There’s a kind of repetitive cycle to everything (or so it seems in hindsight) in which changes in app architectures and usage spur the need for new technologies in the network. Technologies designed to address those challenges that impede the success of applications, whether measured by consumer or corporate metrics (profit and productivity).
Availability and performance are usually the first of these challenges that need to be met. And always (or so it seems) last comes security. All three concerns, which align almost perfectly with the components of operational risk, tend to be answered with individual, targeted (we call them ‘point’) solutions.
At some point in the cycle, organizations realize they have way too many solutions deployed and that they’re contributing to the bloat that’s eating up operational budgets. That’s “solution sprawl.” So they naturally look to consolidate, or centralize, to reduce the operational burden on their budgets and, increasingly, their people.
Cloud is one of those app architecture changes, in that it provided another environment that was operationally and financially compelling as an option. Organizations have certainly taken advantage of it, and are continuing to do so today. While SaaS consumes the largest portion of the “cloud” application landscape, public IaaS and PaaS offerings are beginning to enjoy at least a modicum of success in attracting organizations.
This movement has led not only to operationally disjointed environments, but has caused a dramatic shift in what we traditionally viewed as the “perimeter” needing to be secured. No longer is the perimeter at the edge of the network, where corporate routers and firewalls pass off responsibility for traffic to providers and the Internet. Rather there are multiple perimeters, each one centered (appropriately, I would say) on an application.
Protecting each applications is paramount. This is inarguable. Applications are the gateway to the corporate vault of data, whether corporate or consumer. Applications simply cannot be deployed without proper security lest they be exploited and the data they’re designed to deliver, process, and manipulate becomes exposed.
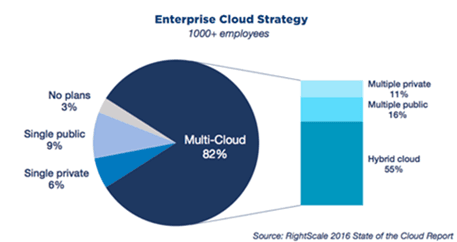
There is little difference between the notion of solution sprawl occurring on-premises, in the data center, and solution sprawl when it occurs across cloud environments.
Except that “centralization” isn’t as easy as consolidating solutions in one solution.
Or perhaps it is.
The cause of the solution sprawl – cloud – turns out to be the perfect solution to address the need to centralize at least security solutions in a manner consistent with the notion of each application being its own perimeter.
Centralizing critical application protection – network and application layer security – in the cloud affords organizations the opportunity to reduce solution sprawl. Doing so not only provides security that is more consistent across applications irrespective of their deployment location, but reduces the burden on security practitioners and processes alike, as log sprawl is also reduced, and event correlation becomes simpler.
Choosing a centralized solution that addresses the need to detect and prevent both volumetric network and application layer attacks further reduces the burden on network and security professionals, and addresses the need organizations have for visibility into application threats.
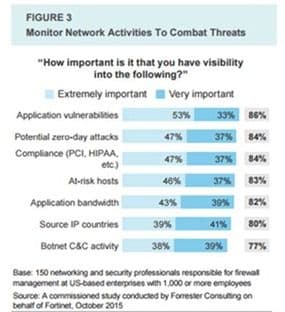
A Forrester study commissioned by Fortinet found that visibility into both application and network characteristics is important to both networks and security professionals. Being able to provide coverage of both in a single, cloud-based solution that can serve as the security sentinel to many applications across diverse locations is imperative in today’s cloud-distributed landscape.
Both DDoS and web application security are important in today’s high-stakes, high volume game of “protect the application.” Bringing both together in a single, cloud-based solution addresses the need to centralize security whilst establishing appropriate app-centric perimeters regardless of where that app may be deployed.
It’s infeasible to establish those app-centric perimeters on-premises. The architectural drawbacks of doing so outweigh the operational advantages. But moving that same concept to the cloud, as a cloud-based service, not only affords the same operational advantages innate to centralization but is an architecturally sound principle, as well. A cloud-based solution has access to greater bandwidth, which means it can withstand a deluge of network and application attack floods. A cloud-based solution has access to faster pipes, which means the extra “hop” required to enable application layer security for every application has relatively no impact. Conversely, trying to route all cloud-based app requests through an on-premises web app security service can cause excessive latency, not to mention an increased need for scale internally and potentially increasing available uplink bandwidth.
Centralizing DDoS protection together with web application security makes good operational and architectural sense.
For more information on a converged, DDoS protection and web application security cloud-based solution, check out F5 Silverline. And for a deeper dive this May 25, join us and Equinix for a live webinar on hybrid DDoS protection.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
