Nearly every organization worldwide is moving toward digital transformation. A transformation that’s driven by the need to collect and transmit sensitive data—user data, customer data, patient data, and corporate data. In short, our lives today revolve around data. Keeping it private and secure is essential.
Applications are the gateways to data. So, securing apps, wherever they reside, is critical to an organization’s security and their business, regardless of industry.
The security and privacy of sensitive data is so important that new governmental rules and regulations are being created to ensure data security and privacy within organizations. And those rules apply regardless of whether the organization or the data collected is located within the borders of the governing entity or not.
The European Union’s (EUs) General Data Protection Regulation (GDPR) requires organizations operating within the EU to make sure personal data is collected legally, with the prior approval of the individual, and it must be protected. In the U.S., the new California Consumer Protection Act (CCPA) mirrors many of the GDPR protections and is being evaluated by other states as a model for consumer privacy protection legislation.
These rules and regulations are designed to create transparency and give customers more control over their personal data and how it’s handled after it’s collected. If an organization experiences a security breach and sensitive data is lost or stolen, misused or exploited, the breached organization may be heavily fined.
Encryption is considered a best practice, at minimum, for protecting sensitive information. In fact, failure to protect data using encryption is considered negligent. However, encryption has two sides.
There are several ways to ensure the security and privacy of data, but the best way is encryption.
Most traffic today is encrypted. Nearly all web sites use encryption. The fast growth and continued adoption of online productivity apps like Microsoft Office 365 and Google G Suite, cloud-based applications, software-as-a-service (SaaS) apps, and social networks have helped drive the continued growth of encrypted traffic.
Encrypting data is great for ensuring and maintaining its privacy and integrity.
However, there’s a dangerous downside to encryption: attackers have realized encrypted traffic is an excellent way of delivering malware and other malicious payloads to unsuspecting users and their organizations, as well as a great way to extract stolen data from users and organizations.
At a minimum, ensuring against threats hidden in encrypted traffic requires that organizations have visibility into both incoming and outgoing encrypted traffic. Visibility into and inspection of encrypted incoming traffic reduces security blind spots. It also mitigates the risk of malware concealed within encrypted traffic and the vulnerabilities that lead to breaches of sensitive data.
Visibility into encrypted outbound traffic is also important because that traffic can mask exfiltration of stolen data. It can also mask communications launched by malware already entrenched within a network or cloud environment to command-and-control (CnC) servers that can trigger attacks or attempt to download and extend existing malicious software into a multi-tier, multi-threaded attack.
Attackers can also download additional malware and move laterally within an organization or even extend beyond the original organization to attack their customers or supply chain, infecting more devices and servers and stealing more information and data.
SSL visibility is only the start, though. Organizations need better control over both encrypted and decrypted traffic—but not at the expense of their security solution’s capabilities.
Many organizations invest significantly in their security solutions, selecting high-value features to perform specific functions like exploding malware, sandboxing, and denylisting applications and web properties—just to name a few. While security solutions may include native decryption capabilities, decryption and encryption aren’t their core purpose or focus.
Without a dedicated solution designed to perform decryption at scale, SSL visibility requires that encrypted traffic be routed by most enterprises through an end-to-end chain of security services. In essence, it must go through the static daisy chain of a repetitive, redundant, process of decrypt/inspect/re-encrypt across the entire security stack.
This process isn’t only inefficient, it also consumes precious time and resources. It can also add latency, impacting user experience. Plus, each of the security devices daisy-chained together will need to scale uniformly to meet the total encrypted traffic capacity, which can easily lead to over-subscription. And that means increased costs for security services.
