Most enterprise organizations today use between 200 and 1,000 applications on average, as pointed out in the F5 State of Application Strategy Report (Figure 1, below). These apps likely span multiple public/private clouds and data centers, which means keeping them available and secure is a challenge.

Just within the last year, we’ve experienced widespread, highly exploited vulnerabilities like Log4j and Spring4Shell. Security teams have worked day and night, seven days a week just to locate and alleviate the vulnerabilities in their existing apps, while desperately trying to protect against exploits and mitigate any damage. And, unfortunately, we only hear about the major vulnerabilities, because not all vulnerabilities are reported and categorized: NIST.gov pointed out that roughly 28% of vulnerabilities were simply not reported in 2021, out of that year’s total of 25,646 vulnerabilities.
Many organizations have mature vulnerability management programs in place where it's routine to patch production systems at least monthly. The big problem, though, is critical vulnerabilities are released every 9-12 hours, according to F5 Labs research, which also notes that almost three critical vulnerabilities are released each day. The concern over vulnerable code being exploited is even addressed in the OWASP Top 10, the standard awareness resource for DevOps and SecOps professionals; “Vulnerable and Outdated Components” has been called out in the latest OWASP Top 10 list (2021) and has even moved up in severity ranking from the previous list (2017).
Often, targeted threat campaigns will leverage known and used vulnerabilities to launch exploits and coordinated threat campaigns. These threat campaigns are sophisticated and can be incredibly difficult to detect. And in some of these cases, an organization can 'over-pivot' to employ highly restrictive security policies in an attempt to block attacks and threat campaigns, running the risk that even legitimate users may be blocked from resources they need to do their day-to-day jobs. This can be a very pressing issue, especially for smaller or understaffed security teams.
However, there are options. One excellent approach that can mitigate the coordinated exploits of applications and APIs via vulnerable code is by deploying a web application firewall (WAF). Even if your organization is slow in patching a known vulnerability, a WAF can protect your most critical apps and vital APIs from the attacks and exploits of coordinated threat campaigns. But, of course, the miscreants and criminals that launch threat campaigns are especially crafty and sly, with ways to mask a threat campaign so that it remains hidden from even the most well-tuned WAF. So, how can a WAF best deal with targeted attacks from these advanced threats without blocking their real users or negatively impacting their work experience?
F5 offers intelligent security threat services, including F5 Threat Campaigns. F5 Threat Campaigns is a subscription add-on to F5 BIG-IP Advanced WAF, and is included with F5 Distributed Cloud WAF and NGINX App Protect WAF. F5 Threat Campaigns uses security analytics with advanced machine learning and honeypots to provide organizations protection against common threats and exploits. F5 Threat Campaigns provides insights into the nature and purpose of an active threat campaign. Organizations today need live and actionable threat intelligence that can enhance the efficacy of existing security controls, including WAFs, with controls that automatically detect and block active threat campaigns. And that’s exactly what F5 Threat Campaigns does.
With F5 Threat Campaigns and an F5 WAF solution, your SecOps team can set granularly controlled security policies that protect your organization, apps, and APIs. The service helps protect apps and IT infrastructure from sophisticated threat campaigns by detecting and blocking attacks preemptively. Using machine learning, F5 Threat Campaigns is able to take threat feeds that may initially appear disparate and correlate them, finding threads of commonality between the different attacks and exploits, until a picture of a network of coordinated threat campaigns becomes clear and apparent. This helps a security team target and mitigate attacks and exploits that leverage existing vulnerabilities.
The latest feature in the F5 Threat Campaigns arsenal, F5 Threat Campaigns world map (Figure 2, below), was released just a few days ago. It is publicly available on F5.com for anyone to see and use—helping provide greater visibility into cyberattack campaigns with insight and telemetry presented together. This map may be viewed at scale, allowing viewers to dive into ongoing threat campaigns in granular detail.
