Introduction
Internet is revolutionizing the whole world. The Internet penetration at APAC is at average of 36% with countries like New Zealand at 91%, Singapore at 81 % and so on. Banking sector is not immune to the trend and is going digital. As per McKinsey Survey Digital Banking Consumers represent more than 700 million customers across Asia.
The chart below shows the penetration of Digital Banking in Asia as registered by McKinseys&Company.
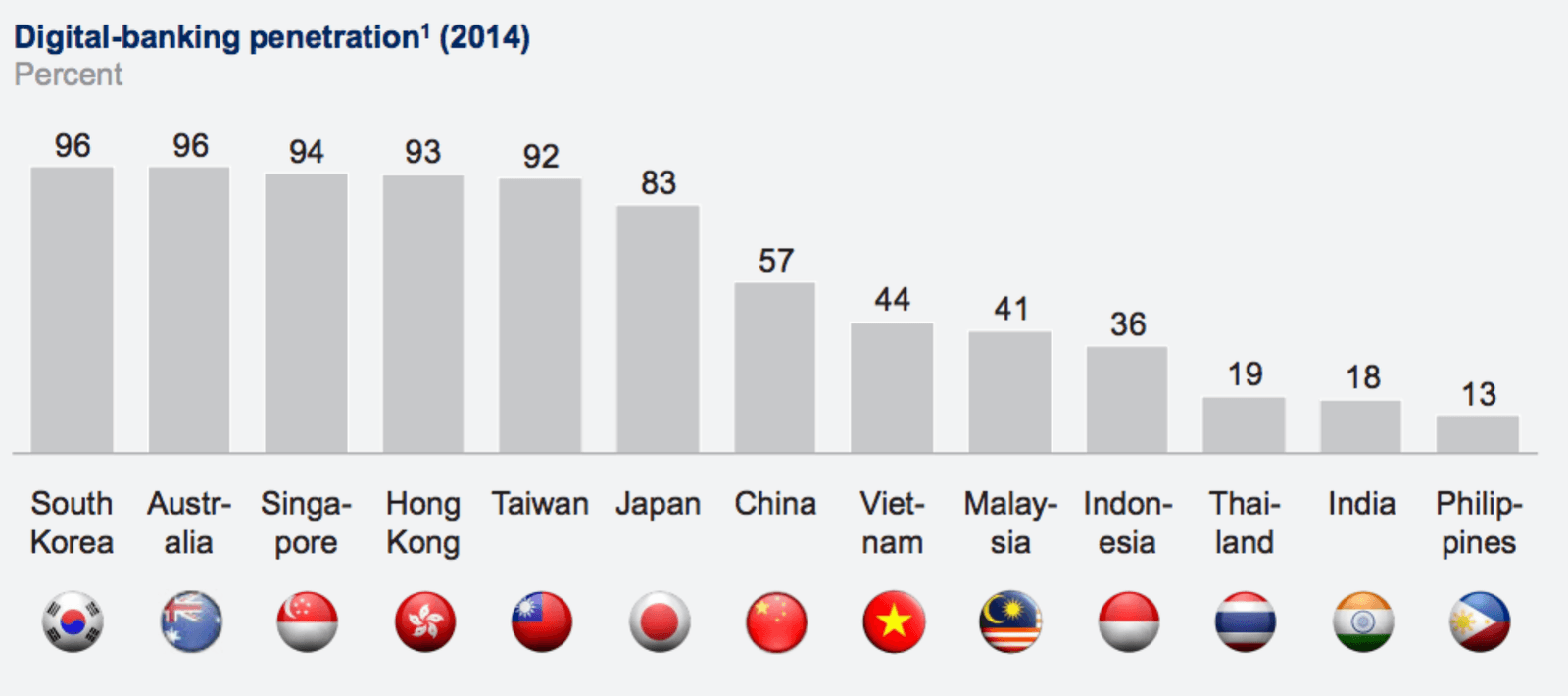
With the wide adoption of Digital Banking, the crooks have followed the money and financial institutions are top targets for cyber attacks. As per a report from Websense Security Lab, the average number of attack against financial services institution is four times higher than companies in other industries. Also the attacks are not limited to any specific region and are spread across the globe. The chart below list the top 10 countries by percentage of attacked users as per Kaspersky 2015 report, it clearly display Asia Pacific being a hot zone of activity.

Despite the security threats the Digital Banking era is here to stay. In this article we discuss about mitigation strategy and option available to disrupt the attack targeted towards banking channels.
