Traditional access control mechanisms can no longer protect sensitive data and resources in the ever-evolving DoD cybersecurity landscape. As organizations mature and reach to achieve milestones on roadmaps such as the DoD zero trust roadmap, they require a more granular, dynamic, and flexible approach to ensure that the right individuals can access the right resources at the right time. This is where Attribute-Based Access Control (ABAC) comes into play. In this blog post, we will delve into the concept of ABAC and explore its implementation with a specific focus on leveraging F5 solutions to bolster security measures.
Understanding Attribute-Based Access Control (ABAC)
Attribute-Based Access Control (ABAC) is a modern access control model that evaluates various attributes or characteristics associated with a user, resource, and environment to make access decisions. Unlike traditional access control models that rely on roles or groups, ABAC takes into account a wide range of characteristics such as user attributes (clearance level, department, job title), resource attributes (sensitivity, classification), and environmental attributes (time of day, location).
Superior Benefits of ABAC:
- Granularity: ABAC allows for fine-grained access control, enabling organizations to define access policies based on specific attributes. This ensures that users only have access to the necessary resources for their roles.
- Dynamic Access: ABAC adapts to changes in attributes and context. This dynamic nature ensures that access decisions consider real-time changes, reducing the risk of unauthorized access. An example could be taking in telemetry from a UEBA or risk engine to determine the overall risk associated with a user and adjust permissions on the fly.
- Policy Flexibility: Organizations can create complex access policies that reflect business rules accurately. This flexibility is beneficial in environments where users have diverse roles and resource requirements.
- Risk Management: By considering attributes such as the sensitivity of data and the security posture of the user's device, ABAC helps manage security risks effectively.
Implementing ABAC with F5
F5 is a leader in application delivery and security and offers solutions that integrate with ABAC principles to enhance access control and security. Here's how F5 can be utilized to implement ABAC or complement current solutions:
- BIG-IP Access Policy Manager (APM): F5's APM module enables the creation of access policies based on a wide range of attributes. It can intercept user requests, evaluate attributes, and grant or deny access accordingly. This ensures that users can access resources only if they meet the specified attribute criteria. Access Policy Manager is often used as the PEP or PDP in zero trust architectures. In addition, C2C or Comply to Connect is another use case in the DoD where APM can help organizations achieve granular ABAC control.
- Contextual Security: F5 solutions can gather context from various sources, such as user directories, device information, trust score engines, and third-party services such as UEBA. This contextual information enriches the attribute evaluation process, leading to more accurate access decisions.
- Single Sign-On (SSO): F5's SSO capabilities, combined with ABAC, provide a seamless and secure user experience. Users authenticate once, and their attributes and the defined policies govern their subsequent per-request access to different resources.
- Integration with Identity Providers and Service Providers: F5 solutions can integrate with various identity and service providers, including Active Directory, LDAP, and cloud providers such as Okta, Ping, and SailPoint, to retrieve user attributes. These attributes play a crucial role in making informed access decisions.
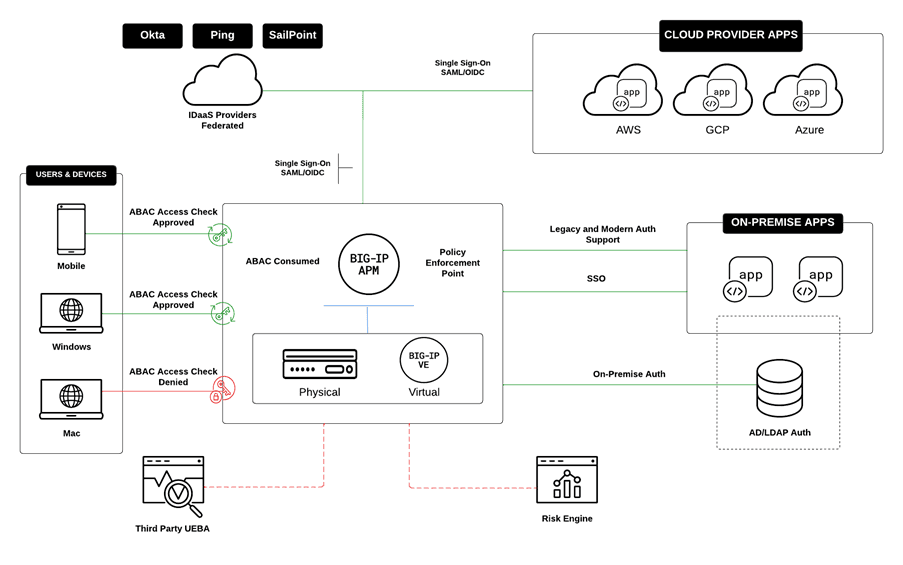
As DoD organizations continue to navigate the challenges of securing their digital assets, solutions like Attribute-Based Access Control (ABAC) offer a robust way to enhance access control measures. F5, with its advanced application delivery and security solutions, provides a powerful platform for implementing ABAC principles. By considering a multitude of attributes and contexts, organizations can ensure that their sensitive resources remain protected while enabling authorized users to work efficiently.
In a world where data breaches and unauthorized access incidents are growing concerns, embracing modern access control mechanisms becomes imperative. By combining the capabilities of ABAC with F5 solutions, Department of Defense organizations can elevate their security posture and establish a strong defense against evolving cyber threats.
Visit https://www.f5.com/solutions/public-sector/public-sector-cybersecurity for more detail on government-focused security solutions.
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.