The Hunt for IoT by our own F5 Labs threat researchers continues. Its latest report exposes not only an active search for vulnerable IoT devices, but the targeting of build infrastructure.
As part of their tracking of attacks on IoT devices – primarily via telnet and SSH access – F5 Labs threat researchers perhaps inadvertently uncovered attempts to take over build infrastructure systems including Jenkins and Vagrant. Additionally, database systems – Oracle, MySQL, PostGres, and Hadoop – appear to be common targets, as well as monitoring provider, Nagios.
The credentials used during brute force attacks are seen in the “Top 50 Attacked Admin Creds” in which all the aforementioned systems appear prominently.
It should be noted that these attacks are focused on SSH and telnet – remote access – via the operating system users routinely created on install by these systems. The majority are deployed on a Linux-based system and automatically create a neutered system-level user for execution, as per best practices. By default, these users have no password. But as the Vagrant documentation on creating a base box notes, these users are often given passwords and login privileges.
“This user should be setup with the insecure keypair that Vagrant uses as a default to attempt to SSH. Also, even though Vagrant uses key-based authentication by default, it is a general convention to set the password for the "vagrant" user to "vagrant". ”
It is noteworthy that in the latest F5 Labs report, it is exactly this combination that is used by attackers attempting to access the system, namely “vagrant:vagrant”. Interesting, as well, is the inclusion in the top fifty attacked credentials of “deploy/deploy”. Along with the identifiable build infrastructure credentials for Jenkins and Vagrant, this indicates a growing awareness of the accessibility of such systems and the target-rich environment they offer. Access to a build or deploy system would offer a wealth of opportunity for attackers given the distributed nature of these systems and their purpose. Comprising a Jenkins user could ostensibly enable access to source code, which in turn offers untold opportunities to inject a variety of malicious code inside an application or system.
Build infrastructure is increasingly vital to business. To wit, 90% of Jenkins users consider it mission-critical. But it’s not just Jenkins, it’s automation frameworks and build infrastructure in general.
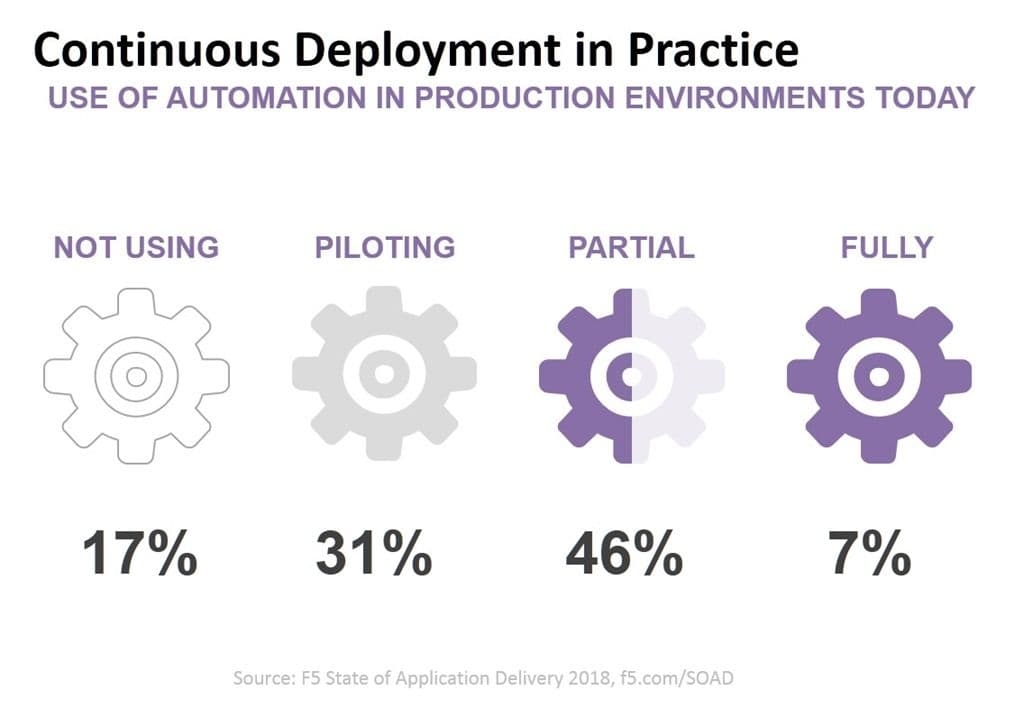
A significant percentage of organizations are using automation, in general, to push changes into production based on our latest State of Application Delivery survey. That invariably means that systems like Vagrant are active in production environments, but not necessarily isolated.
Caution is warranted and careful consideration of the credentials used by build infrastructure and associated systems should be required. Given the purpose of these systems, it is doubly important to take care with credentials and limit (if not completely deny) remote access with external security services if necessary.
As automation consumes more of the production environment, it behooves the business leaders and security professionals to be mindful of the threat posed by a compromise of such systems. As our threat researchers have uncovered, attackers are already aware of the rich target that build and automation systems offer and are actively seeking access.
Stay safe out there.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
