Era Belongs to Technology
Technology is transforming the way we do business. It has brought ease and timelines. We do not have to stand in queues for paying utility bills or getting a taxi anymore. Our smartphone tells us when our bus is going to arrive and keeps us connected to work while being on the move. With rapid digitization more and more of our work and life will be controlled by our smart devices.
Criminals are keeping pace with technology and have figured innovative ways to capitalize with the technology adoption. The rewards that cybercrime has to offer, the fact that it can be achieved hiding behind proxies and easy renting of technologies from underground markets has paved way for increased cybercrime.

Enterprise and Individuals alike are looking and investing in technologies to prevent, detect and respond to these threats. Heavy investments are made in the area of network and application security to guard the fort (read Brand Value). New threats are mitigated with point products leading to an enterprise acquiring a lot of technologies.
Intelligent Orchestration of Security
Today a typical enterprise stacks different kind of technologies as layers of defense and user traffic passes through it. Individually many security devices can cater for the traffic load, SSL/TLS offload, and the processing of all traffic, but the CPU cycles spent can be optimized and put to better use with intelligent orchestration.
Taking a deeper delve, let’s take a look at the traffic a typical enterprise generates (not an exhaustive list).
- Intranet Web Sites
- Social Media like Facebook, Twitter, etc.
- YouTube and other video sharing platforms
- Search Engines
- Emails
- Command and Control Sites
- Backup traffic
- Sites containing Personally Identifiable Information and Financial Information
Some types of traffic need more scrutiny than others. Making all of them pass through the same kind of inspection is not an intelligent choice. Something similar to service-oriented architecture is needed for modern day networks to thwart modern threats in an optimized manner.
Introducing the Intelligent Inspection Zone
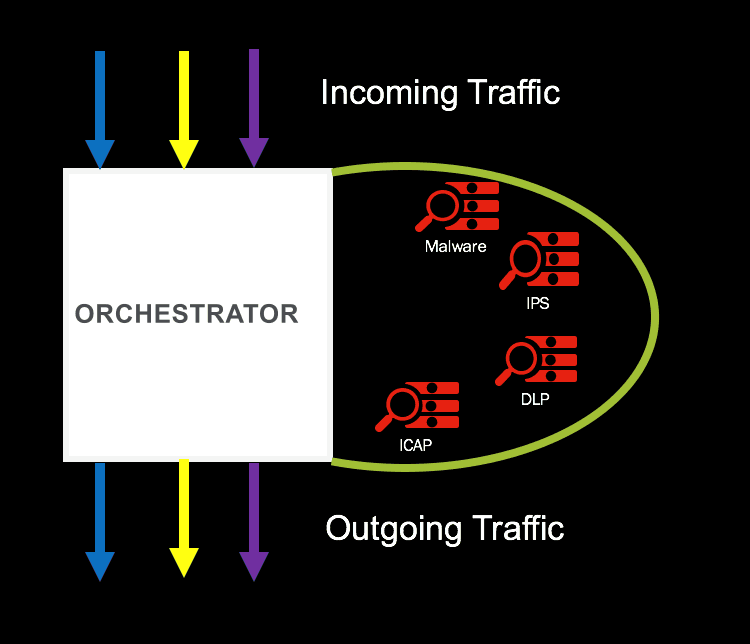
An intelligent inspection zone can be characterized with security purchases of an organization being made available as services. These services are then applied to traffic path based on threat level. As displayed in Image below, the inspection zone needs to be controlled by an Orchestrator. The Orchestrator is responsible for:
- Making Security Appliances available as Service to various network paths
- Create a SSL free inspection zone for optimized use of inspection service
- Fail open or close the network in case a device fails
- Policy driven selection of security appliance for network traffic based on threat
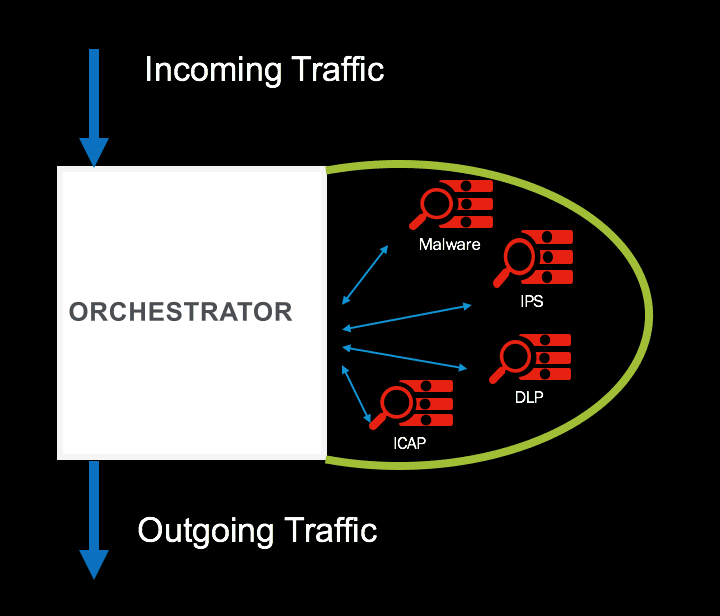
Traffic heading towards an untrusted site on internet (possibly a Command & Control) should undergo strict inspection.
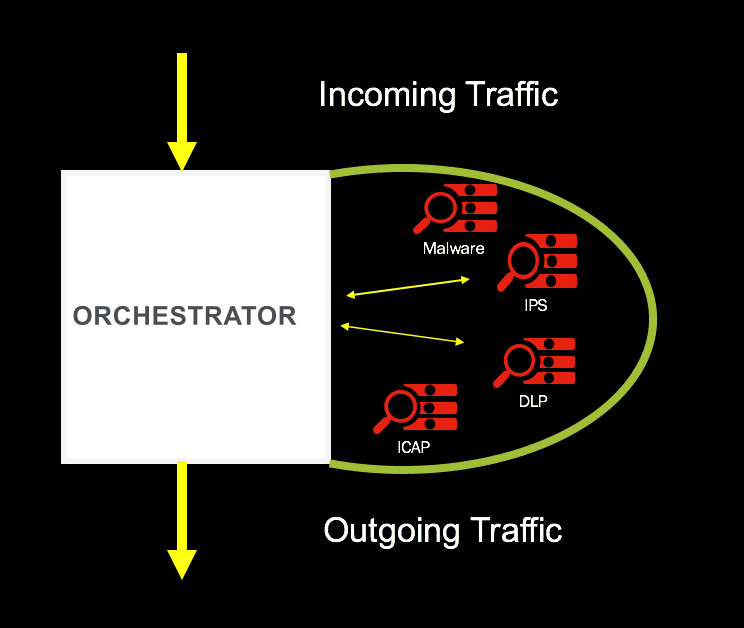
Traffic heading towards a trusted site on internet (or internal backup site) should undergo intermediate level of inspection.
An intelligent inspection zone also provide an avenue to introduce new security appliance easily, by simply adding it to the inspection zone and adding it to traffic steering policy.
Conclusion
An intelligent inspection zone will help organization orchestrate the security and optimize security investments. Making security appliances available as service and an SSL free inspection zone will help organizations utilize the security appliance.
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.