When new ways of interacting with business logic are introduced, they have a dramatic impact on how applications are designed, deployed, and ultimately delivered.
The web browser, for example, was the driving force that broke up monoliths and gave us what built the Internet as we know it: three-tier web applications. The primary interface quickly became a GUI that was far easier to navigate than its green-screen, command line predecessors.
That interface is changing again, thanks to generative AI. And this time, the impact is going to be huge.
““The way we use the internet is about to change in a big way. … Instead of jumping from website to website, we’ll soon be able to simply 'chat with the internet' to get what we need.”— Laurent Querel & Gilad Bracha, Transforming the Web: The End of App Silos”
Indeed, replacing the graphic interfaces we’ve come to love—and sometimes loathe—is a new way to interact with applications: the conversational interface.
Enabled by the ability of generative AI to parse and seemingly understand our requests, the natural language interface is quickly becoming “the way” to conduct business with your customers.
Aside from radically changing the user experience, this shift has significant consequences on the technical details of how developers build applications, how applications communicate, and how we deliver and secure those applications.
Three Key Changes
There are three key technical changes in generative AI applications driving change in other domains.
Interaction Patterns
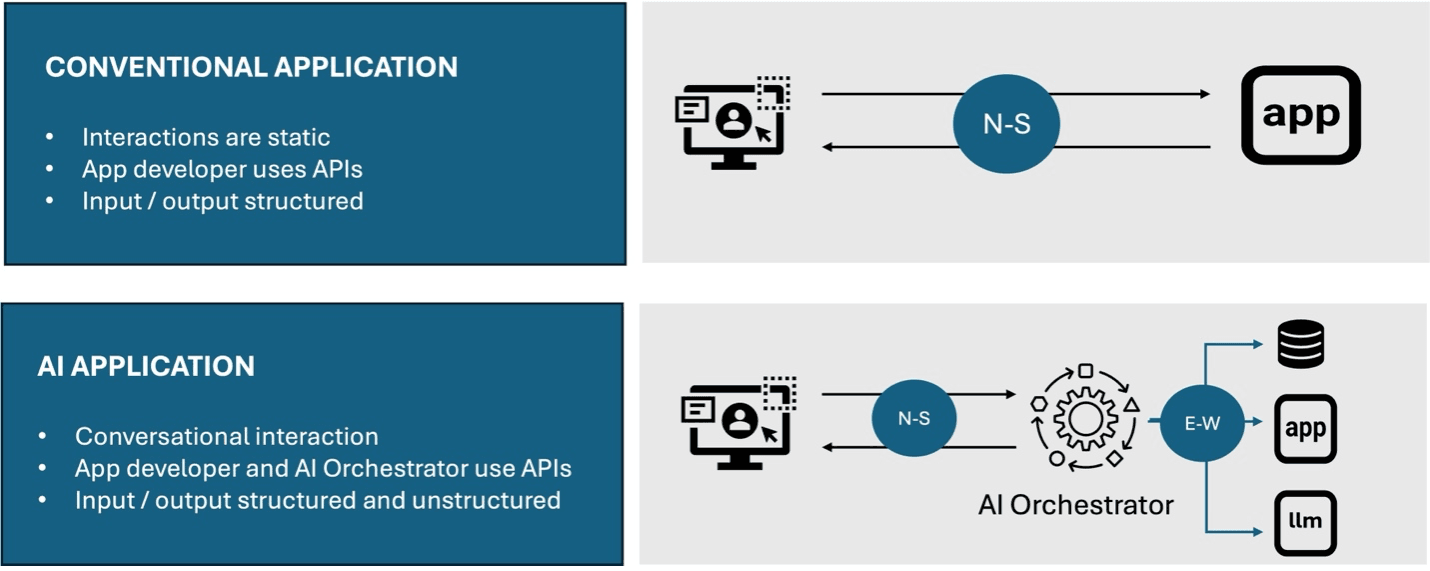
Interaction patterns describe the way traffic flows back and forth between a user and the application that processes requests. With conventional applications, these interactions are static. That is, we know what each page and API request is going to be sending and receiving. We define what data can be exchanged, and we can limit the type and size of that data as part of our security efforts.
With conversational applications that pattern changes. The conversation might be quick and short, it might be long with lengthy requests. As multimodal AI continues to add new types of data to generative AI’s capabilities, the conversation might include images, audio, or video. It might not. We just don’t know. That makes it difficult not just to secure, but to understand how to scale and optimize for performance. We can no longer predict resource consumption because, well, it’s highly variable and dynamic.
The impact on app delivery
Traditional means of scale via ingress control, Gateway API, and load balancers at the local and global levels, must become more dynamic themselves. These critical components of every enterprise architecture today will need greater visibility and understanding of application and user behavior in real time and be able to make decisions about forwarding of requests based on more current conditions, rather than mostly static algorithms.
