Digital transformation continues to challenge the norms we are used to—from the concept of work itself to consumer expectations around what a digital experience entails. Organizations must maintain well-developed network capabilities that can deliver consistently high digital performance while keeping latency low.
While telecom service providers aggressively define and build out their next-generation network capabilities with 5G, certain areas will inevitably remain “notspots.” These locations that have zero or minimal network coverage create barriers for enterprises to deliver excellent digital experiences in these areas. Further, the growing demand for edge computing solutions, especially around increasing video demands, is placing pressure to deliver on these experiences while ensuring that networks are not overloaded.
To push the limits and boundaries in terms of the possibilities that edge computing can achieve in these respects, we partnered with SoftBank Corp. to test out an exciting proof-of-concept (POC) project.
Our goal was straightforward—demonstrate the viability of Multi-access Edge Computing (MEC) in a satellite communications environment, utilizing F5 caching technology to implement MEC and broadcast content in a bandwidth-limited communications environment.
Testing the limits of low-bandwidth environments
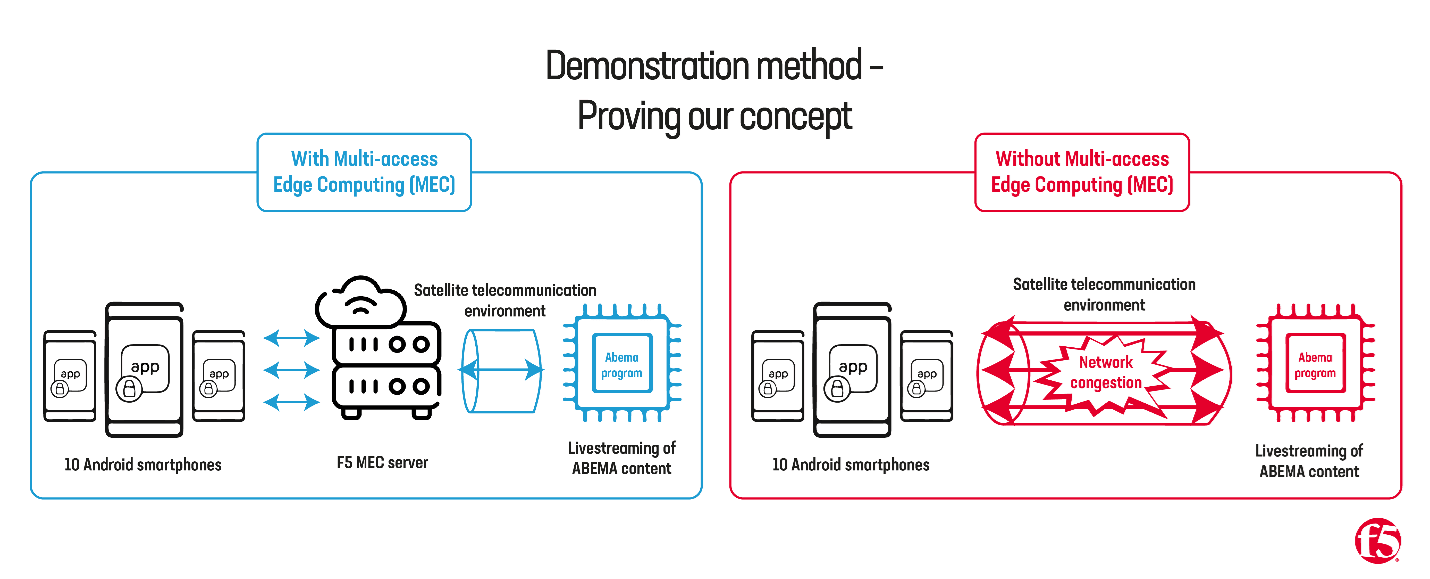
Bringing our concept to life, we worked with TV and video entertainment service, ABEMA, to run an ambitious broadcast event. We wanted to test if latency could be kept to minimum level despite increasing the number of simultaneously connected terminals with MEC.
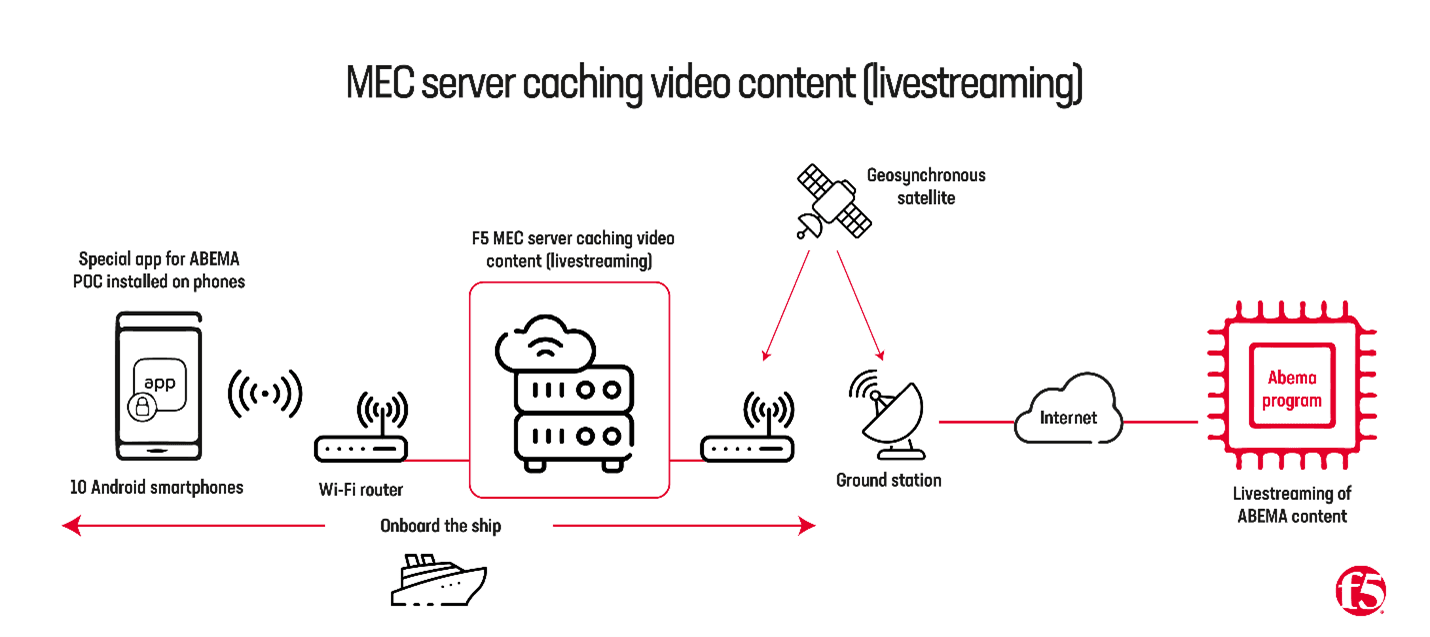
To truly test the limits of our capabilities, we set up a testbed on a ship, far out at sea—an extremely bandwidth-limited environment to broadcast a live video from ABEMA.
What we achieved was promising. It was a breakthrough in video broadcasting capabilities as previously this was not possible due to the challenges with low-bandwidth environments, such as remote areas where telecommunications services are unreachable.
In our experiments, we were connected simultaneously to more than 10 devices and terminals with a stable broadcast observed, and the load placed on the network behind MEC remained largely the same. It also reflected latency being kept to the minimum, despite an increase in the number of simultaneously connected terminals. For context, we created an onboard satellite telecommunication environment that could only view content on one to two smartphones simultaneously.
Even more improvements for Multi-access Edge Computing capabilities
While the prospect of being able to stream videos stably out at sea is promising, I’m even more excited at the possibilities to enable quick, reliable and secure delivery, of application content.
We have demonstrated that it is viable to enable application delivery in a bandwidth-limited satellite telecommunications environment, and not just that—we have made application delivery faster, smarter, and safer.
