
We are living in, as the Chinese proverb-curse says, interesting times. A growing awareness of confidentiality and integrity has led to a groundswell of efforts to, in effect, encrypt “all the things.”
Whether it’s web sites and applications (SSL Everywhere) or internal communications (SSH), encryption is often considered the foundation of every organization’s security strategy.
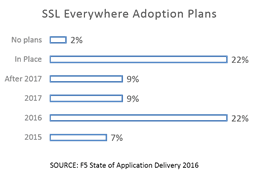
And yet encryption is not a panacea and can, in fact, create as many problems as it solves. End-to-end encryption makes communications (and the data it might carry) safe from inspection and prying eyes and that is, in general, a good thing. Except when it blinds security practitioners from being able to use the myriad tools in its infrastructure toolbox to ensure other aspects of security.
Because we all know that encrypted malicious data is still malicious, and encrypted unauthorized command execution is still, well, unauthorized.
What we’re losing from the picture is visibility; the ability to “see” who is doing what, from where and why.
Visibility lost that can make useless investments in security infrastructure. Visibility lost that can prevent IT from detecting and preventing data leakage. Visibility lost that can prevent policy enforcement that protects devices, things, and systems from unauthorized access. Research from Gartner stated that “80% of the organizations that use these security devices [NGFW, IPS, UTM] might be allowing cybercriminals to bypass the organization’s existing security controls by leveraging SSL tunnels to sneak malware into the corporate network…” (Are Cybercriminals Hiding in Your SSL Traffic?)
Running a business blind to those threats that can cause damage is not exactly the outcome hoped for by encrypting all the things.
Like the Force, there must be balance. Communications must be encrypted to ensure confidentiality and privacy, but security policies and practices must also be enabled with the visibility necessary to enforce and execute.
That’s why "smart” intermediaries are a must in any architecture supportive of a comprehensive security strategy. Intermediaries that are capable of maintaining the security and privacy offered by encryption without eliminating the visibility necessary to detect and prevent malicious or unauthorized communication. Whether those intermediaries are acting as terminating points for encrypted communications or simply offering a view into what’s beneath the cryptographically encoded stream, these architectural gateways are imperative to ensure visibility is available in this era of encrypt everything.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
