Artificial intelligence has become a double-edged sword for cybersecurity. While AI models drive innovation and transform industries, their inherent unpredictability introduces new risks. Whether it’s an embarrassing chatbot conversation or an agent with too much agency, the new risk landscape is littered with reputational land mines that could earn you unwanted media attention or erode customer trust.
Each new model iteration brings with it fresh vulnerabilities, and once organizations start to give agency to these models at scale—whether its tool calling or performing operations—the impacts of exploitation, bias, and safety have a much greater impact. Hence, the need for more controls and guardrails.
“By integrating CalypsoAI’s capabilities with the F5 Application Delivery and Security Platform (ADSP), F5 positions itself as a leader in providing a comprehensive solution that not only mitigates AI risks but also enables enterprises to scale their AI deployments with flexibility, security, and trust.”
In its recent “Market Guide for AI Trust, Risk and Security Management (TRiSM),”1 Gartner® states that, “Enterprises face multiple AI risks and are most concerned with data compromise, third-party risks, and inaccurate or unwanted outputs.” In our opinion, this bolsters the need for heightened governance, security, and risk management, which has become a critical imperative for organizations adopting AI at scale—especially for those who want to do it quickly. Having controls in place from TRiSM allows for both safer and faster adoption of AI.
In this shifting landscape, F5’s acquisition of CalypsoAI will emerge as a timely and strategic move to address these challenges. Relevant capabilities include CalypsoAI’s expertise in AI governance and runtime inspection and enforcement for AI systems. By integrating CalypsoAI’s capabilities with the F5 Application Delivery and Security Platform (ADSP), F5 positions itself as a leader in providing a comprehensive solution that not only mitigates AI risks but also enables enterprises to scale their AI deployments with flexibility, security, and trust.
Navigating a rapidly maturing AI landscape
The AI market is evolving at an unprecedented pace, with foundational large language models (LLMs) and specialized small language models (SLMs) proliferating across industries. Organizations that try to fall back on traditional tools in this shifting environment risk coming up short in their ability to scale, maintain a level of flexibility, and contain costs.
As Gartner states, “Enterprises must retain independence from any single AI model or hosting provider to ensure scalability, flexibility, cost control and trust, as AI markets rapidly mature and change.”1
We agree with the importance of retaining independence from any single AI model or hosting provider, citing the need for flexibility and trust as AI capabilities continue to expand across new use cases.
F5 is responding directly to this dynamic landscape by incorporating CalypsoAI’s real-time security inspection and risk scoring for any model, regardless of where it comes from. Enterprises leveraging F5 ADSP, augmented by CalypsoAI’s solutions, can confidently adopt diverse AI tools while maintaining governance over their models and applications. This independence alleviates reliance on specific AI providers and future-proofs AI implementations for scalable success.
A layered approach to AI security
According to the Gartner Market Guide for AI TRiSM,1 there are four layers of technical capabilities, all of which rest on a fifth layer that represents traditional technology protection:
- AI governance
- Runtime inspection and enforcement
- Information governance
- Infrastructure and stack
In our view, this framework ensures AI systems are trustworthy and secure by validating their alignment with organizational policies, regulatory compliance, and ethical expectations.
