Machine learning (ML) is a subset of artificial intelligence (AI) that enables computing systems to recognize patterns in vast amounts of data and uncover insights, make predictions, and automate decision making. Instead of being explicitly programmed for each new task, ML models recognize trends or anomalies to improve model performance over time, adapting to new information and inputs without the need for human intervention.
ML’s ability to detect hidden structures and patterns in data flows makes it a valuable cybersecurity tool: It can automate threat detection, improve response times, and uncover hidden risks beyond the ability of human observers or of security alert systems based on predefined rules.
Incorporating ML into cybersecurity is especially important today due to the evolving complexity, scale, and speed of modern cyberthreats. Today’s threats, particularly previously unknown or zero-day exploits, can evade conventional security policies based on static, predefined rules and dated threat signatures. In addition, IT resource constraints in many organizations are stretching in-house security teams thin, leading to slower response times and increased human error in detecting cyberthreat activity. The nature of security threats is also evolving and dynamic, with criminals making use of AI and automation to launch sophisticated attacks that can unfold in seconds and adapt to bypass traditional defenses.
The use of ML and AI to support cybersecurity is on the rise, according to surveys conducted for the 2025 F5 State of Application Strategy Report. According to respondents:
- 59% of businesses use AI to mitigate zero-day vulnerabilities by automatically injecting security rules.
- 51% want to use generative AI to automatically adjust security policies, workflows, and configurations to respond to threats or new vulnerabilities.
- 99% are comfortable using AI not just to support decision making but to automate at least one operational function.
This post explores how ML models work and the ways they are transforming the field of cybersecurity. It will examine the key benefits ML brings to security operations, including its role in detecting and preventing a wide range of cyberattacks. Additionally, the post will address common challenges and misconceptions about ML, helping to clarify what it can—and cannot—do to enhance cybersecurity defenses.
How does machine learning work?
There are three major types of ML models:
Supervised machine learning involves training a model on data that has already been analyzed and labeled by a human so it can learn the patterns that predict the labels and then recognize those patterns in new data. Supervised learning is good at classifying data and recognizing particular patterns specific to certain types of threats, such as distributed denial-of-service (DDoS) attacks.
Unsupervised machine learning involves training models on unlabeled data, allowing the model to find hidden patterns, structures, or groupings in the data on its own and define these clusters of characteristics. This form of ML is good at detecting new and complicated attack patterns, detecting anomalies in incoming traffic, and mitigating zero-day attacks.
Reinforcement machine learning uses trial and error to iteratively improve the model’s approach to making decisions based on rewards and penalties, continually trying new approaches to maximize the reward. This ML model is good at detecting a wide range of cyberattacks and improves its efficiency over time.
How machine learning is transforming cybersecurity
ML is increasingly applied across a wide range of cybersecurity functions due to its ability to automate complex tasks, identify patterns in massive datasets, and detect evolving threats in real time.
It contributes greatly to cyber threat intelligence by generating actionable insights from large and varied data sources, such as logs, dark web content, and threat reports, to identify emerging attack trends, threat actor behaviors, and indicators of compromise. ML models excel at anomaly detection, as they learn what constitutes normal behavior for users, devices, or applications and can detect deviations that may signal breaches, insider threats, or misconfigurations.
Similarly, machine learning can inspect network traffic flows in real time to identify suspicious patterns, such as command-and-control communications, data exfiltration attempts, or lateral movement within the network. This is crucial for detecting advanced persistent threats that evade signature-based detection.
Risk scoring is another cybersecurity tactic enabled by machine learning. ML algorithms can assess and prioritize risks by analyzing multiple data points—such as user behavior, asset sensitivity, and threat likelihood—to produce dynamic, context-aware risk scores based on the threat’s potential impact on an organization. This is especially important when detecting bots and malicious automation, as attackers will attempt to spoof telemetry signals to disguise their campaigns as legitimate traffic. For instance, they might rotate IP addresses, use different autonomous system numbers (ASNs), which are identifiers for Internet networks, or change browser user-agent strings to avoid detection. ML helps to spot these deceptive tactics by identifying subtle, unusual patterns across multiple data points that humans or rule-based systems might miss.
Machine learning is also highly valuable for malware detection, as it offers dynamic capabilities that go beyond static, signature-based security methods. ML enables faster, more adaptive, and more accurate identification of both known and unknown threats, includingpreviously undetected malware, including zero-day and polymorphic variants.
Machine learning is increasingly used to automate elements of penetration testing, where security professionals conduct simulated cyberattacks to identify vulnerabilities in a computing system or platform. ML can reveal exploitable paths, explore vulnerabilities, or simulate attacker behavior with the goal of uncovering weaknesses before real attackers can exploit them.
