Payment Card Industry Data Security Standard (PCI DSS) version 4.0.1 serves as a forcing function for retailers and e-commerce providers to shore up their application security defenses. The potential fallout is real, as best practices have become enacted requirements. Due to the sophistication of attackers and demand from customers to easily transact, organizations that rely on online commerce for their core business should consider integrated solutions that not only help meet stringent compliance mandates, but more importantly, seamlessly protect the digital business.
Let’s dive into some of the reasons why in this blog.

E-commerce platforms must provide a seamless and secure customer experience.
Why now?
While not new, the latest PCI standard dramatically expands the scope of its guidance. A common misconception over the years can be summarized as, “I am good, I have a firewall, check.” This misconception can now be considered a myth.
Application modernization, the rise of omnichannel digital touchpoints, and constant advancements in attacker sophistication necessitate the addition of numerous security controls to meet PCI DSS compliance, including payment script security, protection of APIs, rapid detection and response to compromised credentials, and regular vulnerability scans.
As stated in the 2025 Gartner Market Guide for Cloud Web Application and API Protection, client-side protection is becoming increasingly important as the latest PCI standard mandates security controls for all payment scripts.
Web applications are increasingly complex due to the de-centralization of architecture and distribution of software components across hybrid and multicloud environments. This de-coupling of application infrastructure and sprawl of software supply chains opens the door (and windows) to threats that target business logic and client browsers as part of the industrialized attack lifecycle.
What can go wrong? (Hint…the weakest link)
Client-side attacks like infostealers can be used to harvest user credentials that are then used in large-scale automated attacks, which left unmitigated, can lead to account takeover and fraud.
Formjacking injects malicious JavaScript into online forms to capture user inputs at the browser level. It’s often carried out by exploiting vulnerabilities in third-party scripts, and is difficult to detect with traditional, centralized security controls.
Magecart is an umbrella term for a set of cybercriminal groups that specialize in web skimming, targeting e-commerce sites by injecting JavaScript code that steals payment data during checkout.
Web application firewalls (WAFs) continue to be a strategic security control, especially since the new standard specifies that all vulnerabilities provide a potential opportunity for attackers and must be addressed regularly. Many WAFs can protect APIs, but the speed of modern application development requires additional capabilities to dynamically detect and automatically protect endpoints buried deep in business logic or called within third-party ecosystems, ideally in code and in testing.
While software lifecycle processes and secure coding techniques are the north star, risk assessments need to be continuous and mitigations will often require robust runtime security in production, including in the client browser, frontend web application, and backend APIs, to effectively thwart attacks across multiple threat vectors for highly interconnected digital experiences.
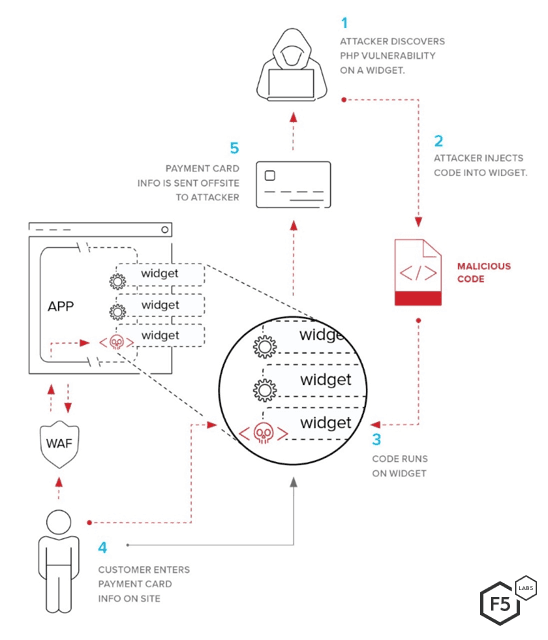
Third-party services are a common component and risk surface for web applications.
What else can go wrong? (Hint…platform abuse)
Vulnerabilities are defects or weaknesses in software that can be exploited by attackers. Now that applications are essentially API-based systems, backend business logic functions are at high risk of abuse.
F5 Labs research details how the e-commerce sector had one of the highest proportions of advanced attacks, with 44.82% of mobile credential stuffing being advanced. These attackers leverage a variety of tools to simulate browser, mobile, and user behavior in attempts to evade detection, including generating valid tokens, spoofing telemetry signals, and emulating keyboard and mouse events. Attackers constantly retool to bypass defenses, pivoting from web apps to mobile apps or escalating their tactics, techniques, and procedures.
Attacks on the e-commerce sector also employ reseller bots that abuse the add-to-cart function, which can prevent real customers from transacting. More than one in five add-to-cart transactions observed from over 200 billion web and API requests analyzed were automated.
Additionally, bots manipulate user reviews to create realistic fake reviews, in many cases with generative AI.
