Pop quiz time. Which of these endpoints belongs to an API and which one belongs to an app?
https://www.example.com/product
https://www.example.com/product
If you’re confused and can’t decide, that’s okay. That’s the point. App and API endpoints look pretty much the same. That’s because in technical terms if they’re RESTful (and most are) they are invoked in the same way, via HTTPS and usually with a GET method. What’s often different is the payload sent with the request. For APIs that typically contains some data in a JSON or XML format while web app requests may contain, well, nothing.
Still, one of the key findings from our annual research implies that organizations treat APIs as different from applications when it comes to security. We infer this based on the finding that 41% of organizations have at least the same or more number of APIs as they do applications and yet place a lesser value on the same security services that protect them.
You might wonder how organizations would end up with more APIs than apps. Thanks for asking! While APIs used for internal, service-to-service communication (a la microservices) are certainly tightly coupled to the service they support, this is not necessarily true when APIs are used to present external interfaces.
Where do APIs come from?
Consider that in our 2021 research, 61% of respondents told us they were “adding a layer of APIs to enable modern user interfaces” as a method of modernization. In 2022 that number was 45%. What that means is the APIs enabling modern user interfaces are not necessarily artifacts directly attached to applications. They might be façades that facilitate modern user interfaces and applications, like mobile apps and digital services, or they might be façades designed to enable partners and supply chain communications. These use cases are supported by API Gateways and layer 7 routing in load balancers, which often provide some level of transformation capabilities that allow them to translate from API endpoint to app endpoint, thus enabling an API façade like those that make old American west buildings appear much more impressive than they are.
And of course, a goodly number of APIs are public-facing entities attached to apps and accessed via the web (typically HTTPS).
Regardless of how they got there, public-facing APIs are subject to many of the same attacks as applications. This is especially true when bots are involved, as APIs with good documentation simply make it easy for attackers to script attacks at scale.
For example, just over 13% of transactions protected by F5 Distributed Cloud Bot Defense in 2023 were automated. That is, a script or software was used instead of a human using a web browser or mobile app. Those transactions occur via both APIs and apps. Some percentage of those automated transactions were certainly “bad bots” that the presence of our security service prevented from doing whatever bad thing they were trying to do. (You can dig deeper into what they were trying to do in this F5 Labs report)
So, when we looked at how respondents perceive bot management based on their self-reported number of APIs, we were somewhat shocked to discover that bot management is pretty low on the importance scale.
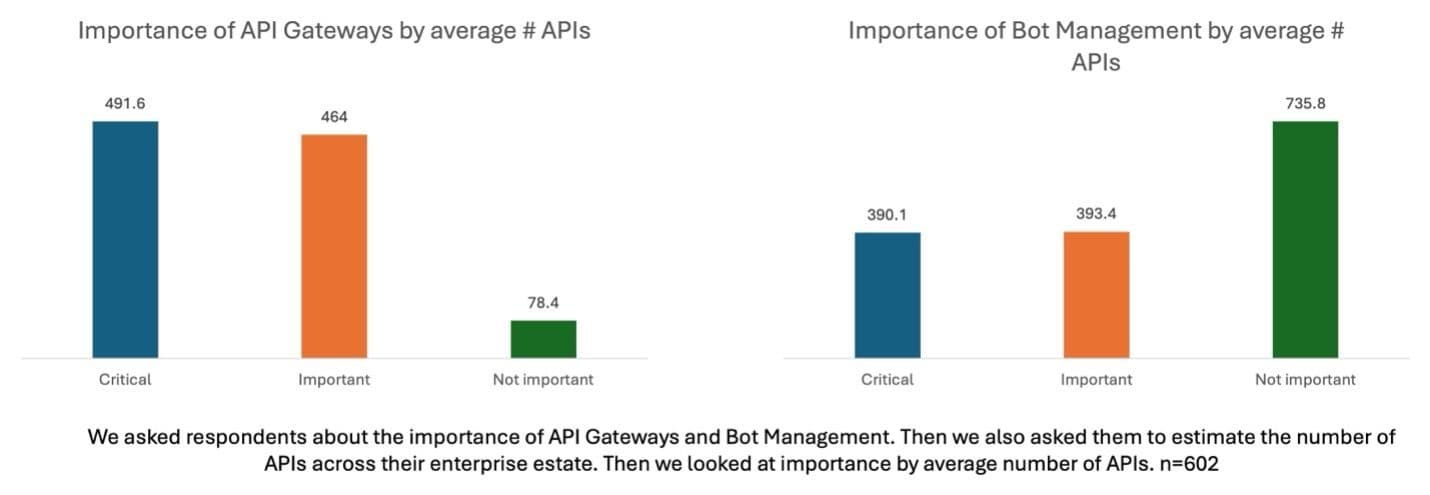
You can see from these nifty bar charts that while the importance placed on API Gateways appears to be appropriate to the number of APIs under management, the same is not true for bot management. In fact, it’s completely the opposite! As the number of APIs grows, the importance of bot management appears to decline. Rapidly.
It could certainly be the case that the bulk of those APIs are internal. That is, they are east-west APIs between microservices that are not exposed to external actors that might be bad bots with malicious intent.
But then again, they might be. Given the number of articles I’ve read in the past year about attackers gaining access via APIs, I’m going to guess there are a lot more external than we think.
So, it’s time to remind folks that while there are a number of annoying bots out there—grinch bots, sneaker bots, etc.—that disrupt business by gobbling up high-demand goods, there are also a significant number of bots whose only purpose it is to sniff out vulnerabilities and attack them. In both APIs and applications.
Thus, it would be a good idea for organizations to employ a full range of security options to protect their APIs and ultimately, their business. Bot management is certainly one of those security options and should be considered a critical component of any security strategy.
At the end of the day, the bots don’t care whether that endpoint belongs to an app or an API. They’re going to attack both.
Which means organizations need to be protecting both apps and APIs by detecting bots and preventing them from doing whatever bad thing they’re trying to do.
Want to see bot defense in action, check out this demo.
About the Author

Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.
