It’s an application world. That’s beginning to sound trite and cliché, but it’s still true. When it comes to security, that means our focus should start with the application and work our way out towards the user.
But that’s not how we build security architectures today.
Today we build security architectures by trying to emplace an impenetrable (fire)wall around the perimeter. As we move inwards toward the application the security trenches we build are less and less granular until, at last, we get to the app and there’s pretty much nothing left. Our most application-affine security is furthest from the app it needs to protect rather than the other way around. It leaves us trying to scale massively at the edge of the network (where the expensive hardware-based devices are required to support the bandwidth and port density needed) rather than scaling more modestly closer to the app, where less-expensive, easier to manage software and virtualized “devices” could be more easily emplaced.
We need to flip this architecture around and refactor security to better fit today’s application and business models.
We need to stop trying to be “application aware” at the corporate perimeter in order to better scale and derive value out of security infrastructure. We need to stop being so application agnostic close to the app and begin shifting that all left, toward dev and ops and a software model that scales both economically and architecturally. We need a generic, corporate security infrastructure at the traditional edge of the network and a specific, per-application security architecture at the new perimeter: the application.
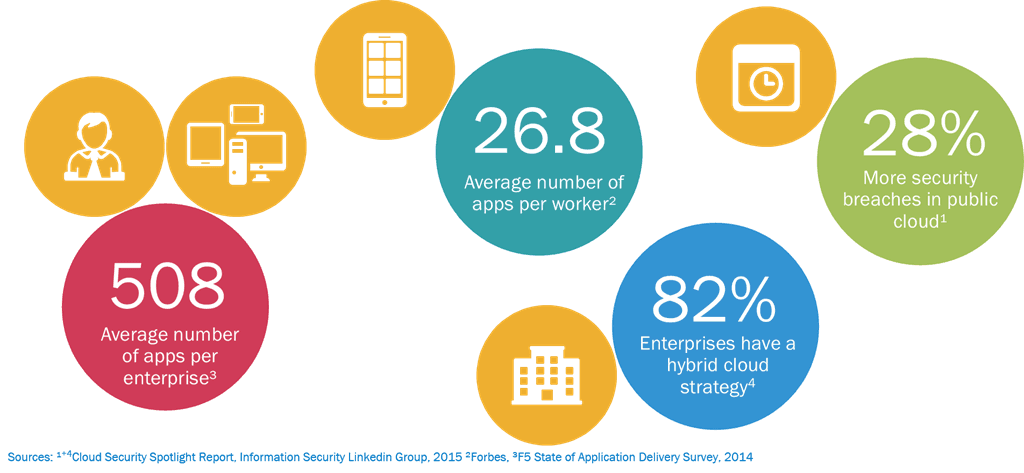
That’s especially true when you consider the impact cloud is having on applications. Not on the data center, but on applications. Applications are what we need to protect out there, not the network, and we can’t do that if our security strategy relies on having complete control over the network (and who accesses it). We need to consider how to protect the application whether it’s in the data center or not, and build a security strategy based on that foundation, rather the one we relied upon before cloud disrupted the data center.
Consider the coming tsunami of applications generated by the Internet of things and adoption of microservices architectures. If every “new” technology generally results in a 10x increase in applications, then how many applications will two, simultaneous “new” technologies generate? How many new security policies will be required at the edge of the network to support each and every one of those applications?
Yeah. A lot. An order or two of magnitude more than what there is today.
What if we shifted those left (in terms of the deployment pipeline; right if you’re looking at a traditional network diagram) and moved them to a more software-deployed and defined environment? What if we enlisted the folks who develop and intimately know the applications to help develop the policies that will secure them and then integrated them into the deployment process? Into the CI/CD pipeline? What if we packaged up apps the same way, with the same security services they need whether in the public cloud or on-premises? Somehow managed to achieve consistent security across IT infrastructures that 60% of organizations consider the most important factor for protecting cloud environments [Cloud Security Spotlight]?
Would that scale?
I’m guessing it would, with less disruption and greater manageability than the current model.
Cloud is disruptive. Mobility is disruptive. The Internet of Things will be disruptive. That’s not always bad, especially when it affords us an opportunity to rethink and reevaluate the way in which we’re deploying and delivering and securing applications.
So maybe it’s time to turn our security model inside out, and embrace the app as the new perimeter as a better way to scale security, protect apps, and defend the sanctity of our data.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
