The Lingering Threat
It has been over 18 months since the log4j vulnerability sent shockwaves through the cybersecurity community, yet recent reports indicate that a staggering 40% of log4j downloads are still vulnerable to exploitation and 72% of organizations are still vulnerable to log4j, as of Oct 1, 2022. In May 2023 alone our F5 Distributed Cloud Platform helped protect customers from over 1 million log4j attack attempts, which were successfully mitigated by the web app and API protection capabilities.
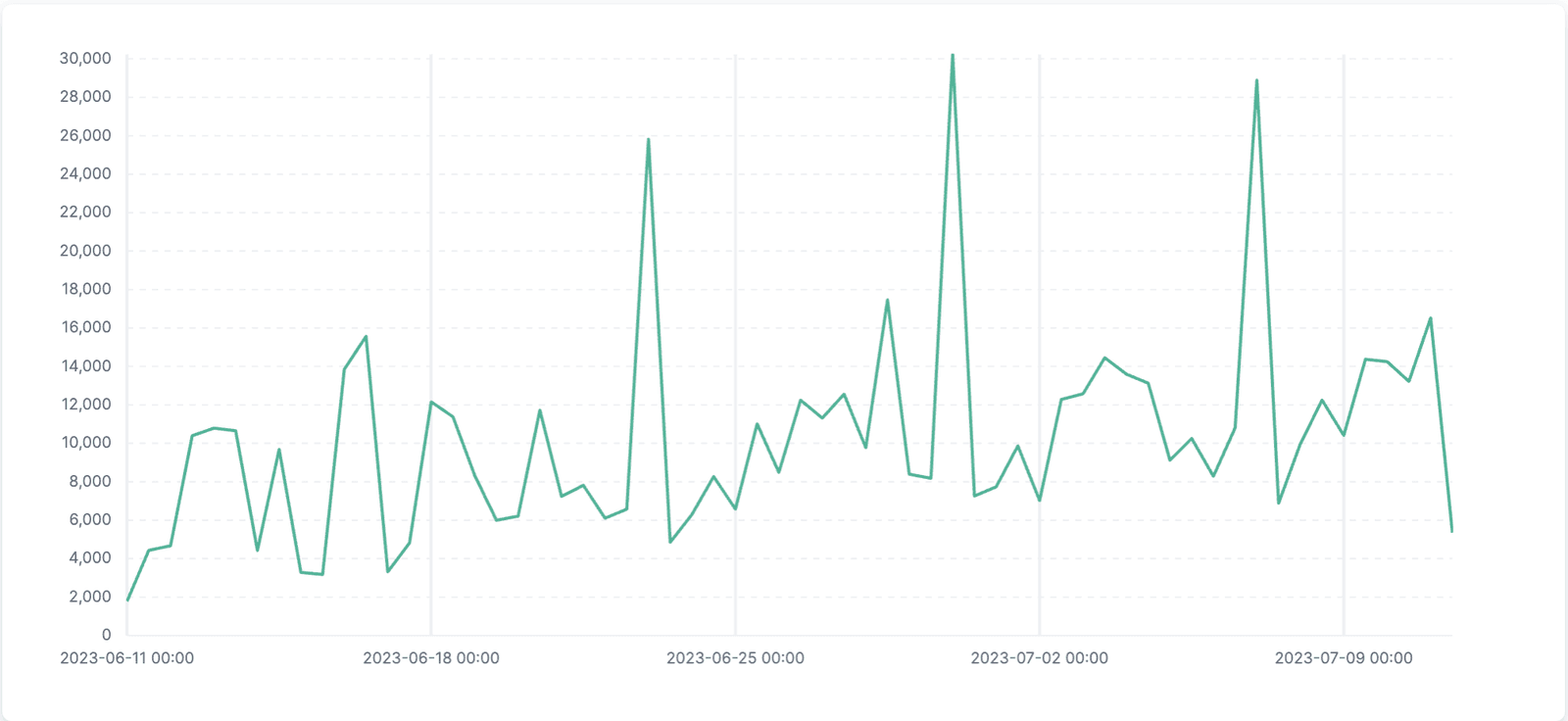
This is simply an example of one CVE highlighting the challenges that persist as organizations struggle keeping up with management of CVE remediation, and it’s a problem that is only going to continue to grow larger. The number of CVEs published is accelerating, and F5 Labs expects the rate at which new CVEs are going to be published in a typical week will balloon to 500 a week by 2025. It’s been almost 2 years since the log4j vulnerability was exposed, and organizations are still playing catch-up as the broader problem continues to evolve. Despite the availability of patches and updates, numerous factors contribute to persistent vulnerabilities like log4j.
Organizational Challenges
The sheer number and frequency of new vulnerabilities leaves organizations struggling to keep up (and possibly unaware) as they arise, either due to limited information or resources for staying up to date on new advisories. Once a vulnerability is identified, patching vulnerable systems can be complex, especially in large organizations with interconnected systems, requiring significant effort and coordination, leading to long patching cycles. This is made more complex by the mix of legacy and modern infrastructure, systems, and applications that exists in most organizations, which may create compatibility issues, high costs, or inconvenient time commitments when trying to implement critical updates. Further, complicated patching and updating are indirect dependencies that can exist within software supply chains or infrastructure components which may be a blind spot, even if an organization doesn't directly use the vulnerable system. Just like the software code itself, human error and oversight can also hinder mitigation efforts, as developers or administrators may overlook the need for patching or misconfigure systems. Lastly, organizations with complex IT infrastructures or risk-averse cultures may experience delays in adopting patches due to extensive testing, concerns about disruptions, or competing business priorities. Compounding all this complexity, most organizations are understaffed, especially in the security field. So, how are they supposed to keep up while they work feverishly to patch and update systems and applications?
Conclusion
Addressing vulnerabilities like log4j requires a collective effort from organizations, developers, vendors, and the broader cybersecurity community. Timely and comprehensive patching, improved awareness, robust vulnerability management practices, and continuous monitoring are essential to minimize the persistence of vulnerabilities and protect organizations from potential attacks. While patches are essential for addressing known vulnerabilities like log4j, they cannot guarantee complete protection as new vulnerabilities are constantly emerging. To effectively mitigate risks, organizations must adopt comprehensive security solutions. This includes implementing web application firewalls (WAFs) and API security measures to safeguard against application-level attacks. Additionally, continuous monitoring is crucial for detecting and responding to emerging threats promptly. By adopting a holistic approach that combines patching with robust security measures and continuous monitoring, organizations can better protect their systems and data from evolving security risks.
Patching happens, but often (like in this case with log4j) it doesn’t happen fast enough and there are new CVEs rapidly being identified, so it’s essential that organizations have a comprehensive layer of security in front of their applications no matter how patched and up to date they are. Protecting both internal and web-facing apps with a solution like F5’s Distributed Cloud Web App and API protection (WAAP) is crucial to fill the vulnerability gap while organizations work through their patch and update backlogs.
Some resources and related links:
- F5 Labs: The Evolving CVE Landscape – Plus the 7 Weirdest CVEs (You won’t believe number 6!)
- F5 Blog: Protection against the Apache Log4j2 Vulnerability (CVE-2021-44228)
- F5 DevCentral: Why We CVE
- CVE.org: Learn about the CVE Program Mission and More
- National Vulnerability Database (NVD): Stay Updated on Log4j-related Vulnerabilities and other CVEs
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.