For years, programmability of the control plane has been dominated by APIs. From F5, that's meant iControl. First as a SOAP interface and then later as REST, iControl has afforded NetOps what its name implies: control over every aspect of a BIG-IP configuration.
That method is not going away. APIs provide the granular control many organizations need to manage their application service deployments. They are also key to integration efforts with partners and new environments.
That does not mean that APIs are the "one true way" to automate the operation of a BIG-IP. In fact, in the movement to adopt a more continuous approach to deployment of applications and application services, an alternative method has arisen. That method is declarative, in which a configuration end-state is described by the operator and responsibility for implementation off-loaded to the target system.
There are many reasons to adopt a declarative method of configuration, not the least of which is its alignment with DevOps approaches like infrastructure as code and continuous deployment. This is the goal behind F5 AS3 - to provide a declarative interface that decreases reliance on APIs and increases the ability to implement a fully automated, continuous deployment pipeline. It's more appropriate to call it configuration as code, as we're not actually building the infrastructure from code as the term implies.

AS3 is a declarative format that uses JSON key-value pairs to describe a BIG-IP configuration. From virtual IP to virtual server, to the members, pools, and nodes required, AS3 provides a simple, readable format in which to describe a configuration. Once you've got the configuration, all that's needed is to get it to the BIG-IP, where the AS3 extension will happily accept it and execute the commands necessary to turn it into a fully functional, deployed BIG-IP configuration.
Sample translation of VIP and pool description in bigip.conf as an AS3 declaration:
bigip.conf | AS3 declaration |
ltm virtual /Common/serviceMain { destination /Common/10.0.1.10:80 ip-protocol tcp mask 255.255.255.255 pool /Common/web_pool source 0.0.0.0/0 translate-address enabled translate-port enabled}ltm pool /Common/web_pool {members { /Common/192.0.1.10:80 { address 192.0.1.10 } /Common/192.0.1.11:80 { address 192.0.1.11 } } monitor /Common/http} | "serviceMain": { "class": "Service_HTTP", "virtualAddresses": [ "10.0.1.10" ], "pool": "web_pool" }"web_pool": { "class": "Pool", "monitors": [ "http" ], "members": [ { "servicePort": 80, "serverAddresses": [ "192.0.1.10", "192.0.1.11" ] } ] } |
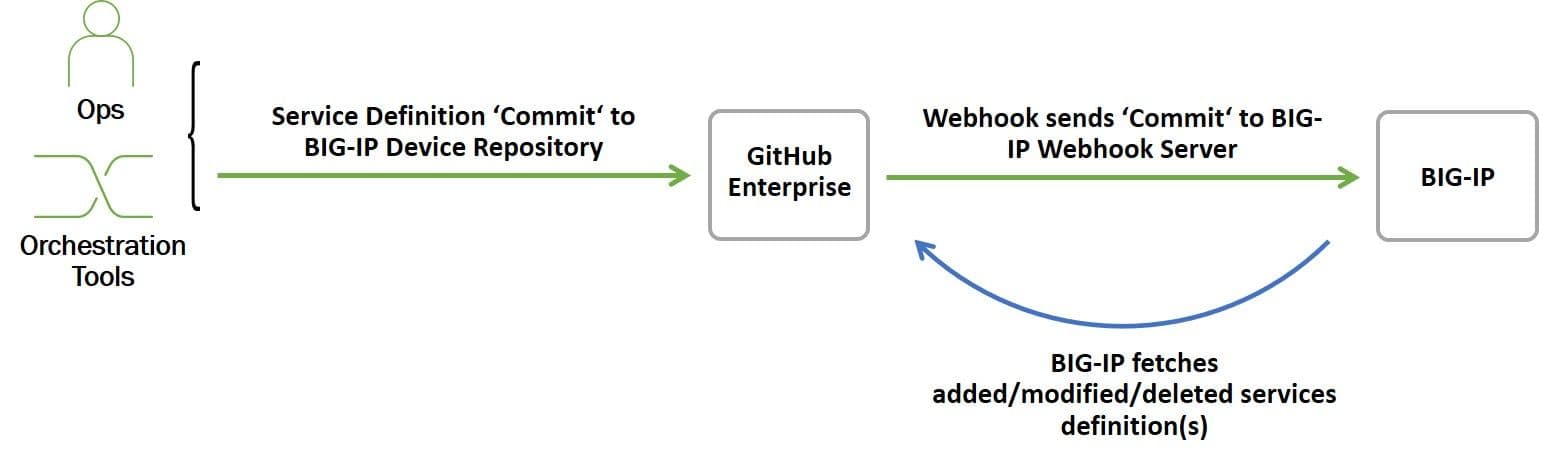
The ability to describe a BIG-IP configuration in this manner enables ops to adopt a configuration as code approach to deploying application services. By taking advantage of a repository, we can automatically pull AS3 configurations for deployment. In addition to automation uses, repositories provide a more modern and integration-friendly way to version and manage configurations and enable rapid rollback in the event of a problem with the configuration.
For example, using GitHub's Webhook capabilities, we can automatically kick off a deployment upon commit of a new/updated AS3 configuration. To do this, we need a Webhook server waiting for a notification that a new service definition (AS3) has been committed. These notifications come in the form of a hook, which is a JSON object containing information about the event. Once received, the Webhook server parses the hook and retrieves the referenced AS3 from GitHub and kicks off the configuration process.
You can download the latest version of AS3 on GitHub. Documentation on deploying the AS3 extension as well as example AS3 configurations are available here.
The Webhook prototype was developed by Nathan Pearce, Developer Advocate in the Office of the CTO. For more prototypes and examples of integrating BIG-IP with CI/CD and telemetry pipelines, you can follow Nathan and F5 Networks on GitHub.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
