What Is DDoS Mitigation?
Distributed denial-of-service (DDoS) attacks can threaten application availability, so it’s critical to have a DDoS mitigation solution.
Distributed denial-of-service (DDoS) attacks can threaten application availability, so it’s critical to have a DDoS mitigation solution.
Distributed Denial-of-Service (DDoS) attacks are a type of cyberattack that target specific applications or websites with the goal of exhausting the target system’s resources, rendering it unreachable or inaccessible to legitimate users. In 2023, application layer attacks are up by 165%, with the technology sector taking the top spot as the most attacked of all verticals. This is why having a comprehensive DDoS mitigation solution in place is critical to maintain uptime and resiliency.
Before diving into DDoS mitigation methods and solutions, it’s important to get a deep understanding of today’s DDoS threats. A distributed denial-of-service (DDoS) attack degrades infrastructure by flooding the target resource with traffic, overloading it to the point of inoperability. A DDoS attack may also send a specifically crafted message that impairs application performance. DDoS attacks can target network infrastructure such as firewall state tables, as well as application resources such as servers and CPUs.
DDoS attacks can have severe consequences, compromising the availability and integrity of online services and causing significant disruption, with the potential for financial losses and reputational damage. These attacks can also be used as a distraction so that bad actors can access important data.
DDoS attacks are a type of Denial of Service (DoS) attacks, which seek to disrupt the normal functioning of a network, server, or website by overwhelming it with traffic. On the other hand, a DDoS attack uses multiple devices to flood the target with traffic. Because a DDoS attack involves several systems attacking a single system, they represent a far bigger threat, and one that is more complicated to thwart.
These are the common types of DDoS attacks seen in the seven-layer Open Systems Interconnection (OSI) model:
Common attack vectors used in DDoS attacks:
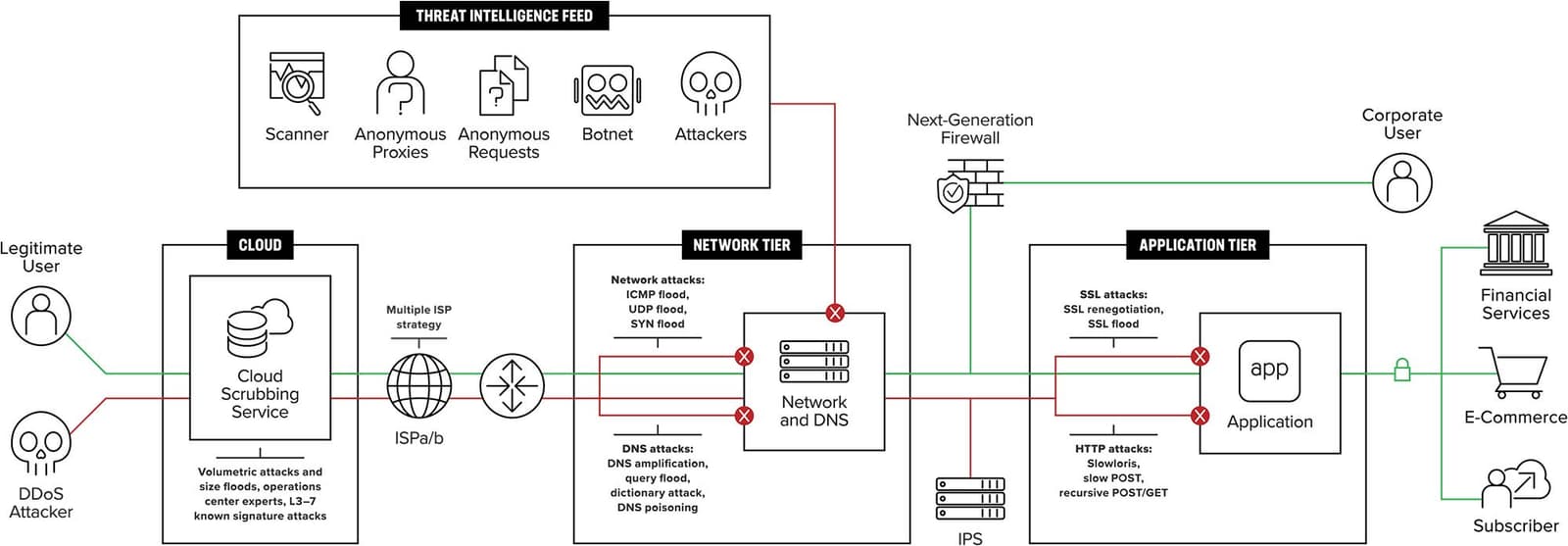
So the threat from DDoS attacks is enormous, potentially leaving companies more vulnerable to cyberattacks. That means it is essential to understand how DDoS attacks happen, so that you can take steps to mitigate them.
