
When I was a wee lass getting ready to deliver my company’s very first Internet-enabled application, I learned a valuable lesson. It wasn’t about technology. It wasn’t about the Internet. It was about processes and how frustrating they can be to the people forced to navigate them.
All we needed was a simple firewall rule to allow traffic to reach the application. That’s it. One rule.
The change itself probably took the network engineer all of five minutes to log in, type the command, and save the config. The process, however, took weeks.
That’s because the process was (1) not documented and (2) required no less than three different signatures on a printed approval form. Signatures that waited for the end of someone’s vacation and re-discovery after being buried on someone’s desk.
Eventually, we got the approvals and the changes were made and voila! I got a nice plaque and a pat on the back.
Fast forward a lot of years and you’ll find that processes are still a significant source of angst for employees. A recent survey by Nintex sought to understand that frustration, and discovered that processes are, in fact, the root of discontent and even employee turnover at many organizations.
In fact, amongst those employees who are right now looking for a new home, 72% said IT processes were broken compared to the 58% of overall employees who agreed. Other processes pointed to as problematic were printing (yes, printing) as well as administrative processes like raise and promotion processes.
Overall, Nintex identified “Technology troubleshooting” and “access to tools and documents that enable good job performance” as the top two most broken processes in corporate America. The report further notes that “the absence of prompt IT service directly leads employees to engage in shadow IT – a practice that inherently places company data at risk. In fact, 40 percent of respondents say they’ve used unsanctioned devices or apps as a direct result of unresolved IT issues.”
You might recall our own research that noted a similar response by DevOps to frustrations over production pipeline processes. In that research we learned that more than one in four (27%) of DevOps respondents indicated lack of self-service access via automation to production pipelines influence their decision to reach for cloud-based solutions “a lot” and 38% influenced “some.”
Processes are very important to both business and operational success.
They are even more important in the context of digital transformation, which in part seeks to codify (automate) those processes to realize gains in productivity and efficiency.
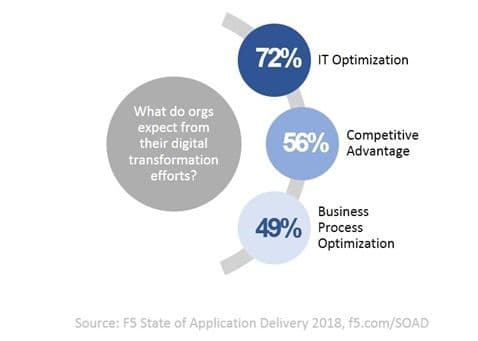
The report from Nintex is helpful when exploring our own results from the State of Application Delivery 2018 exploring the benefits organizations expect (want) out of their digital transformation efforts.
At the top of that list was IT optimization. Coming in at number three was business process optimization.
Sensing a theme?
Organizations are investing in digital transformation efforts in the hopes that it will make them more efficient. That’s what optimization means, after all: “making the best of most effective use of a situation or resource.”
That’s the dictionary definition, by the way. I didn’t make that up.
The thing about optimization is that you have to first understand the process. You have to lay it out – whether that’s the process of requesting a new virtual machine or container environment, printing a document, or submitting a request for some time off.
Only after you know what the process is now can you begin to optimize it. And you really want to try to do that before you codify it in a business process management (BPM) system or in scripts and templates that will execute the process for you.
Because “garbage in, garbage out” isn’t just a developer’s commentary on data or code. It’s true for all processes. If you automate a poor process, you’re going to get poor results – just faster than you might have if you executed it manually.
Optimization – whether of IT or business processes – requires first understanding what you’re trying to optimize. You need to map out the value stream – the individual tasks that comprise a business process – and get rid of the extraneous fluff that serves no real business or operational purpose other than ‘that’s the way we’ve always done it.’
And those unnecessary steps exist in IT processes, too. An approval that isn’t necessary. Waiting on a task that isn’t a blocking dependency. Automation as part of your internal digital transformation efforts isn’t going to radically change the necessary technical steps to fulfilling a request. But it can radically alter the operational processes by exposing a whole lot of inefficiencies and unnecessary waiting around that can be eliminated.
Optimization may be about making IT and the business go faster; but it starts with enabling IT and the business to go smarter.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