Even within e-commerce, F5 Labs threat research has uncovered that the fashion industry is the worst hit industry by scrapers, which extract large amounts of data and content from their targets, making up 53.23% of all web traffic. Scraping can put the business at a pricing disadvantage and put intellectual property at risk.

Bots and malicious automation fuel the industrialized attack lifecycle.
What’s regs got to do with it?
The latest PCI DSS includes several recommendations for employing targeted risk analysis versus traditional enterprise-wide risk assessments.
In particular, the updated standard addresses the growing threat of client-side attacks with two client-side requirements effective March 31, 2025, but does not prescriptively dictate how organizations meet them.
These new mandates recognize that malicious client-side scripts are a growing threat surface in the payment card industry. Established methods for addressing these risks, including Content Security Policies (CSPs) to block unauthorized code injections into a website and Subresource Integrity (SRI) web methods to verify those third-party apps have not been altered, are difficult to implement and maintain, especially now in the AI era where competition for customer mindshare is driving continual enhancements to digital experiences.
How to be seamless and secure
Customers expect to transact easily and do not tolerate delays, glitches, and especially security incidents. Widely used security controls, such as web application firewall solutions, may not adequately extend protections to the client browser or backend APIs. Bot management solutions that inject user challenges via CAPTCHA are largely ineffective at deterring abuse from skilled cybercriminals, but are very effective at frustrating users. Even multi-factor authentication can be bypassed.
Attackers employ different techniques depending on the platform, industry, and business logic they can abuse, and for e-commerce, the inability of a prospective buyer to add an item to their shopping cart is a significant threat. The transaction, resulting revenue, and customer loyalty are all at stake.
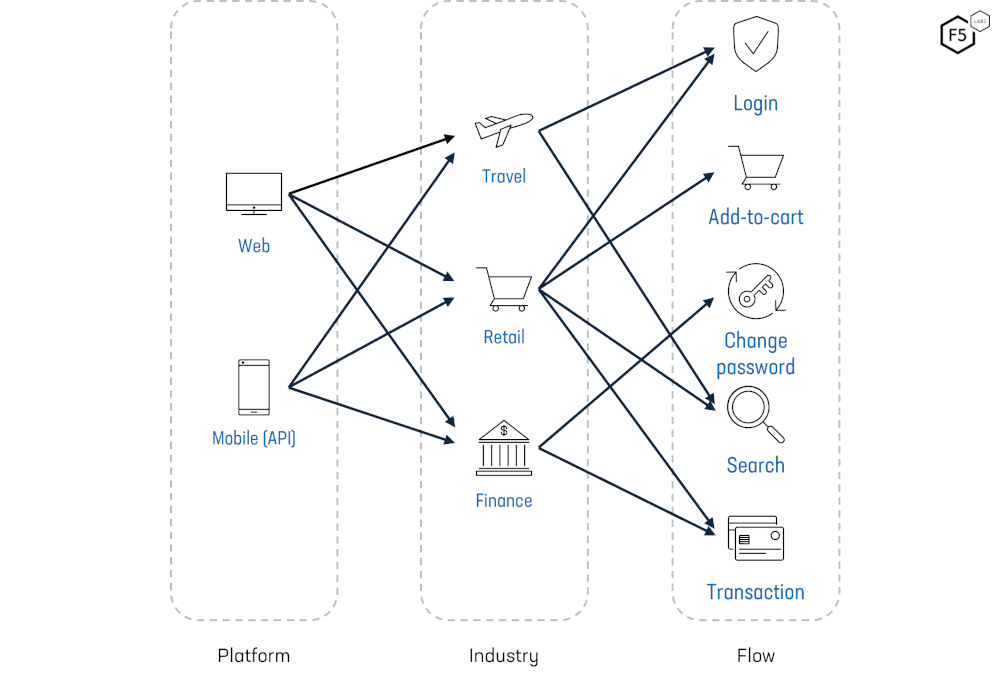
The interaction between platforms, industry, and flows targeted by bots and automated attacks.
Instead of deploying a patchwork of loosely integrated security controls to meet PCI DSS compliance mandates, e-commerce providers should consider unified security platforms designed to protect web apps, APIs, and customers throughout the digital lifecycle from the actual threats targeting their industry.
To learn more about PCI DSS, check out these blogs:
- Make Your AWS Environment PCI DSS v4.0.1 Compliant with F5
- F5 Distributed Cloud Client-Side Defense Prepares Customers for PCI DSS v4.0.1
- F5 Helps You Address the New PCI DSS v4.0 Requirement
- PCI DSS 4.0.1 Update: Major New API Security Upgrades Required
- Important Changes in PCI DSS 4.0.1 You Should Know About
For more, go to F5 solutions for eCommerce.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
