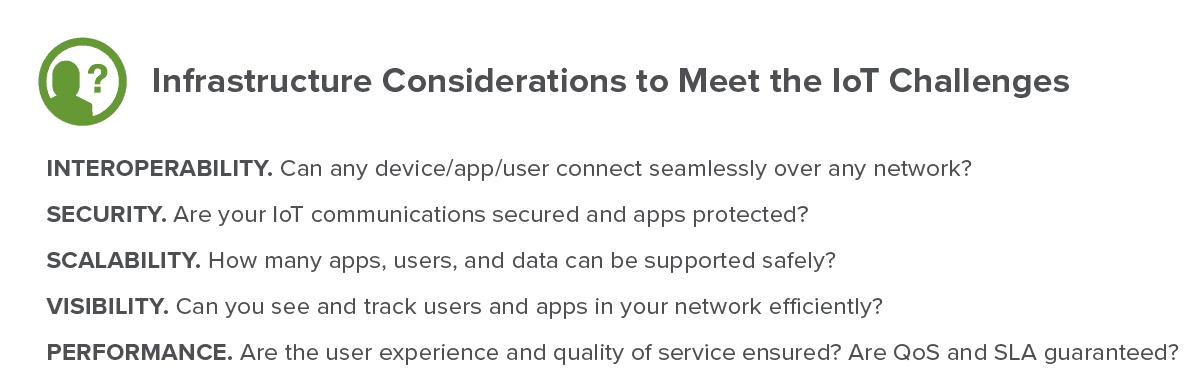
Comprehensive security will include implementing software/hardware platforms that can scale to billions of concurrent connections and support millions of new connections per second. Security platforms must provide the scale and performance required to handle sophisticated and emerging threats, mitigating potential attacks on devices, sensors, core network resources, DNS, and L7 services with visibility into applications.
Service providers will need signaling conformance and security solutions that will protect against protocol-specific attacks targeting protocols such as CoAP, MQTT, SIP, and Diameter. Finally, the network must be able to prioritize which device, corresponding applications, and associated signaling messages have access to the network with application-aware intelligence to optimize performance and improve quality of experience for users.
Robust solutions must give service providers the tools they need to seamlessly transition from today's purpose-built implementations to future virtualized solutions.
Security solutions need to be flexible and programmable with open APIs to offer the agility service providers require to create new revenue-generating services. To take advantage of potential new revenue, service providers must be able to integrate seamlessly with various ecosystem partners to deliver secure and actionable insights.
Simple and automated provisioning and upgrades of IoT services are also critical key factors in an agile network infrastructure. A programmable interface allows service providers to develop and tailor new services and implement virtual network functions (VNFs) to seamlessly transition toward the 5G network vision. A comprehensive, interoperable NFV/SDN ecosystem with programmable, open APIs, and advanced orchestration capabilities will enable service providers to scale their networks with more flexible and agile architectures. This can allow rapid services delivery—and potential cost savings—in the various IoT use cases.
Summary
The IoT clearly represents an important new business opportunity for service providers. While business models will continue to evolve as the number of connected devices grows, a few key concepts will remain at the forefront of an effective strategy for service providers.
To achieve the full market potential of delivering a seamless connected experience, service providers must develop and propose integrated solutions. To start, rather than offering IoT services across all verticals, service providers could identify and differentiate to offer a few IoT use cases such as shipping, asset tracking, and connected cars. It's important to start slowly to gain experience in working with partner ecosystems and creating new revenue streams.
By delivering connectivity, security, and an optimal customer experience using the same business model, service providers can cement their position as value-added solution providers and best capitalize on the burgeoning opportunities presented by the growth of the IoT.
To accomplish these goals service providers must architect secure and agile networks that offer connectivity, security, and an optimal customer experience.
Learn more about the scalable, high-performance security solutions required to mitigate sophisticated and emerging threats to devices, sensors, core network resources, DNS, and L7 applications at the F5 solutions for service providers page.
1 "NGMN 5G White Paper", February 2015, https://www.ngmn.org/wp-content/uploads/NGMN_5G_White_Paper_V1_0.pdf.
PUBLISHED DECEMBER 08, 2016