Application Development
Second, application development will change. When developers build conventional applications, they use APIs. But the primary traffic pattern was what we call “North South.” That is, the most significant traffic—and security—needs were at the application public-facing “front door.”
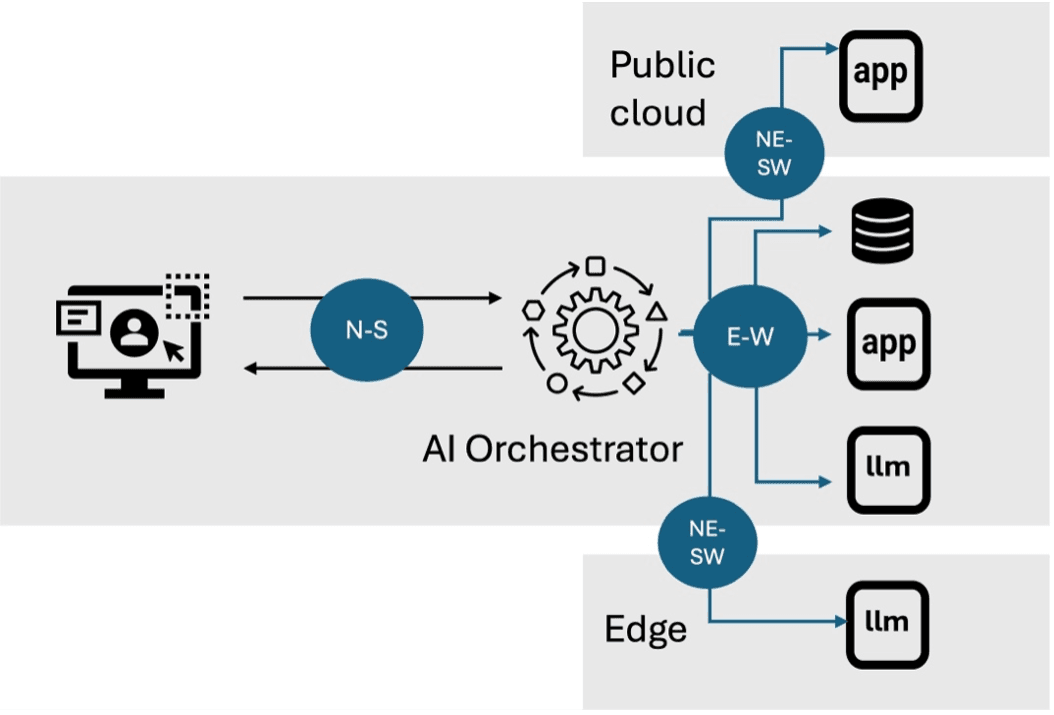
Generative AI applications will still see developers leveraging APIs. But so will the AI Orchestrator, which is a fancy way to describe an application proxy capable of receiving user requests and, after parsing the request, invoke the right services via well-defined APIs. These will be bespoke services, some will be offered by providers, and others will be various instances of LLMs. This will see a significant increase in “East West” traffic as the AI orchestrator talks to services that are effectively components of the “AI application.”
The impact on app delivery
There will still be significant N-S traffic with conversational applications, but there will be increased traffic and need for delivery and security inside, on the “East West” data path. This will require application delivery and security to expand from watching the front door to watching all the doors of a house, inside and out.
The prevalence of multicloud estates, with application components sprawled across core, cloud, and edge, will further require that app delivery apply its N-S capabilities to what is quickly becoming the NE-SW data path that covers inter-location traffic using secure multicloud networking methods.
Input and Output
Lastly, and perhaps most obvious, is the shift from structured input and output to unstructured. For most of technology’s history, we’ve relied on structured input and output to design everything from networks to databases to applications.
That’s all changing. Input and output are now “whatever the user felt like” and developers can’t count on data types or lengths any more than security ops can build policies based on expected input and outputs. This is a radical change in how applications communicate, and it will have a dramatic impact on app delivery and security.
The impact on app delivery
The biggest impact from unstructured data processing is in security. We’ve relied on understanding how attackers can exploit existing data structures and logic because there was a clearly defined set of vulnerabilities that arise from the way structured data is processed.
Given a nearly infinite array of possibilities with natural language, it becomes incredibly difficult to identify attacks because the threat surface moves from the lexical (syntactical) to the semantic (context and meaning). That requires a different way of inspecting and evaluating requests and responses. This is why AI is quickly becoming one of the best tools in the security toolbox; because its ability to understand natural language and analyze vast quantities of data provides insights into anomalies and outliers that can be indicative of an attack.
It also drives data security techniques into the app security domain, requiring that app and API security also inspect and evaluate input and output from a data security perspective.
Generative AI Changes Everything
There is virtually no domain that is not already or will shortly be impacted by the adoption of generative AI. Changes to applications may be welcomed by users but will pose challenges to security and delivery professionals as solutions shift to incorporate new traffic patterns and needs and understand the new threat surface.
Generative AI changes everything, because it changes everything about applications.
About the Author

Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.
