F5 launched Distributed Cloud Services in 2022, providing web application and API protection for enterprise organizations that need edge-based security that can be consumed as a service. In today’s interconnected world, cyber threats are on the rise and organizations must be prepared to protect their critical infrastructure from new evolving attack types. One of the most common types of cyberattacks is a distributed denial-of-service (DDoS) attack, which can bring down even the largest websites and online services.
Recently, a prominent pro-Russian hacktivist group known as Killnet launched a sophisticated L7 DDoS attack on a large European organization. The attack aimed to overwhelm the company’s servers with massive amounts of traffic, making it difficult for users to access the website with attack traffic peaking at 120K RPS. However, thanks to the efforts of the F5 Security Operations Center (SOC) and the advanced DDoS mitigation capabilities of F5 Distributed Cloud Services, the attack is being successfully mitigated, and the website has remained operational throughout the attack. This attack is part of several DDoS campaigns that have been occurring over the past few weeks originating from this group.
Note: This is an active attack campaign that has been happening for over a week, and we are successfully mitigating these attacks as this blog post is being written.
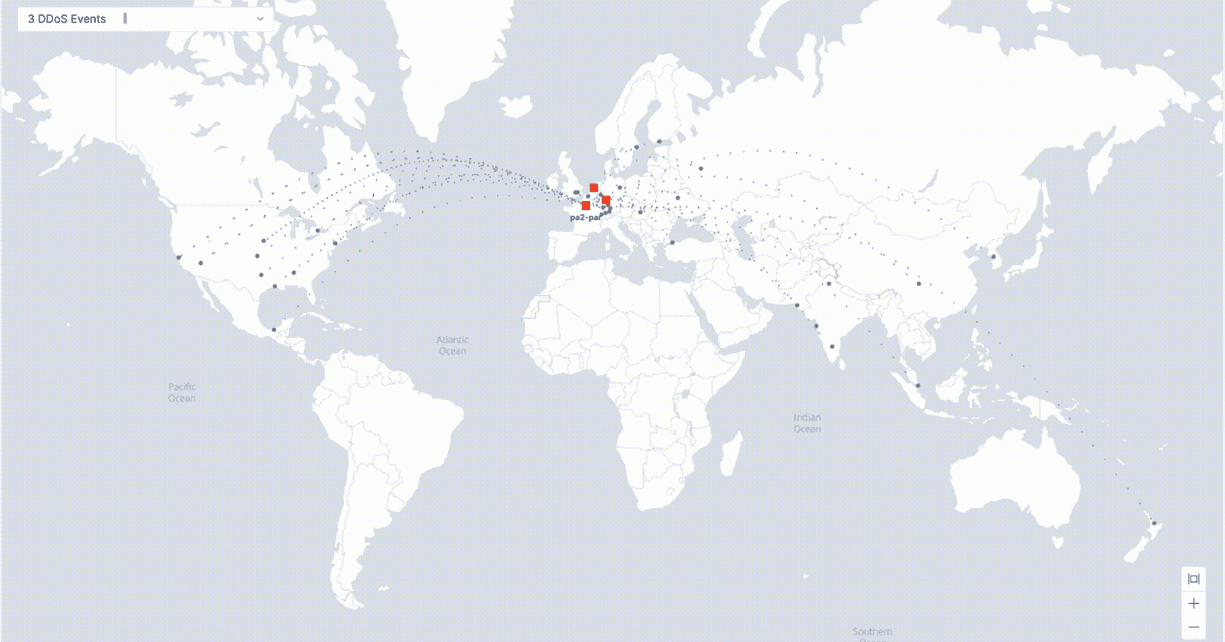
This specific DDoS attack originated from multiple locations across the globe. The grey dots on the map above represent attack origins, and the red boxes represent F5 Global Network points of presence where the application’s attack traffic is filtered, and legitimate traffic is being allowed.
One of the key characteristics of Killnet’s attacks is their focus on the application layer (L7). These attacks are particularly challenging to detect and mitigate, as they often involve mimicking normal user behavior (making them difficult to distinguish from legitimate traffic), multiple application attack vectors, and the ability to retool—including cycling through different source locations, IPs, and other attack components.
