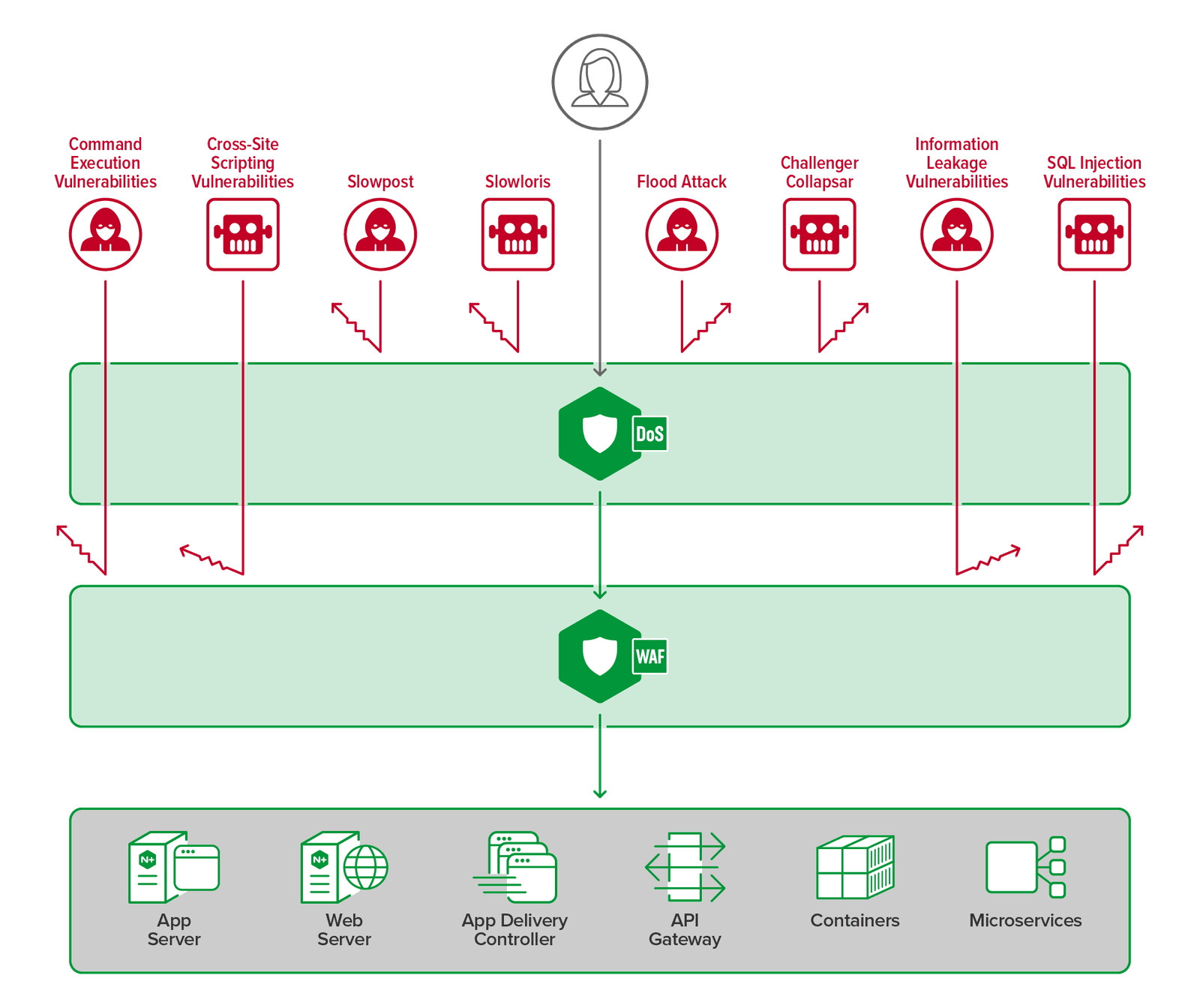
Multilayer defense refers to a security strategy composed of multiple independent security management layers, ensuring continued functionality even if one layer fails or is compromised. These layers generally include factors such as personnel, technology, and operations. By layering these management systems, attacks that cannot be mitigated by one layer during data processing can be blocked by another layer within the same system.
There are several ways to implement a multilayer defense strategy. For technical aspects, it is recommended to consider the following three points:
Related Content