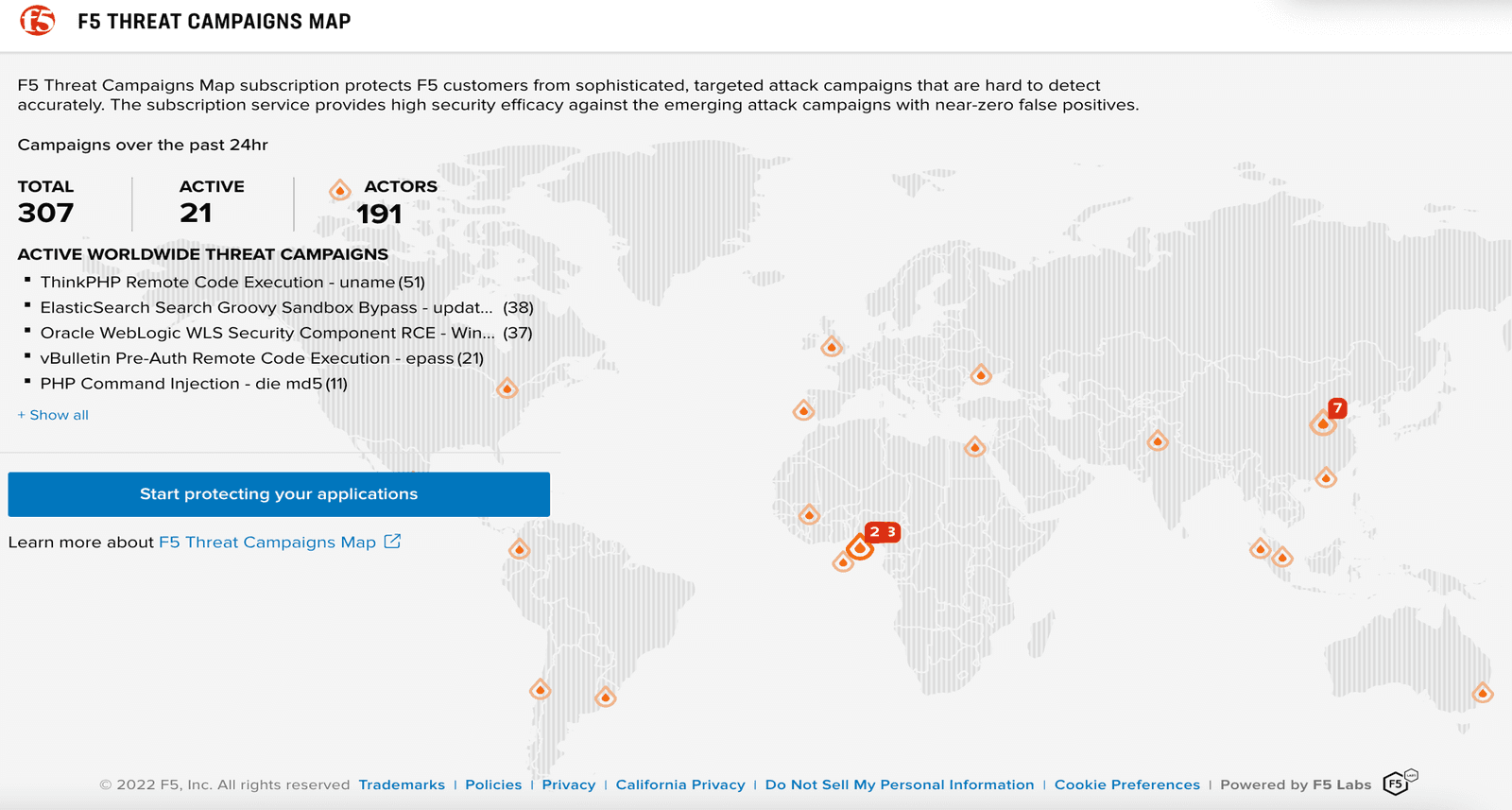
In addition to the new F5 Threat Campaigns Map, F5 Threat Campaigns includes:
- Live updates with actionable threat intelligence from F5
- Improved web application security with near-zero false positives
- Confident risk mitigation with a cost-effective model
- No more threat hunting
- Visibility into accurate, relevant threat feeds
In the run-up to addressing and ultimately mitigating the Log4j exploit, F5 released several protections, rules, and policy updates, as well as communicated actively and often with customers and the public. F5 also released F5 Threat Campaigns to address active Log4j exploits in the same week. F5 Threat Campaigns customers were also able to detect attacks exploiting the Spring4Shell vulnerability in their threat feed, blocking and mitigating the threat (Figure 3, below).