These ML use cases fall into three broad categories:
- Detecting threats faster and with greater accuracy. Security solutions that leverage aachine learning enhance the speed and precision of threat detection by analyzing large volumes of data in real time to spot anomalies, suspicious patterns, or known indicators of compromise. ML algorithms learn what constitutes normal user or system behavior and flag deviations that may indicate malicious activity so it can be addressed in real time.
- Proactively finding and patching network vulnerabilities. Identifying weak points before they are exploited by attackers is key to proactive threat management. ML-supported security tools can use threat intelligence, simulation, and modeling to score and prioritize vulnerabilities for rapid remediation.
- Improving IT efficiency by automating repetitive tasks. While many cybersecurity operations are repetitive and time-consuming, ML can help automate these tasks, increasing the speed and consistency of security operations and allowing security teams to focus on strategic planning and decision-making.
Benefits of machine learning in cybersecurity
The primary benefit of incorporating ML models into cybersecurity is the ability to analyze massive quantities of diverse data—such as network traffic, user behavior, system logs, and threat intelligence—at speed and scale far beyond human capacity. Machine learning excels at identifying complex patterns, correlations, and anomalies in real time, allowing security systems to detect and respond to threats earlier in the attack lifecycle, often before significant damage occurs. Additionally, ML algorithms continuously improve as they ingest more data, making detection smarter and more adaptive over time.
For businesses, this means stronger security postures, as ML-enabled solutions can help automate security policy updates, expose existing weak points, proactively remediate vulnerabilities, and reduce the possibility of human error introducing a weakness or misconfiguration. Secuity solutions that use ML also allows businesses to adapt faster to the evolving cyberthreat environment by detecting new threats quickly and adjusting defense systems proactively. Improved IT productivity is another benefit of incorporating ML into cybersecurity systems. By automating most threat detection and mitigation efforts, these systems free up human IT resources to work strategically and augment their tactics with real-time insights and threat intelligence.
Machine learning challenges
To gain the full impact and benefits that ML can bring to cybersecurity requires access to high-quality data and telemetry, as these are the fuel that drives accurate, adaptive, and effective models. Without access to automated sources of data, ML systems cannot continue to learn, improve, or provide meaningful insights. For many organizations, providing these automated data flows is a challenge.
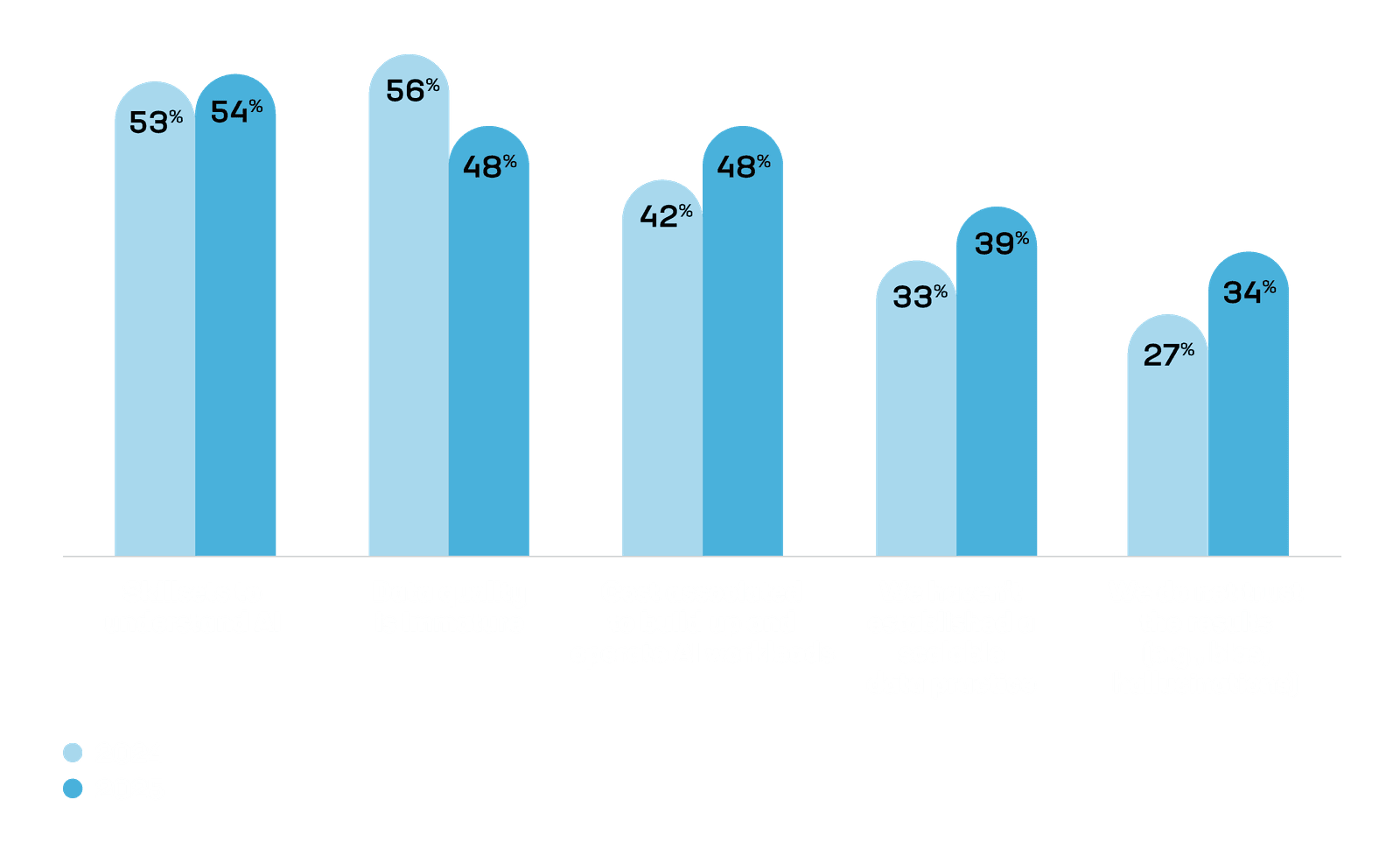
Challenges that organizations face when implementing AI (from the 2025 F5 State of Application Strategy Report)
According to the 2024 F5 Digital Enterprise Maturity Index Report, a primary measure of automation capability is the degree to which a digital business is driven by data with minimal human intervention. Yet only about 45% of businesses surveyed in the report have automated network security, and 40% have automated application and API security functions, so the report finds there is massive opportunity for improved data automation and security.
