BRIEF
Automating Cybercrime with Sentry MBA

Anatomy of a Sentry MBA attack:
- Targeting and attack refinement.
- Automated account checking.
- Monetization. Sentry MBA (and the criminal ecosystem that supports it) dramatically improve criminal productivity during the first two phases.
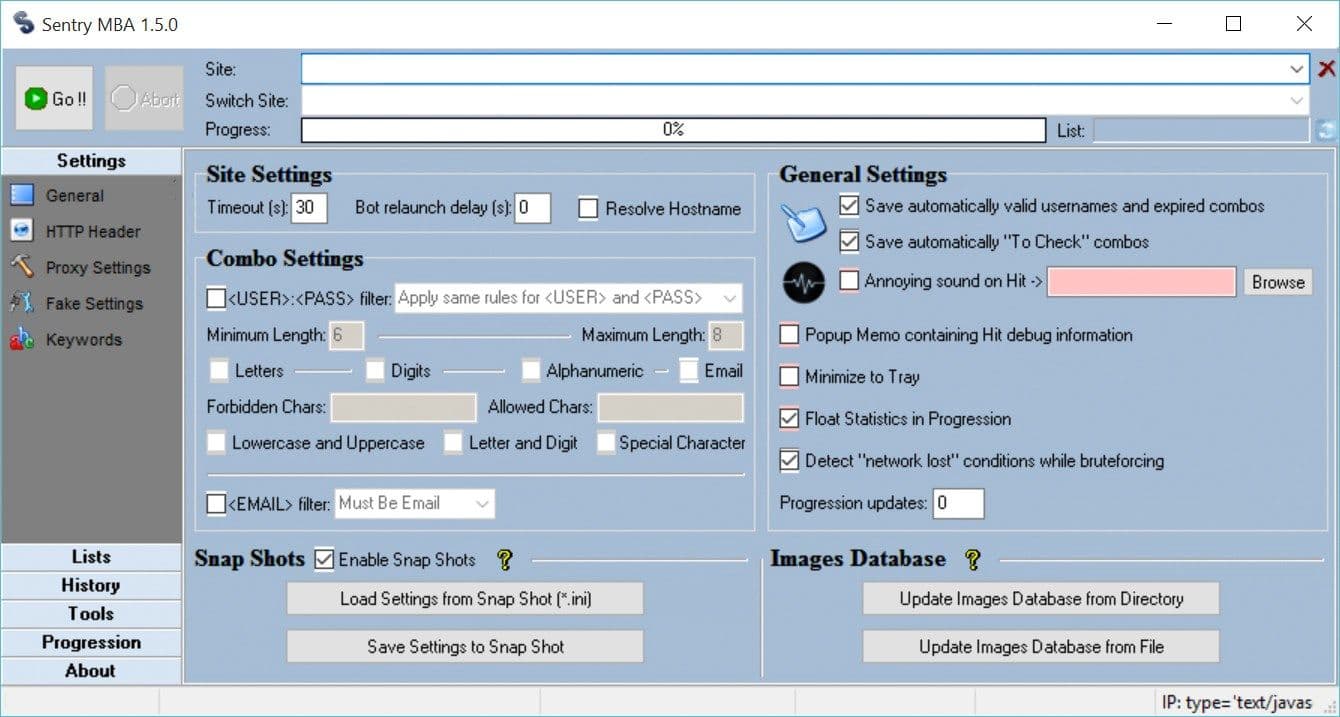
Using Sentry MBA in Credential Stuffing Attacks
A list of usernames and passwords is at the heart of every Sentry MBA attack. In Sentry MBA parlance, these are called “combo” lists. If the combo list has credentials that were valid on another website (e.g. via publicized breaches at eBay, Sony, and Ashley Madison or through phishing techniques), the attack is called “credential stuffing.” Credential stuffing works because Internet users routinely reuse passwords across web accounts. Verizon’s 2015 data breach report cites the use of stolen credentials as the most common attack action used against web applications today.