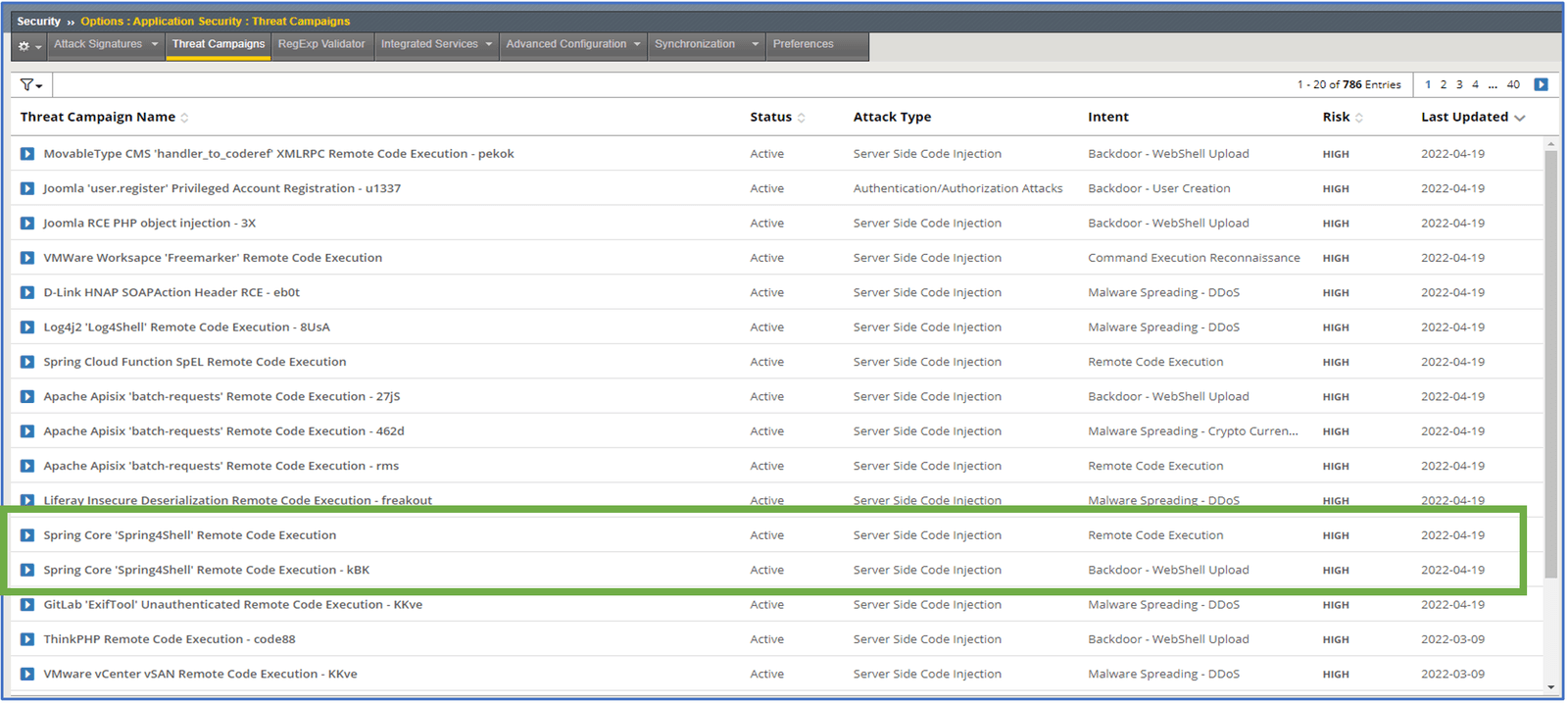
With access to the newly released F5 Threat Campaigns map that’s equipped with live feeds on coordinated campaigns, attacks, and exploits leveraging vulnerabilities, like Log4j and Spring4Shell, you, too, can empower your WAF to mitigate and address targeted attacks with F5 intelligence services (including F5 Threat Campaigns).
Please reach out to your Channel Partner or F5 Account Manager for more info on how to add a subscription for F5 Threat Campaigns to your BIG-IP Advanced WAF, or to begin using F5 Threat Campaigns on your F5 Distributed Cloud WAF or NGINX App Protect WAF solution today.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