DDoS attacks can cause significant downtime and disrupt the availability of services, leading to financial losses and reputational damage.
Protection: By incorporating DDoS mitigation measures, your company reduces the risk of malicious traffic reaching their network infrastructure, while ensuring legitimate users can access their websites and web applications. DDoS attacks are sometimes used as a smokescreen to distract security teams from a coordinated attack campaign that can lead to data breach. And some types of attacks simply cannot be “coded” away.
Resilience: Investing in effective DDoS mitigation technology enhances an organization’s resiliency against nation-state adversaries and other malicious actors, making it a less attractive target.
Cost savings: Rapidly mitigating DDoS attacks can save organizations time and money.
By including DDoS mitigation in a cybersecurity policy, organizations can proactively protect their resources, maintain service availability, and minimize the impact of potential DDoS attacks.
Now we understand what is at risk in being vulnerable to DDoS attacks, including business-critical data and applications, and why it’s critical to deploy a DDoS mitigation solution. We can now review the types of DDoS mitigation so that you can determine the best solution for your needs.
There are several types of on-premises solutions and measures that an organization can implement to reduce the risk of DDoS attacks. Some of these may also be used in addition to cloud-based ones to build a stronger overall defense posture.
Moving DDoS mitigation efforts to the cloud or a hybrid solution helps increase efficiency, scalability, and efficacy. Some cloud-based solutions can be integrated with on-premises solutions. Cloud-based DDoS mitigation solutions operate on cloud-delivery networks, or CDNs.
Moving DDoS mitigation efforts to a hybrid solution can bring the best of public cloud security and private cloud or on-premises management. A hybrid model can allow businesses to further tailor their security posture to their unique data needs.
Apps are the drivers of modern business, but they are increasingly targeted for DDoS attacks. Traditional DDoS mitigation is static and centralized. But because apps are distributed across clouds and architecture, they need a DDoS mitigation solution that is scalable and flexible to offer maximum protection.
A comprehensive DDoS mitigation strategy typically includes several key components.
The first step in DDoS mitigation is detecting potential issues or risks. The two main methods of identifying and alerting on threats are signature-based detection and anomaly-based detection.
Signature-based detection relies on a preprogrammed list of known indicators of compromise (IOCs) to identify threats. These IOCs could include malicious network attack behavior, content of email subject lines, file hashes, known byte sequences, or malicious domains, among other issues. Signature-based detection has high processing speed for known attacks and low false positive rates, but it cannot detect zero-day exploits.
Anomaly-based detection, on the other hand, is capable of alerting on unknown suspicious behavior. Anomaly-based detection involves first training the system with a normalized baseline and then comparing activity against that baseline; once it detects something out of the ordinary, an alert is triggered. Anomaly-based detection can have higher false positive rates.
Protecting DNS resources is business critical. Two real-time traffic diversion solutions can help.
As traffic moves toward and through your network, you need a DDoS mitigation solution that is continually monitoring it for malicious activity.
When considering the right DDoS mitigation solution for your organization’s needs you will want to weigh the following factors with your business’s growth trajectory and possible risk surface in mind. And when and if you are considering a cloud service, you now have the option of choosing among several public clouds (AWS, Google Cloud, Microsoft Azure, and Alibaba Cloud) as well as private cloud companies.