Deep Dive into Threat
All financial institution takes due diligence in protecting their digital assets, with significant investments in technology to guard its datacenters be it on premise or on the cloud. With defense in depth, the crowned jewels are protected under layers on security, making it difficult to breach. Crackers have to discover Zero-days and advanced sophisticated techniques to break through the defense. On the other hand the endpoint used to access these digital services have little to no protection. Security on user devices can be flawed by outdated operating systems, lack of antivirus, infected by drive-by-downloads etc. This provides the crackers a wide range on options to infect the machine and dilute the security in the App centric world of the Digital Era. Cybercriminals do not need to be computer experts to cause this damage, the solution to infect and steal are available as software’s in the underground market.
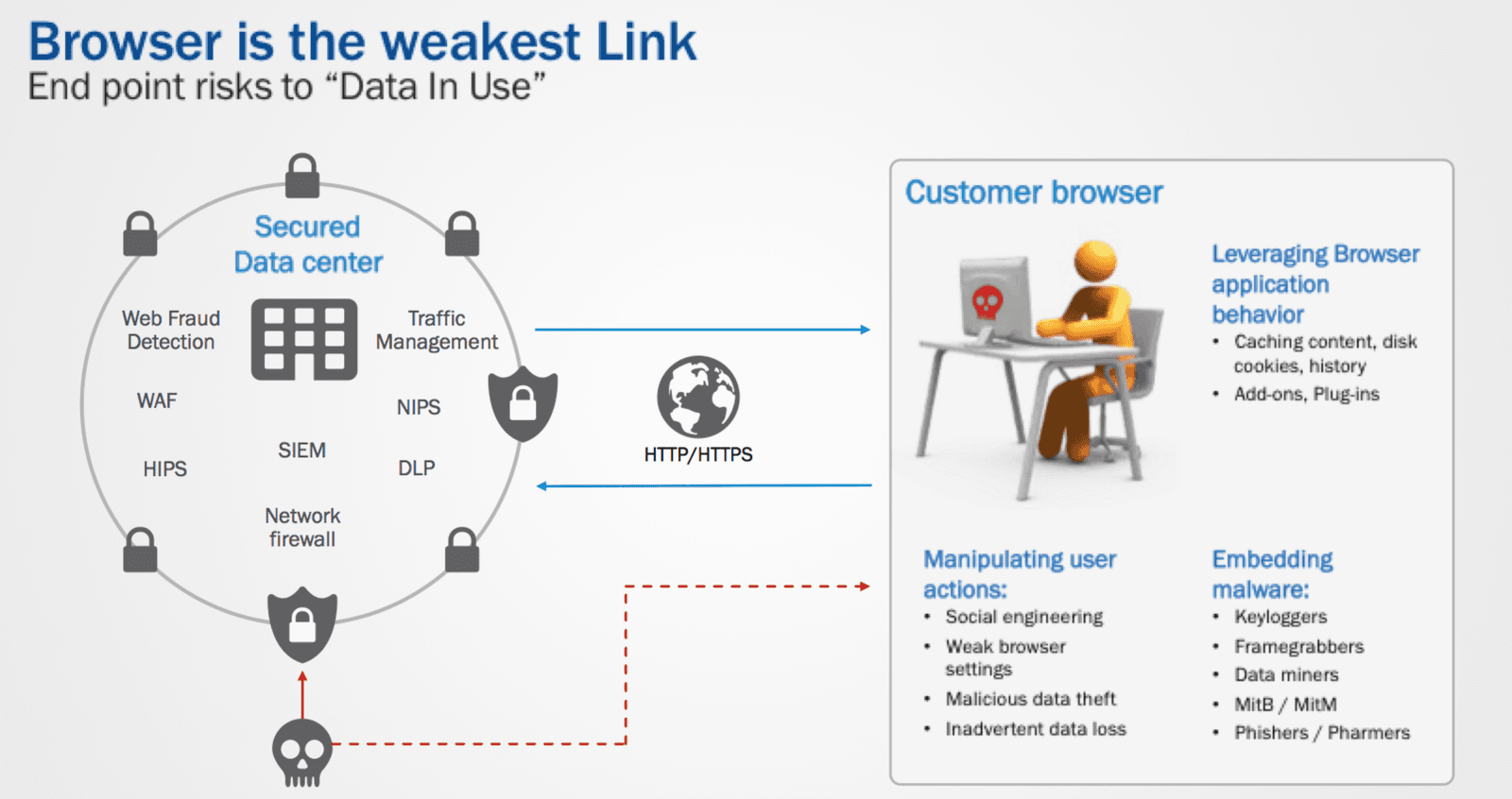
Toolset the Modern Malware Leverages on
Vector | Description |
Form Grabbing & Key Loggers | Form Grabbers Captures sensitive data from the HTML form element before a user submits the request.
