The global IT community is currently experiencing a confluence of challenging factors.
One glaring factor is the well-documented global semiconductor shortage, which has increased lead times for app delivery and security hardware. While demand for F5 iSeries appliances remains strong, high demand for appliances and the persistent chip shortages have led to extended delivery timelines for iSeries appliances (supply chain shortages are not affecting F5 rSeries appliances and VELOS chassis as significantly).
A second major factor is the continuing conflict in Eastern Europe, along with cyberwarfare concerns. As F5 Labs reported way back in 2018, such attacks can target government agencies, the private sector, and even home offices.
These two factors have significantly contributed to an environment in which new security deployments are urgently needed but many organizations are unable to procure solutions quickly. That said, we know that putting security on hold is not an option as more advanced threats are on the rise.
One prominent example: ransomware. The increasing threat of ransomware—up from 6% of all data breaches in 2019 to 42% of all attack chains researched by F5 Labs in 2021—has rippling impacts that cannot be overstated. Perhaps more than any other type of malware, ransomware has the potential to harm the supply chain by propagating through trusted vendors, rendering critical infrastructure and data unavailable, and negatively impacting economies both nationally and internationally.
To stop ransomware attack chains in their tracks, it’s key to implement a visibility solution that can peer into the encrypted channels that mask individual ransomware attack vectors. BIG-IP SSL Orchestrator deployed in the cloud can help you decrypt these channels and gain visibility into SSL/TLS traffic traversing your network. It can orchestrate the decrypted traffic to your security stack for threat inspection, while simultaneously bypassing the long lead times caused by global chip shortages and supply chain issues.
To help you address your security needs amid increasing cyberattacks and global supply chain shortages, we have teamed with Amazon Web Services (AWS) to offer High Performance Virtual Editions of BIG-IP SSL Orchestrator that you can deploy on AWS. Here are four reasons why SSLO Orchestrator on AWS may be the best choice for you:
1) You are experiencing longer than normal lead times for hardware
Security is too important to put on hold due to global semiconductor shortages and supply chain interruptions. In many instances, your organization may not be able to afford to wait months for the hardware you rely upon to deploy your security stack and defend your applications.
Fortunately, there are other options. With a High Performance BIG-IP Virtual Edition, you can bypass lengthy supply chain lead times by deploying BIG-IP SSL Orchestrator on Amazon Web Services, enabling you to address your organizations’ security priorities even during global hardware shortages. When deploying SSL Orchestrator on AWS, you'll enjoy identical feature sets present in both our on-premises solutions and our VE solutions; all form factors utilize our flagship BIG-IP software and share a common suite of use cases and capabilities. With AWS, you can spin up BIG-IP SSL Orchestrator quickly and scale on-demand as your capacity requirements increase or as your security needs change.
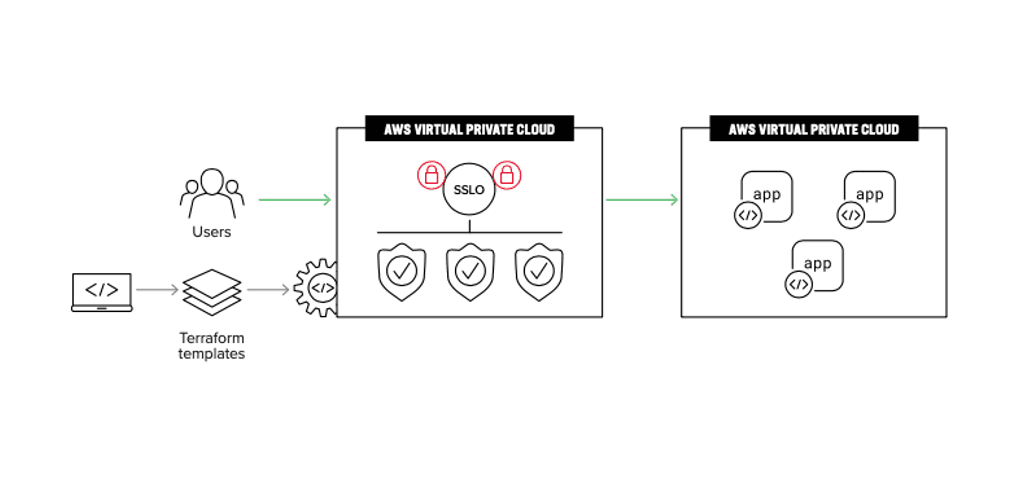
2) You need to scale SSL/TLS inspection quickly and want to take advantage of infrastructure acceleration and offload
One of the advantages of deploying SSL Orchestrator on AWS is that you won’t need to worry about scaling up your network infrastructure as your capacity requirements increase. With AWS, you can perform traffic decryption and re- encryption on the highly scalable AWS platform. This will bolster your SSL offload performance for maximum security and cost-effectiveness. As the amount of encrypted traffic traversing your network increases, you can scale out your decryption and orchestration solution as needed with flexibility.