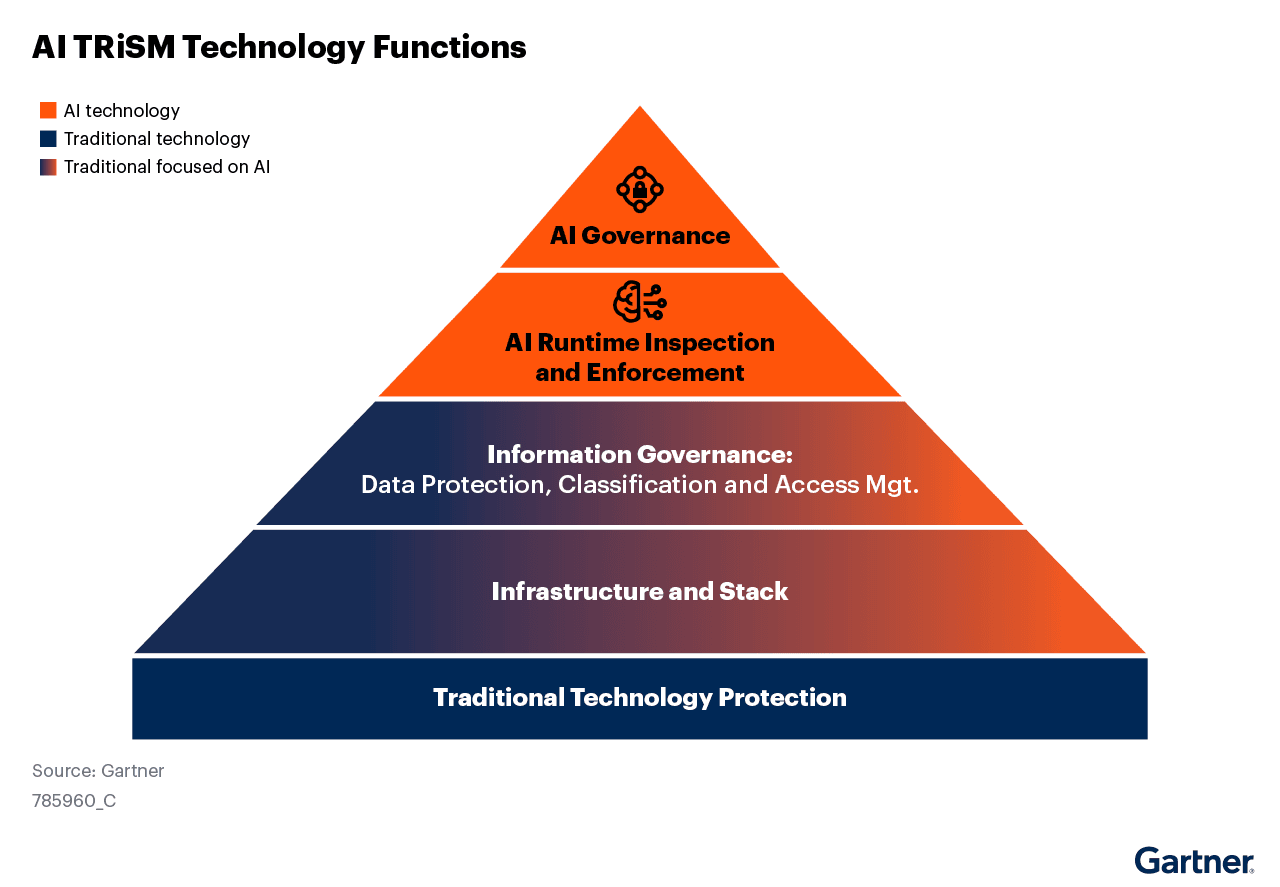
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from F5.
The acquisition of CalypsoAI will bolster F5’s role as a leader in application security, particularly on AI where enterprises face mounting threats from both the outside in and the inside out, in the form of bad actors exploiting misguided AI behaviors and the unpredictable behavior of AI itself. CalypsoAI’s capabilities in AI governance and runtime enforcement complement F5 ADSP, which excels in delivering enterprise-wide controls for information, infrastructure, and traditional protection technologies. Combined, these strengths seek to address every layer of AI TRiSM,1 providing end-to-end coverage for AI trust and risk management.
CalypsoAI’s strengths lie in the top two layers of the pyramid—AI governance and runtime inspection and enforcement—while F5 ADSP complements these capabilities by supporting information governance, infrastructure, and traditional protection layers.
AI governance
CalypsoAI enhances AI governance with model cataloging and risk scoring systems to provide a unified view of enterprise AI assets. CalypsoAI’s governance capabilities focus on responsible AI principles—accountability, transparency, and security. By continuously assessing model health and performance, CalypsoAI ensures alignment between AI outputs and regulatory policies, such as the General Data Protection Regulation (GDPR) and the EU AI Act, reinforcing ethical and trust-driven AI practices.
AI runtime inspection and enforcement
CalypsoAI leverages runtime engines to enforce policy alignment across AI applications. These mechanisms provide real-time inspection of AI interactions, highlighting anomalies or violations. CalypsoAI’s plug-and-play frameworks adapt defenses based on model behavior and agentic threat intelligence, delivering both proactive and real-time security for enterprise AI deployments. Borrowing from these insights, runtime inspection addresses malicious prompts, bias risks, and compliance concerns, positioning enterprises to stay ahead of emerging threats.
