BIG-IP SSL Orchestrator
Maximize infrastructure and security investments with dynamic, policy-based decryption, encryption, and traffic steering through security inspection devices.
Maximize infrastructure and security investments with dynamic, policy-based decryption, encryption, and traffic steering through security inspection devices.
Bad actors take advantage of SSL/TLS encryption to hide malicious payloads to outsmart and bypass security controls. Don’t leave your organization vulnerable to attack with security solutions that can’t inspect encrypted traffic efficiently at scale. BIG-IP SSL Orchestrator delivers high-performance decryption of inbound and outbound SSL/TLS traffic, enabling security inspection that exposes threats and stops attacks before they happen.


You need orchestration to be on top of your security game. Visibility into and inspection of SSL/TLS traffic is a start, but it only scratches the surface. Daisy-chaining or manually configuring security solutions to support inspection across your security stack’s not scalable and ineffective. BIG-IP SSL Orchestrator intelligently manages the decrypted traffic flow across your entire security stack.
Shadow AI—the unsanctioned use of AI tools—introduces critical blind spots and can expose your organization to vulnerabilities. Simply blocking tools like generative AI might seem like an easy solution, but for most, it’s impractical. With BIG-IP SSL Orchestrator, you gain the visibility and control needed to easily address the risks of Shadow AI without compromising innovation.


Ransomware is one of the fastest growing cybersecurity threats. What once was an uncommon threat now makes up almost half of all attacks. Unfortunately, ransomware shows no signs of slowing down. It’s critical you protect your organization from ransomware sneaking in through encrypted payloads. BIG-IP SSL Orchestrator maximizes your ability to block these attacks by creating a comprehensive ransomware defense.
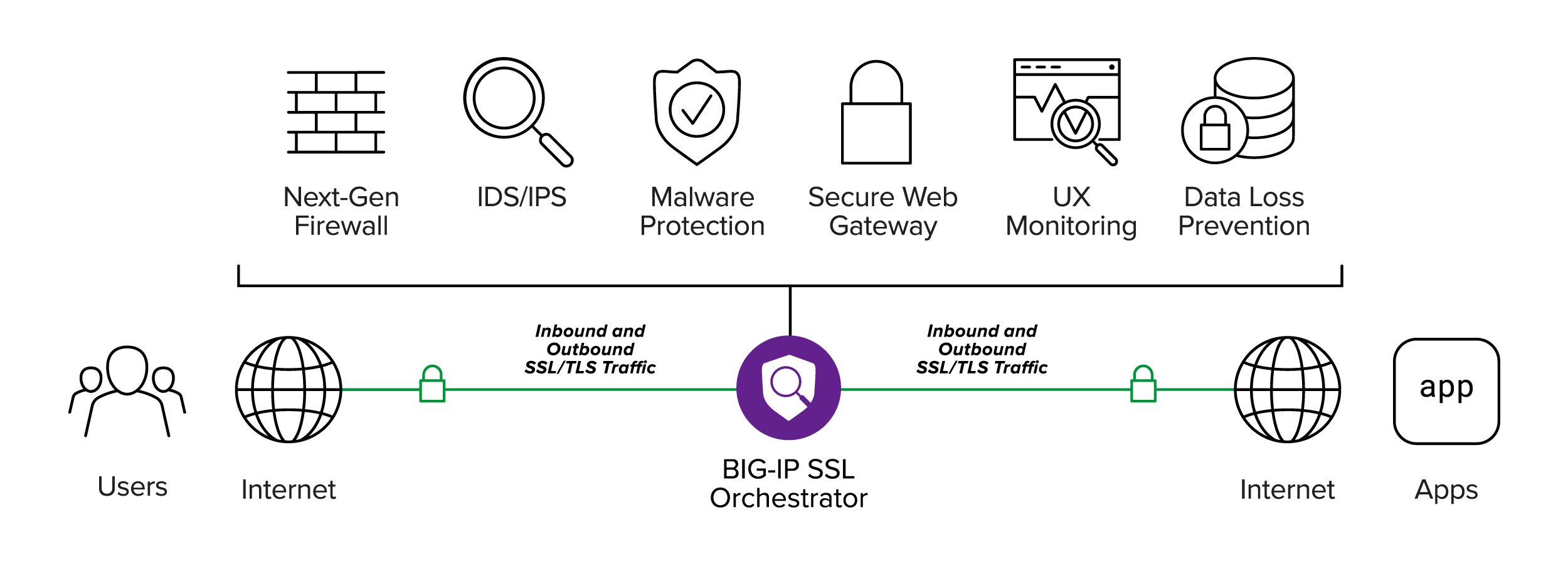
BIG-IP SSL Orchestrator enhances SSL/TLS infrastructure, makes encrypted traffic visible to security solutions, and optimizes existing security investments. It delivers dynamic service chaining and policy-based traffic steering—applying context-based intelligence to encrypted traffic handling to intelligently manage the flow of encrypted traffic across the security stack—and ensures optimal availability and security.
Deploy high-performance hardware in your on-premises data center or collocation facility.
Deploy on any hypervisor within your data center, collocation facility, or in AWS, Azure, or Google Cloud.
If you’re not inspecting SSL/TLS traffic, you’ll miss attacks and leave your organization vulnerable. BIG-IP SSL Orchestrator provides robust decryption/re-encryption and orchestration of encrypted traffic.
Provides SSL/TLS decryption and encryption, strong cipher support, and flexible deployment.
Provides service insertion, service resiliency, service monitoring, and load balancing.
Supports geolocation, IP reputation, URL categorization, and third-party ICAP integration.
Header changes, support for port translation, and control over ciphers and protocols.
Supports inline layer 2 and 3, HTTP proxy, ICAP, and passive/receive-only inspection services.
Standalone, cluster, and separate ingress/egress tiers.
Intercepts and inspects traffic without requiring any special client configuration.
Scales with high availability, F5’s best-in-class load balancing, health monitoring, and SSL/TLS offload capabilities.
While BIG-IP SSL Orchestrator is vendor and product agnostic, it’s optimized to easily integrate with the world’s leading security devices to create a powerhouse solution that’s ready to tackle any of your encrypted threat challenges.






At F5, we deliver broad, integrated support across cloud platforms to enable you to secure and deploy every app, anywhere—whatever your cloud journey looks like.




Trinity Cyber protects customers with a unique cybersecurity service line delivering deep content inspection with decryption by BIG-IP SSL Orchestrator.
Read the storyControl Shadow AI Risks with F5 BIG-IP SSL Orchestrator ›
Protecting Against Encrypted Threats ›
Protect Against Ransomware with AWS and F5 ›
BIG-IP Advanced WAF as a BIG-IP SSL Orchestrator Service ›
F5 Secure Web Gateway Services as a BIG-IP SSL Orchestrator Service ›
BIG-IP SSL Orchestrator Data Sheet ›
Cisco Firepower Threat Defense ›
Cisco Web Security Appliance ›
Menlo Security Remote Browser Isolation ›
Palo Alto Networks Next-Generation Firewall ›
Symantec Data Loss Prevention ›