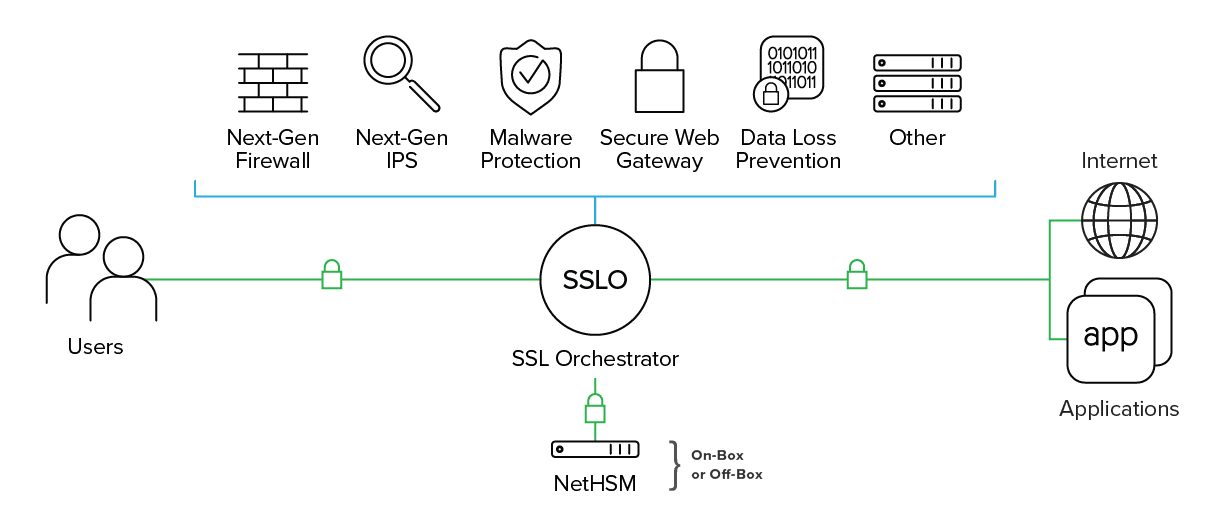
F5 SSL Orchestrator ensures encrypted traffic is decrypted, inspected by the appropriate security controls, and then re-encrypted, delivering visibility into encrypted traffic, mitigating the risk of concealed threats.
Dedicated to enhancing SSL/TLS infrastructure, SSL Orchestrator also maximizes the effectiveness of existing security investments. It dynamically chains security services and steers decrypted traffic via policy, applying context-based intelligence to encrypted traffic.
SSL Orchestrator centrally manages and distributes the latest encryption technologies across the entire security infrastructure. It centralizes certificates and key management while providing robust cipher management and control.
It also delivers a single platform for the unified inspection of next-generation encryption protocols. SSL Orchestrator ensures security solutions are operating at peak efficiency and can scale with high availability via F5’s load balancing and scaling capabilities. And it independently monitors the health of each security service.
As a central point for all things encryption, SSL Orchestrator must ensure that its environment, whether physical or virtual, supports the most stringent and robust government and industry standards for security and privacy.
A key part of providing SSL visibility requires a robust key management (PKI) infrastructure. Key management and key protection, as well as their proper use, are often associated with regulatory mandates—for example, the Federal Information Processing Standard 140.2 (FIPS 140-2), Common Criteria, standards from the International Organization for Standardization (ISO), and other regional or vertical-specific certifications.
FIPS 140-2, despite being a U.S. National Institute of Standards and Technology (NIST) standard, can be found in, and is applied to, many highly-regulated markets worldwide and provides guidance for the use of crypto and implementation validation.
There are several different Levels of FIPS 140-2 that map to regulations, risk, and sensitivity of data. In SSL visibility deployments, FIPS 140-2 Level 3 is often required to protect the signing key in a hardware, tamper-resistant physical enclosure, referred to as a Hardware Security Module (HSM). An HSM will include key zeroization, startup integrity checks, and controls for preventing unauthorized key extraction. HSMs deliver more than enhanced key security; they can also help simplify certificate management and reduce compliance costs.
F5 provides the broadest range of FIPS-compliant platforms, including several HSM options, both on box and via Public Key Cryptography Standards #11 (PKCS #11) to network HSMs. Depending on the SSL Orchestrator license and model selected, there are a number of FIPS 140-2 levels available, including a range of price options to make sure policy adherence is possible for any organization, regardless of size.
F5 SSL Orchestrator delivers unparalleled, holistic visibility into encrypted traffic, mitigating risks associated with malware and other malicious threats masked by inbound encrypted traffic. SSL Orchestrator also stops stolen data exfiltration, CnC communications, and the downloading of additional malware and malevolent payloads in outbound encrypted traffic.
And, SSL Orchestrator, through its centralized decrypt and re-encrypt function and dynamic service chains and intelligent traffic steering, enables high-value security features to perform at scale—securely offloading CPU-intensive decryption/encryption. That makes it easier to maximize security investments.
These actions not only stop security blind spots and hidden threats, but also free existing security solutions to optimally perform their primary functions: delivering threat protection, preventing data leakage, sandboxing, and other relevant security services.
SSL Orchestrator has several licensing options designed for small- and medium-sized business (SMB), modern enterprises, and the cloud. With several platform options, including Virtual Editions (VEs), as well as mid-tier to high-end appliances, F5 has solutions to meet the changes in encrypted traffic and the changes to ciphers and protocols, including TLS 1.3, tomorrow’s IoT devices and eventually post-quantum cipher schemes.
PUBLISHED JULY 01, 2019