Information governance
F5 ADSP builds robust information governance on the foundation of acquisitions like LeakSignal to help strengthen data protection in products like F5 BIG-IP SSL Orchestrator (SSLO), which plays a pivotal role in precisely identifying the types of data being transmitted and their destinations. SSLO enables organizations that are deploying AI models to enforce policy-driven controls that intercept data before exposure, dramatically mitigating risk.
CalypsoAI adds both advanced role-based access control (RBAC) and data loss protection (DLP) functionality that aligns with F5’s broader ecosystem, delivering dynamic data classification and discovery at AI runtime. Using F5 BIG-IP Access Policy Manager (APM), enterprises gain unified access controls for users, devices, and APIs—fostering a secure backbone for AI-driven interactions while addressing AI-centric governance requirements.
Infrastructure and stack
F5 ADSP web application and API protection (WAAP) solutions play a critical role in securing the infrastructure at the heart of AI applications, and that begins with creating a robust and secure API ecosystem. While AI is a powerful and advanced vehicle, the highways it uses are still the same APIs organizations have historically struggled to discover and secure. CalypsoAI’s runtime enforcement complements WAAP by mitigating vulnerabilities in AI-specific interactions, while F5 strengthens this layer through API discovery and protection tools designed for API-heavy ecosystems.
Partnerships with leading storage vendors like Dell, NetApp and MinIO extend this security to data workflows, ensuring scalable, high-performance data storage and transit to power AI model training and inference cycles, including RAG. Additionally, F5’s partnership with NVIDIA brings advancements to the DPU through F5 BIG-IP Next for Kubernetes, helping to streamline application delivery and deployment for GPUs while introducing new security controls for inference and training.
Incorporated into a single platform with F5 ADSP, these technological advancements help reduce the overall cost of ownership while future-proofing AI infrastructure for enterprise scalability.
Traditional technology protection
The traditional technology layer forms the backbone of enterprise application security, and F5 BIG-IP and F5 WAAP solutions provide foundational protections that ensure the stability and resilience of applications, data, and infrastructure.
Anchored by advanced security tools, these solutions address a range of threats—from volumetric and targeted distributed denial-of service (DDoS) attacks to bot traffic and advanced application-layer threats. At the core lies the capability of a robust web application firewall (WAF) to defend against SQL injection, cross-site scripting (XSS), and other OWASP top threats. This comprehensive coverage completes a layered security approach—ensuring end-to-end protection for AI operations, as well as traditional workloads.
Strengthened leadership in AI security
Artificial intelligence presents both transformative potential and significant risks for cybersecurity. Its inherent unpredictability, coupled with relentless exploitation by bad actors, creates an evolving threat landscape that challenges traditional approaches to security.
As enterprises rapidly adopt AI innovations, the need for trust and accountability becomes paramount. F5’s strategic acquisition of CalypsoAI will offer an essential response to this growing demand, empowering organizations to confidently embrace AI while maintaining security, privacy, and operational control. With layered AI TRiSM1 solutions, F5 sets a new standard for AI application security, ensuring businesses can innovate with trust at their core.
1 Gartner, Market Guide for AI Trust, Risk, and Security Management, 18 February 2025.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved
About the Author

Related Blog Posts
The hidden cost of unmanaged AI infrastructure
AI platforms don’t lose value because of models. They lose value because of instability. See how intelligent traffic management improves token throughput while protecting expensive GPU infrastructure.
AI security through the analyst lens: insights from Gartner®, Forrester, and KuppingerCole
Enterprises are discovering that securing AI requires purpose-built solutions.

F5 secures today’s modern and AI applications
The F5 Application Delivery and Security Platform (ADSP) combines security with flexibility to deliver and protect any app and API and now any AI model or agent anywhere. F5 ADSP provides robust WAAP protection to defend against application-level threats, while F5 AI Guardrails secures AI interactions by enforcing controls against model and agent specific risks.
Govern your AI present and anticipate your AI future
Learn from our field CISO, Chuck Herrin, how to prepare for the new challenge of securing AI models and agents.

F5 recognized as one of the Emerging Visionaries in the Emerging Market Quadrant of the 2025 Gartner® Innovation Guide for Generative AI Engineering
We’re excited to share that F5 has been recognized in 2025 Gartner Emerging Market Quadrant(eMQ) for Generative AI Engineering.
Self-Hosting vs. Models-as-a-Service: The Runtime Security Tradeoff
As GenAI systems continue to move from experimental pilots to enterprise-wide deployments, one architectural choice carries significant weight: how will your organization deploy runtime-based capabilities?