A comprehensive DDoS mitigation solution helps cover your network preventively, with real-time incident response, and ongoing testing and review to ensure the highest performance.
Network architecture design: A well-designed network architecture can help prevent DDoS attacks by ensuring that the network is resilient and can withstand high volumes of traffic. For example, a network that is designed with multiple layers of security, including firewalls, intrusion detection systems, and other security measures, can help prevent DDoS attacks from penetrating the network. Additionally, network segmentation can help limit the impact of an attack by isolating affected areas of the network.
Load balancing: Load balancing can help prevent DDoS attacks by distributing traffic across multiple servers, which can help prevent any one server from becoming overwhelmed. This can help ensure that the network remains available even during a DDoS attack. Load balancers can also help detect and block malicious traffic, which can help prevent DDoS attacks from succeeding.
Detailed vendor SLAs: When considering a third party for DDoS attacks protection, it’s critical to understand the vendor’s capabilities in every DDoS scenario, and to have protocols, actions, and responses incorporated into the SLA.
DDoS incident handling steps: There are six key steps involved in responding quickly and effectively to a DDoS incident, though it’s important to state that these steps don’t happen in a linear fashion, but rather in a loop.
Communication protocols with mitigation provider during a DDoS incident: From the outset, it’s key for a company and its mitigation provider to follow a strict communication protocol. These are recommended best practices for communication during an incident:
IT and security teams should be doing analysis and testing regularly. One type of testing is red team testing, which involves simulating real-world attackers’ tactics and techniques. In this case, the red team testers would try out a variety of DDoS attacks to monitor the responses of the mitigation solution.
It’s also critical to stay up to date on trends in cyberattacks, especially as bad actors from around the world continue to change their methods. A mitigation solution should be scalable and adaptable to any new types of disruptions.
Organizations in any vertical, of any size, operating in any part of the world, can benefit from having a reliable DDoS mitigation solution in place. These case studies demonstrate how effective a DDoS mitigation solution can be in any scenario. Companies just like yours have seen measurable results from taking on DDoS risks.
While DDoS attacks have been around for decades, the bad actors who operate them are growing ever more sophisticated and aggressive. It’s important to be aware of current and coming trends in the DDoS area of cybersecurity.
At a high level, F5 has found these trends in 2023:
In addition, there are three growing areas that cybersecurity experts are keeping an eye on:
Artificial intelligence and machine learning: As more companies are deploying AI and ML in other parts of their businesses, like manufacturing or customer service, there are roles they can play in detecting and mitigating DDoS attacks. One recent study showed that using an artificial intelligence method to detect DDoS attacks resulted in more than 96 percent accuracy.
Internet of Things (IoT): IoT is growing, yet securing the additional compute surfaces involved can leave these solutions more vulnerable to attack. Experts suggest adopting more robust security practices, password protection, and using firewalls or VPS, all to reduce the number of devices at risk to attack.
Blockchain technology: Blockchain technology presents an interesting option for DDoS mitigation because by its nature, blockchain is decentralized and has secured distributed storage. That can help especially with geographic attacks, where security can also be targeted geographically.
While DDoS attacks are not going away, there are more tools to help mitigate those attacks both now and into the coming years.
Distributed Denial of Service (DDoS) attacks have been around for decades, and they are not going away. That’s why companies need to be thinking future-forward for their DDoS mitigation solutions. At F5, cybersecurity is front and center of virtually everything we do. Our DDoS mitigation solutions and stellar support give your organization the upper hand it needs in mitigating the risks of possible DDoS attacks. It’s also important to make sure your DDoS mitigation solution can scale and adapt to your company’s needs – and to the adapting threat of DDoS bad actors.
Let F5 help you in all the ways you and your network might need DDoS attack protection. We have deep experience in implementing the right type of DDoS mitigation for your organization’s needs.