Application DDoS
Low and Slow Attacks, Asymmetric Attacks, SlowHTTPTest, Slow Loris, POST and GET Floods
Is your website slower than it should be?
Do your users report frequent login problems, search timeouts, or unexplained database failures? You may be the victim of application-level distributed denial of service (Application DDoS). Application DDoS has been one of the most pernicious problems in computer science for the last ten years. It goes by other names: “low and slow” attacks, “layer 7 DOS” attacks, and asymmetric attacks.
20 Million
A MAJOR INSURER WITH MORE THAN 20 MILLION MEMBERS RELIES ON ITS WEBSITE TO DELIVER INFORMATION ON PROVIDERS, BENEFITS, AND PLANS.
Competitor Uses DDoS to Mask Scraping
A major insurer with more than 20 million members relies on its website to deliver information on providers, benefits, and plans. An attacker flooded the insurer’s search function with queries for multiple days, bringing the site to its knees.
F5 Distributed Cloud researchers observed low-level automated scraping activities co-morbid with the denial-of-service attack, suggesting the DoS attack may have been a diversionary tactic.
Case Study: Insurer Defeats Application Layer DDoS
Key points:
- Insurer’s services are highly personalized, so website search is an essential function.
- Adversary used a simple command-line tool to exercise the search function at a rate sufficient to cause it to fail.
- F5 Distributed Cloud deflected application DDoS, and uncovered competitor-rate scraping.
The Application DDoS Attacker’s Playbook
Step 1
The attacker, be it competitor, extortionist, or activist, will reconnoiter your website using a spidering service—slowly, over days or weeks to avoid detection. They build a list of URLs with amount of time that each query takes and the amount of data returned.
Step 2
The attacker will then order the list by time-to-complete or file size and repeatedly request the first URL on the list, 100 times a second or more. Their small GET requests cost them nothing to launch, but a 5-megabyte PDF file, or expensive database query launched 6,000 times in a minute, can cause havoc on an undefended website.
Step 3
If the defender blocks requests to the target object, the attacker merely targets the next URL on the list. The defender almost never knows which URL it will be. If the URL is a database query, the repeated requests can take down the entire database, bringing business to a halt.
How F5 Distributed Cloud Fixes Application DDoS
At F5 Distributed Cloud, we’ve seen nearly every kind of application-layer DDoS attack imaginable. A simple attack may involve your competitor taking down your website by repeatedly invoking your slowest database search. For some retailers, the slowest search can be a store locator. For others, it can be an unindexed “select all” query. Because each small request on the part of the attacker can draw vast resources at your website, the attacker doesn’t need to send a large attack—just a steady stream of small GET requests. These “low and slow” DDoS incursions will not set off bandwidth trigger alarms.
Application DDoS attackers rely on automation—scripts, programs, and botnets—to carry out their DDoS attacks. Traditional DDoS defenses are usually blind to these kinds of attacks, because the attacks are almost always carried out over encrypted SSL channels.
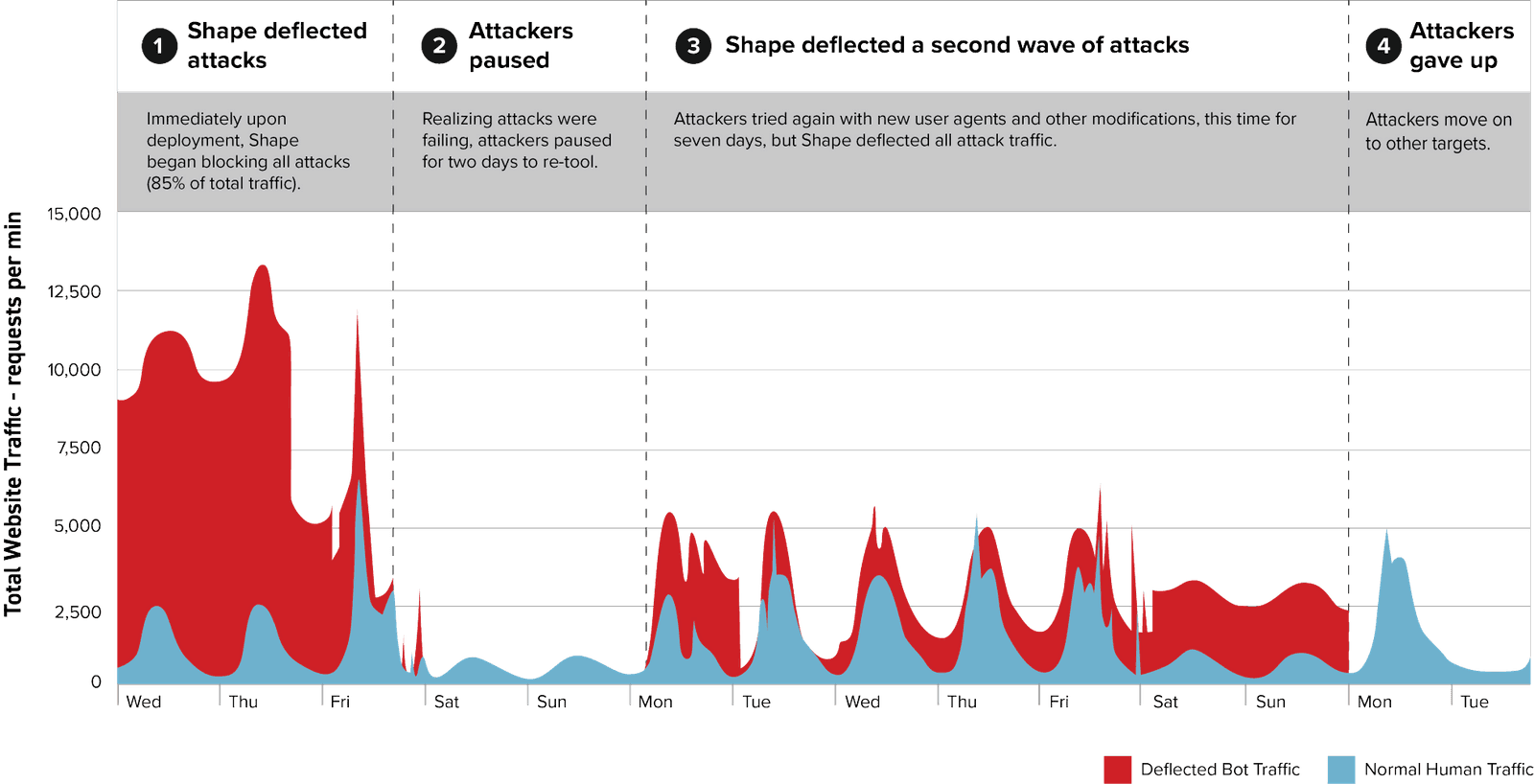
The diagram above is representative of the traffic recorded by the F5 Distributed Cloud Protection Manager, and it shows attack traffic directed at an insurer’s website. Red indicates traffic reaching the origin servers before F5 Distributed Cloud is activated. Gray indicates traffic deflected by F5 Distributed Cloud that does not reach the origin servers. The chart illustrates a typical app layer DDoS attack pattern that continued even after F5 Distributed Cloud mitigated its damaging effects.
At F5 Distributed Cloud Security, we can see the attacks, detecting them like we do any other automation. We know when the attacking client is not a true browser, and we limit them, redirect them, or use controlled blocking to minimize their impact. Sometimes we turn the tables on the attacker and slow their queries, making them think they are succeeding when they’re not.
F5 Distributed Cloud specializes in telling humans and computers apart, and Application DDoS is just another bot symptom of the same threat vector we handle billions of times per week.