With SSL Orchestrator deployed on AWS, your encrypted threats and orchestration solution will be high-performing and adaptable to your changing network conditions and organizational needs, while meeting the flexibility and scalability demands of the modern security landscape.
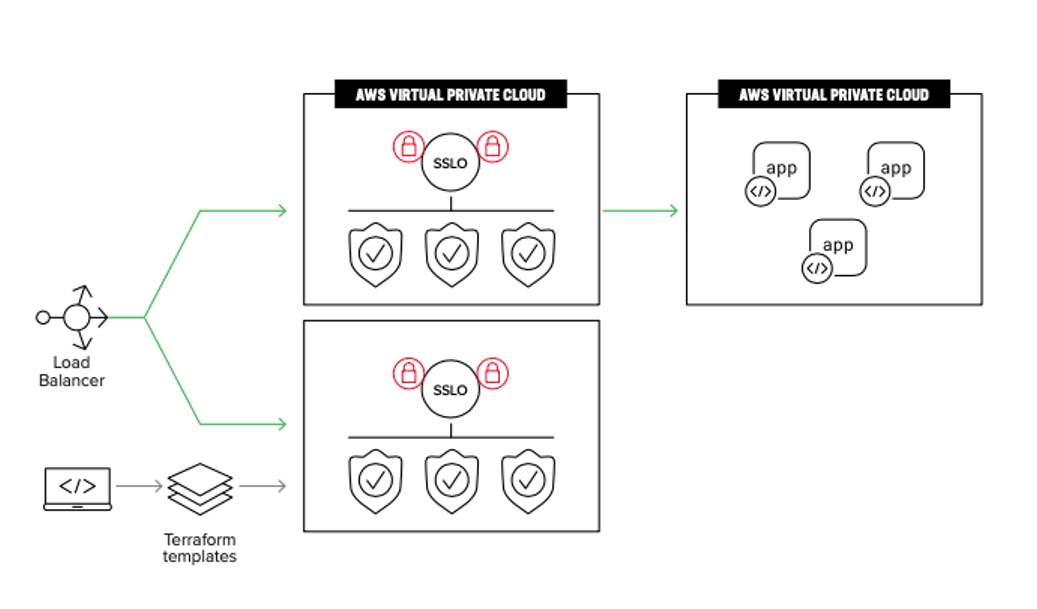
3) You need protection against ransomware entering at layer 3 through layer 7
Unfortunately for security professionals, ransomware can enter a network through a wide range of attack vectors. But many of these attack vectors have one thing in common: they enter via encrypted channels. Therefore, gaining visibility into encrypted traffic is an incredibly crucial aspect of mounting a comprehensive ransomware defense. With estimates suggesting that 90% of traffic is encrypted today, it is easy for attackers to take advantage of the privacy aspect of cryptography to evade detection by network monitoring programs. In fact, F5 Labs reported that 83% of phishing sites use a valid TLS certificate. Phishing, software and browser vulnerabilities (CVEs), and drive-by downloads are some of the most common entry points for ransomware—and all these attack vectors are likely to be encrypted. Monitoring encrypted traffic is therefore a crucial move in detecting ransomware entering or traversing your network.
With BIG-IP SSL Orchestrator, you can chain security services together, leveraging the solution’s intelligent classification metrics to create focused, appropriate security service chains based on traffic and network conditions, as well as your security needs.
4) You want flexible purchasing options
“Flexibility” is the name of the game with BIG-IP SSL Orchestrator deployed on AWS. Flexibly consume SSL Orchestrator using a High Performance VE of the model and licensing of your choice while lowering your security total cost of ownership and infrastructure footprint with the combined power of SSL Orchestrator and AWS. Due to the capacity requirements of decrypting SSL/TLS traffic, it is highly recommended that you license SSL Orchestrator as a High Performance VE. Throughput-licensed VEs are not recommended for SSL Orchestrator, as licensing the software in this manner may result in performance issues for SSL Orchestrator. Take advantage of High Performance BIG-IP VEs to deploy SSL Orchestrator on AWS. These unthrottled virtual edition instances without throughput limitations are capped only by the number of vCPUs that can power the instance.
With AWS, you need use only the resources and infrastructure you need to power SSL Orchestrator, allowing you to maximize your security investments.
Relax and let BIG-IP SSL Orchestrator as a High Performance Virtual Edition on AWS ease your semiconductor shortage and supply chain-induced worries about protecting your applications and data from ransomware and other malware, as well as command-and-control server outreach and data exfiltration.
More information
To learn more about if deploying SSL Orchestrator on AWS may be right for you, check out our joint solution overview and the AWS Marketplace listing. Contact sales.f5.com with questions about the solution.
Ready to deploy? Check out our set of Terraform templates and deployment documentation to help you get started.
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.