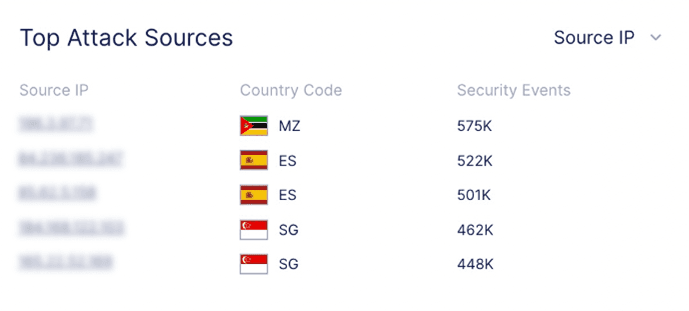
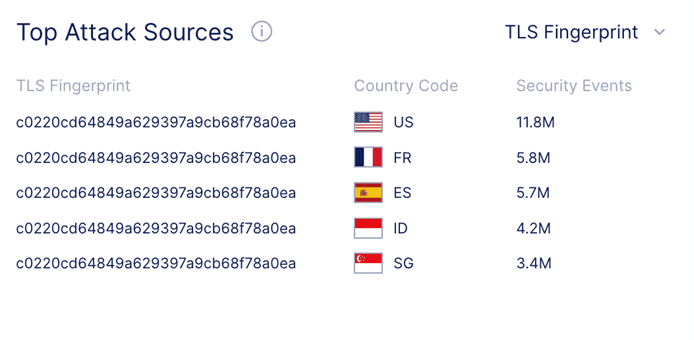
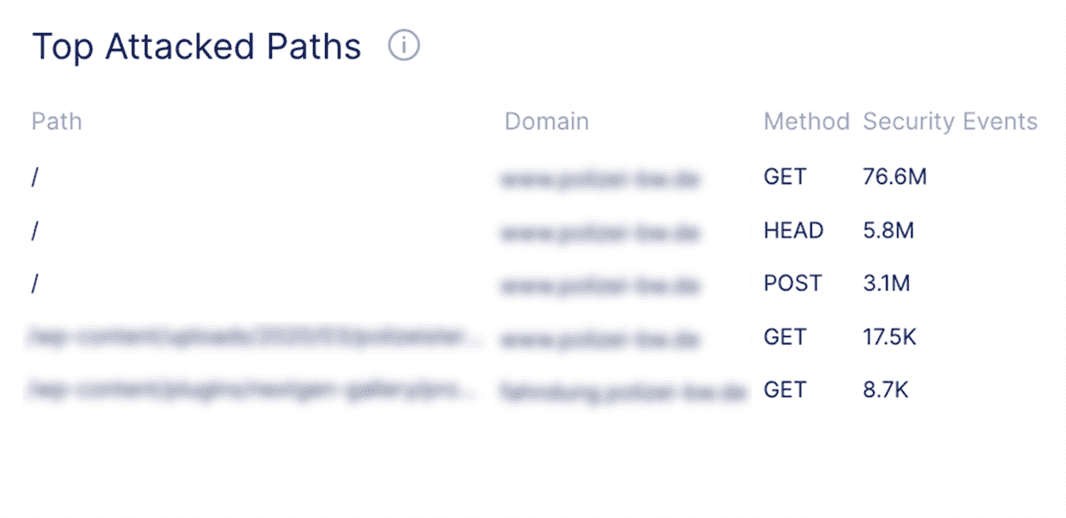
Attack traffic is originating from only 3 different TLS fingerprints, even though the source of the traffic is distributed across 35 different IP addresses and 19 countries. We are seeing 72% of attack traffic originating from 1 TLS Fingerprint which is shown in the above image. This fingerprint has been associated with Tofsee malware, where systems infected with Tofsee are used as part of a DDoS botnet.
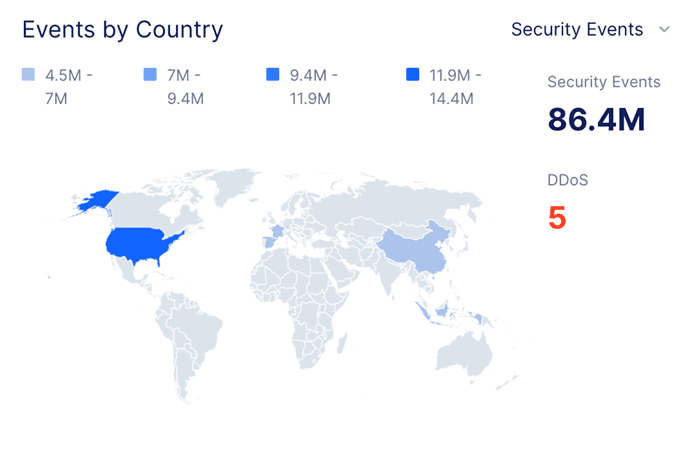
The F5 SOC is employing a variety of strategies to defend against the attack, including traffic filtering, IP intelligence and rate limiting. This allows the team to identify and block only malicious traffic while allowing legitimate traffic to continue reaching the website. Another key component of successful mitigation is the team’s use of real-time threat intelligence and L7 DDoS auto-mitigation capabilities, which has blocked elements of this attack in real time without the need for human involvement. This information allows the team to stay ahead of the attackers and quickly adjust their defenses as the attack evolves across geos, different IP addresses, and new attack paths.
The successful mitigation of the L7 DDoS attacks by Killnet and other groups represents a new normal—check out more DDoS attack insights in our F5 Labs 2023 DDoS Attack Trends report. This attack recap highlights the importance of having a multi-layered security infrastructure in place and a well-trained security team ready to support in real time. By using a combination of traffic filtering, rate limiting, cloud-based DDoS scrubbing, real-time threat intelligence, and a solid disaster recovery plan, organizations can protect themselves against even the most sophisticated DDoS attacks targeting their infrastructure and applications.
If you are experiencing a disruptive attack and need emergency onboarding to F5 Distributed Cloud Services, contact our emergency support line at: (866) 329-4253 or +1 (206) 272-7969
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.