Nearly 50% of respondents to the 2025 F5 State of Application Strategy Report claim that data quality issues were a top challenge to adopting AI, as training machine learning models requires large volumes of data, and many organizations don’t have enough of it. Cost was citedas another top challenge to AI adoption. Though ML may lead to efficiency gains in the future, there are significant upfront costs to implementing it.
The greatest challenge that businesses face in adopting machine learning, according to 54% of the State of Application Strategy Report respondents, is the lack of skilled employees to successfully implement and manage AI deployments. Maintaining machine learning models and knowing how to interpret the results is a requirement when incorporating ML into cybersecurity, but a significant talent shortage persists, with some 3.5 million unfilled cybersecurity positions in 2025.
Machine learning myths
As with many popular and on-trend topics, misconceptions abound about AI and ML:
- Myth 1: Machine learning can automate any task. In reality, ML is not a one-size-fits-all technology. It requires large, high-quality datasets and ongoing model training to remain effective. Without sufficient and continuous data, a model’s performance can degrade over time. Additionally, the cost and effort to develop and maintain an ML model may not be justified for low-value or narrowly scoped security tasks, where traditional rule-based systems may be more practical and efficient.
- Myth 2: Machine learning-enabled solutions will fully replace human security analysts. Machine learning is a powerful tool, but it cannot operate effectively without human oversight. Skilled cybersecurity professionals remain essential to interpret results, provide context, and make judgment calls that ML models cannot. Human analysts are needed where critical thinking, experience, and intuition are required—capabilities that machines do not possess.
- Myth 3: Machine learning will make cybersecurity defenses impenetrable. While machine learning can significantly enhance cybersecurity, cyber attackers are also adopting AI and ML to develop more sophisticated, evasive techniques. Additionally, AI models are not impervious to cyberattacks—such as data poisoning, where adversaries manipulate the training data to mislead the model. As threats continue to evolve, cybersecurity defenses must be constantly monitored, updated, and complemented by human expertise to remain effective.
Getting started with ML in cybersecurity
Machine learning brings speed, scale, and proactive adaptability to cybersecurity, making it a key component of modern digital security strategies, particularly for applications and workflows that involve large datasets.
When evaluating cybersecurity solutions, be sure to ask vendors how they’re leveraging ML in their platforms—not just whether they use it, but how it’s implemented, what types of data it requires for optimal processing, and what outcomes it delivers. Inquire whether the ML models are trained on diverse, real-world threat data and how frequently the datasets are updated.
For almost two decades, F5 has employed machine learning across its application security and delivery products. For example, F5 Distributed Cloud Bot Defense uses both supervised and unsupervised ML models to analyze billions of signals per day and dynamically update bot mitigation strategies.
Finally, don’t assume that ML will solve all your cybersecurity challenges. Your organization will always need skilled cybersecurity professionals, so continue to invest in and support them. With the talent shortages in the IT industry, you don’t want to lose the skill sets you already have.
For more information about best practices and emerging trends in cybersecurity, read this glossary entry. Also, be sure to catch all the latest F5 AI news on our Accelerate AI webpage.
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.