The proven viability of the concept opens the door to a growing list of use cases that enable more seamless user interactions. These solutions will become critical in today’s hyper-digitalized world, where organizations need to serve globally distributed applications with secure, optimized, and differentiated experiences. The possibilities are limitless: from the creation of smart cities to managing smart electric vehicle energy, immersive video-streaming, and more.
Moving into the next phase of edge computing
Computing now takes place at the network edge. By extending our application security and delivery to the edge, we can move compute and storage functions away from the core of the network and closer to end users and their devices to achieve better application performance and delivery.
Built on a new set of technology design principles and centered around holistic application distribution, Edge 2.0 will enable true portability of applications across dynamic environments. Geng Lin, our Chief Technology Officer sees Edge 2.0 as the new paradigm for solving the challenges facing tomorrow’s distributed applications. At F5, we are excited to see how it can advance our vision for adaptive applications and, ultimately, provide a superior digital experience for customers.
As we enhance our F5 portfolio, we are primed to provide customers across different industry sectors with the best-in-class, tailor-made solutions. Further, with the success of this proof-of-concept with SoftBank Corp., I look forward to continuing our collaboration to develop solutions that extend the reach of MEC technology.
About the Author
Related Blog Posts

Build a quantum-safe backbone for AI with F5 and NetApp
By deploying F5 and NetApp solutions, enterprises can meet the demands of AI workloads, while preparing for a quantum future.

F5 ADSP Partner Program streamlines adoption of F5 platform
The new F5 ADSP Partner Program creates a dynamic ecosystem that drives growth and success for our partners and customers.

Accelerate Kubernetes and AI workloads with F5 BIG-IP and AWS EKS
The F5 BIG-IP Next for Kubernetes software will soon be available in AWS Marketplace to accelerate managed Kubernetes performance on AWS EKS.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
F5 Silverline Mitigates Record-Breaking DDoS Attacks
Malicious attacks are increasing in scale and complexity, threatening to overwhelm and breach the internal resources of businesses globally. Often, these attacks combine high-volume traffic with stealthy, low-and-slow, application-targeted attack techniques, powered by either automated botnets or human-driven tools.
Phishing Attacks Soar 220% During COVID-19 Peak as Cybercriminal Opportunism Intensifies
David Warburton, author of the F5 Labs 2020 Phishing and Fraud Report, describes how fraudsters are adapting to the pandemic and maps out the trends ahead in this video, with summary comments.