Phishing and fraud are most often (and lamentably) associated with financial and banking industries.
Fraud is just another word for trickery, for deception, for deceit, and for chicanery. And those are exactly the means by which attackers obtain credentials from corporateusers every day. Through phishing and through malware deposited on corporate assets by the simple act of browsing. Oh, I know, you don’t let corporate users browse those kinds of sites. But do you let them browse the BBC? Newsweek? The New York Times? How about MSN? All were recently victims of malvertising, where bad guys use top-tier sites to distribute malware laden online ads through online advertising companies. Oh, you’ve got anti-virus software running, of course. But only 25% of real-world malware is caught by anti-viruses according to the Five Habits Of Highly Successful Malware. You’ve no doubt had multiple “security awareness” sessions with your employees teaching them to recognize the signs of a phishing attempt. And yet nearly 50% of victims open that e-mail and click on the link within the first hour of receiving it.

Now let’s not forget that people are accessing their financial institutions, where phishing and malware is heavily relied on by the bad guys, from within the work place. Research from IDC indicates 30-40% of Internet access time in the workplace is spent on non-work related activities. That may be why our F5 SOC found that phishing attempts were significantly higher during the week than it was on the weekends, with Monday being a very popular day to go phishing. If an employee is out doing some banking on Monday morning and falls victim to a phishing attack intended to snag their financial credentials, well, the bad guys are likely to get corporate ones, too. Because AV isn’t catching everything, and people are still falling victim to phishing attacks. Those corporate credentials are just as sellable on the open market as any other, meaning very.
Then there’s the employees who access corporate assets through an SSL VPN or other “protected” portal from outside the corporate walls. The malware that’s sitting in their browser right now doesn’t really care whether it’s grabbing corporate or consumer-related credentials. They’re all worth something to the attacker, and as long as they went to all the effort to infect that device, why not grab everything you can?
The reality is that “fraud” isn’t peculiar to finance and banking. Oh, they’re the hardest hit and see the most immediate impact because the bad guys are after the money they’ve been asked to steward for the rest of us. But if you recall some of the “big” breeches in the past few years most of them point back to a single root cause: stolen credentials.
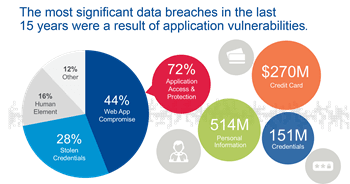
Credentials that may have been stolen through phishing or malware directly or through trojans that made their way past traditional detection systems and gave the bad guys an easy “in” on your network. From there, data is more often than not the goal. Customer and corporate data alike. The next thing you know, bam! You’re on the cover of “Guess Who Failed to Protect Your Data this Week Magazine*”.
The costs of dealing with that breech go way beyond the technical and operational.
Brand and Business Impacts
Oh, there’s recovery and clean up costs, of course. Resources are reallocated to rooting out every instance of malware and backdoors stemming from that single successful phishing expedition. Desktops are wiped and reinstalled to eliminate those that got in from drive-by downloads or malvertising. A significant loss of productivity across IT and business units ensues, cutting into your bottom line.
And then the brand impact sets in. The Twitters are alive with angry sentiments. Your heretofore pristine brand is turned into a mocking meme that spreads faster than the first winter cold through an elementary school.
Once the desktops are clean and stronger protections put in place, the aftershocks of a breach continue to hammer at your brand reputation and you’re going to have to address that. According to a recent study over half (57%) of organizations admit that security incidents had a negative impact on their reputation costing small and medium businesses more than $8000 and enterprises over $200,000. Some of that costs come from hiring external agencies to help manage the overwhelming demand for responses, answers to questions, and advice on how to proceed. Some of it comes from costs incurred meeting consumer expectations to provide identity theft protection (63%), credit monitoring services (58%), and compensation in the form of cash, products, or services (67%).

Some of it comes from losing customers, because as it turns out, brand is a significant factor in consumers’ purchasing decisions. Price is usually fingered as number one, but it turns out that price considerations are relative to the reputation of the brand. Consumers will pay for more for a brand with a good reputation, which makes it imperative that after a breach your brand is repaired as soon as possible.
But the damage isn’t restricted to consumers, though that’s usually the first place we look. Recruiting, it turns out, is also impacted. Attracting the right talent takes money, and the Employer Branding Global Trends report noted that good employer brands experienced a 22% lower recruitment fee. That’s assuming you can interest the talent in the first place. The same survey found that 45% of potential hires place other people’s perception of the company they work for on their list of “important” when it comes to choosing a new job. Brand impacts whether or not people want to work for an organization, so breaches can negatively impact your ability to attract (and potentially retain) the talent you need to succeed today.
Addressing Web Fraud
The good news is that there are tools that address the threats from phishing and malware. A lot of them. The thing is they’re generally categorized as “anti-fraud” and mentioned in the context of finance and banking and other money-based industries. But the solutions aren’t peculiar to finance and banking; there’s nothing magical about the way those industries interact with customers that makes anti-fraud only applicable to protecting them because they’re really about stopping web fraud; the use of web apps and technologies to trick, deceive, and coerce individuals into giving up their credentials.
What web fraud solutions do is seek out and prevent the theft of credentials that ultimately assist attackers in breaching security. Whether they’re after cash or data isn’t relevant; once they’re collecting credentials they’re collecting any credentials, whether they’re corporate or consumer. If employees access corporate resources using a compromised machine, the bad guys get corporate credentials right along with everything else. And that should be a concern for business in any industry.
* Not a real publication but after the spate of breaches over the past few years it seems like there’s a need for one, isn’t there?
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
