Malwares And Their Impact
Malwares have caused billions of dollars as loss for the financial industry, and there is no looking back. At this juncture one would think that the field is so lucrative that malware writers would craft out new attacks for, on contrary we find that malwares have been reusing codes and reincarnating themselves in different forms. Most malwares use exploits like Man in The Browser (MiTB), Man in The Middle [MITM] etc. for their nefarious purposes.
This article talks about Man in the Browser and F5’s Fraud Protection Solution (FPS) based mitigations. There is a whole school of malwares known to leverage on this attack vector. Bugat, Gozi, Tatanga, SpyEye, Zeus are few of the well known malwares which used MiTB technique.
What is Man in the Browser?
A trojan horse infecting the browser and modifying the pages and transaction covertly before it is rendered to the user or submitted to the server can be summed up as MiTB.
Most browsers provide functionality to extend the capabilities; it comes as Browser Helper Objects for Windows, Extension for Google Chrome, and Plugins for Firefox etc. While these extensions greatly enable and provide for customized browsing, they are also used as tool by malwares. Imagine the next time you logon to your favorite bank and it shows you a message like this, you would say MiTB is active.
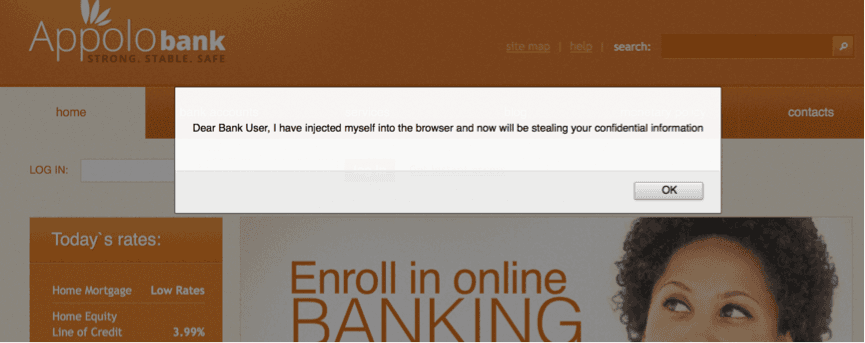
Unfortunately the attackers are sophisticated and subtle and it all behind the wraps. They use the browser’s capability to enhance user-browsing experience and put it to a more evil use. The screen grab below display a malware making a covert request to a drop zone with captured credentials.

F5’s Fraud Protection Solution is the Answer
The fraudsters use the browser to steal information and the servers are completely ignorant of these transactions originating at client end. The need of the hour is to monitor these transactions originating at the customers browser without hampering or altering his browsing habits. F5’s FPS helps in monitoring such suspicious activities.
Some of F5 unique capabilities to defeat MiTB attacks include
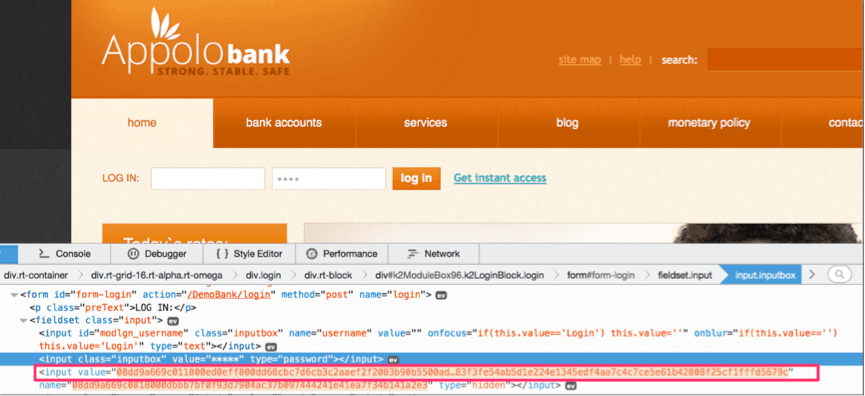
HTML form Field Obfuscation: Sensitive field names like username and password are replaced by random strings defeating automated scripts looking for specific Document Object Model (DOM) elements.

Real-Time Encryption of sensitive fields: Identified critical fields are encrypted as the user types.
Fake Strokes to defeat browser based key loggers: Key strokes generated hides the actual user inputs defeating browser based key loggers.

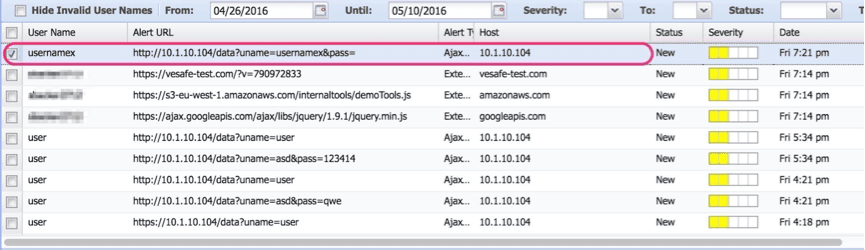
Alerts on external Script injection by Malware: FPS alerts the banks if an AJAX made a post to a different domain.
Conclusion
Man In the Browser attacks are capable of defeating channel encryption and stealing confidential information from the Browser. F5’s FPS solution helps cover the security gap and gives organization visibility and protection on users browser.
Resources
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.