Key loggers listens to key strokes and record data for theft
|
RAT & Back Connect | These are remote administration tools, which provide the remote operator controls to system. A malicious RAT enters a users device as Trojan and will hide itself from security software on the device |
Man In the Middle | In MITM, attacker dispatches the message between the browser and server, altering them in between to steal confidential information or hijack session |
Man In the Browser | MITB attack stealthily modifies the webpage and transaction content invisible to both user and the host server |
Mobile Malware | Trojans deployed with intention to steal SMS (defeating One Time Passwords), compromise the device DNS leading to leak of confidential information theft. |
Understanding the malware
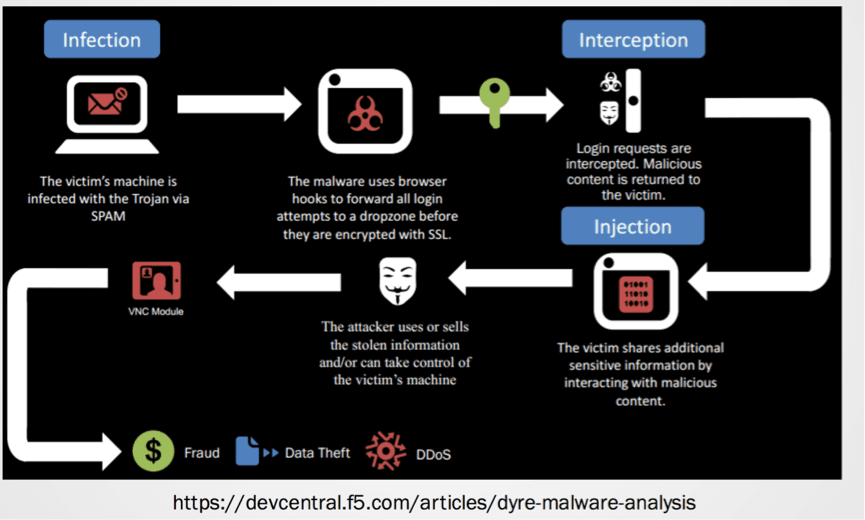
Modern malwares are written with on objective of stealing. Lets take a look the method of operation for one of the sophisticated malware Dyre.
- The victim’s machine is infected by virtue of a spam campaign.
- Once activated the malware hooks on to browser looking for users access to financial sites, and capturing login credentials. To deter second factor and additional risk based authentications, the malware displays html content with additional information required.
- All captured content is sent to a drop zone, where the attacker can use the credentials
Staying Ahead of the Threat
To mitigate and control the threat of modern day malwares, organization needs to put in place technology to detect and deter. Following table display some of the common principles.
Principle | Definition |
Malware Fraud Detection
| Detecting the malwares running on the machine |
Phishing Protection
| Protect copying and taking down of fraudulent websites copied from the original one |
Application-Level Encryption
| Prevent interception of sensitive information transferred by users to organizations while it’s still in the browser
|
Transaction Protection
| Protect against fraudulent dealings and suspicious activity with multi-layered transaction checks and risk scoring
|
Device and Behavioral Analysis
| Distinguish between actual users and automated transactions initiated by scripts and bots to prevent fraudulent payments and transfers
|
Securing the Mobile App
| Detects malware and jailbroken devices, protects against MiTM, keyloggers and fraudulent applications, and ensures information is rendered useless to attackers
|
A constant chase is on between good and bad. Technology is place (constantly changing) to defeat the modern day malwares. This technology can be broadly categorized as agent based vs. agent less solution.
| Agent Based | Agent less solution | Hybrid Solution |
Definition | The solution is delivered with an agent running on the desktop looking for attack signatures | Solution is delivered using web technology where JavaScript is used to detect the attack signature | A combination of a agent running on desktop and JavaScript is delivered along with the application |
Strength | The agent runs on privilege on the desktop and has the capability to detect and mitigate attacks | Client less deployment provides greater coverage. Protection cover is provided the moment it is turned on and doesn’t need any activation/installation by user | A combination that provides the strength of both agent and agentless solution |
Deployment | Mass rollout is required | No deployment needed on client side | Rollout needed for the agent solution |
Coverage | Coverage is only to the user who are accessing the desktop where the agent is installed | Covers user coming from any machine | Covers user coming from all machine |
Challenges | Deployment and mass rollout has problems with adoption.
A wide range of myriad operating system support also adds to the problem
| Problem mitigation/ removal of malware is not available | Costlier, as usually protection provided by agentless deployment covers most scenarios with respect to detection and alerts
|
Conclusion
In the era where the gains from attacking the financial sector is high, organizations needs to be aware of the threat and be at the top of the game to deter malwares from causing financial and brand harm.
Resources
- F5 Anti-Fraud Solution
- Digital Banking in Asia: What Consumer really wants
- Internet Penetration in Asia Pacific as of first quarter of 2015
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.