Secure remote access safeguards sensitive data transmission when applications are accessed from devices outside of the corporate network.
Secure remote access is an umbrella under which a number of security strategies reside. It can refer to any security policy or solution that prevents unauthorized access to your network or sensitive data.
With the proliferation of internet-connected devices, an organization’s workforce is no longer sequestered to a single location. Instead, an organization may have employees connecting to their internal network and accessing sensitive data from locations across the globe. Because of this, old access security measures are no longer enough and must be replaced with safeguards that allow employees and other verified users safe and secure access from anywhere, on any device, at any time.
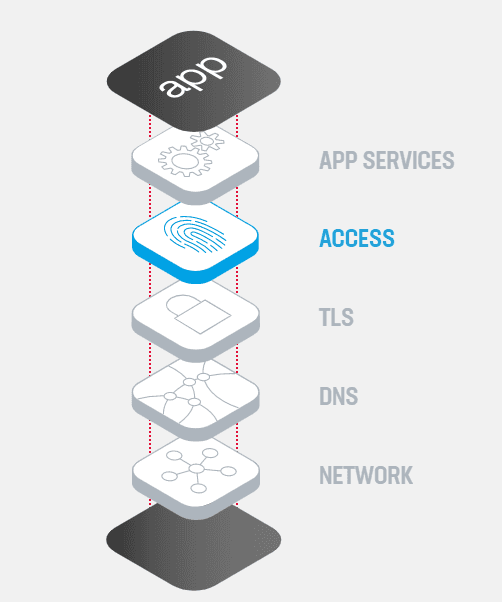
Secure remote access is a crucial part of any healthy application stack, working with other elements such as DNS and TLS to ensure your applications are continuously secure and performant.
With the proliferation of internet-connected devices, an organization’s workforce is no longer sequestered to a single location. Instead, an organization may have employees connecting to their internal network and accessing sensitive data from locations across the globe. Because of this, old access security measures are no longer enough and must be replaced with safeguards that allow employees and other verified users safe and secure access from anywhere, at any time, from any device.
There are several types security solutions and technologies that fall into the category of secure remote access, including (but certainly not limited to):
F5 has a host of access security solutions purpose-built to keep good traffic flowing and bad traffic out. BIG-IP Access Policy Manager (APM) lets you create identity-aware, context-based access policies, implement an SSO solution, and create an SSL VPN.