A new(ish) attack is making the rounds this week. I say new(ish) because the attack itself isn’t all that original. ICMP attacks have been around since the 90s. I also say ‘newish’ because this attack stands in stark contrast to the high-profile, volumetric attacks that make the news when they disrupt access to half the Internet. It’s a DoS (notice there’s only one “D”, not two) attack against well-known and widely used firewalls that can, with little effort, bring the business to its knees.
I won’t bog you down in details of how this ICMP (ping!) attack dubbed BlackNurse (for no obvious reason I’ve seen so far) works. There are tons of resources and commentary already available on the topic: Threat Post, El Reg, TDC SOC, or Netresecfor starters. What I did want to call attention to is the devastating disruption this attack could have on business, and in particular those businesses that rely heavily on cloud-based apps.
Because this one is not just about disrupting access to apps from the outside in, it’s about disrupting access to apps from the inside out. TDC SOC, in its report, specifically calls this out: “When an attack is ongoing, users from the LAN side will no longer be able to send/receive traffic to/from the Internet.”
LAN side. That’s the business side of the firewall.
We tend to view firewalls as the tactical response to keeping attackers out of our corporate networks. They’re the walls around the castle, the sandbags along the river, the firebreak in the wilderness trying to stop a rampaging fire. But firewalls have long served a dual purpose in the enterprise; that is, they have also controlled access from the inside out. Early on this was used to gate access to the adolescent Internet and continues to be a mechanism for enabling preventative measures against “phone home” attempts by malware and viruses that have managed to infect internal assets.
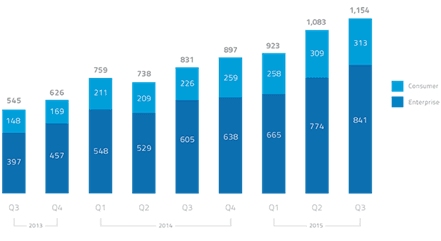
Today, the prevalence of cloud-based productivity apps requires inside-out access. And if we’re using cloud-based apps, we kinda need access to the Internet. Salesforce.com. Concur. Google Docs. Social media. The list of applications that reside outside the enterprise to which the business needs access goes on and on and continues to grow. As this nifty chart from Skyhigh Networks illustrates, the use of cloud-based applications in business has been steadily on the rise. In fact, its Q4 2015 report noted “The average organization now uses 1,154 cloud services.”
Business is inarguably dependent on the cloud.
That means disruption of access to those services is devastating to productivity, which is one of the key performance indicators in any business.
Thus, an attack like BlackNurse, which is relatively easy to conduct and requiring little more than a single laptop, is incredibly disruptive in spite of its relative simplicity. The goal of such attacks is simple: resource consumption. Low and slow attacks, whether targeting firewalls or web servers, are designed to tie up resources so the device cannot respond to legitimate requests. The problem is that such attacks are often more difficult to detect than their volumetric cousins. High volumes of traffic is noticeable. It sets off alarms and red lights and people immediately understand what is going on. We’ve focused a lot of energy in the past ten years to understanding how to combat such attacks and are luckily getting better at doing so.
But detecting a low and slow attack is more difficult. The CPU suddenly pegs at 100% and stops responding. Could be a software problem. Could be a hardware problem. Could be a lot of things. Sifting through logs to find the low volume of packets representative of this kind of attack is akin to the needle in a haystack problem. According to researchers the BlackNurse attacks generate only 15 to 18 Mbps. Yes, you read that right. There’s no “G” in that measure. That’s about 40 to 50K packets per second, which is nothing to modern firewalls. Conversely the DDoS attack recorded against Dyn measured in the 1 Tbps range. That’s a “T”, which is bigger than “G” and way bigger than “M”.
The answer to such attacks is usually to move apps to the cloud where firewall services are not constrained by such antiquated concepts as “limited resources” and are able to scale effortlessly and automagically. Except it’s not, because the business still has employees behind the corporate firewall that have to access those apps (and others). And it is their access that is being disrupted when the target is the corporate firewall that stands between them and “the cloud.”
It is productivity that suffers.
Businesses need to recognize the potentially perilous state caused by attacks that disrupt outbound traffic as well as inbound. While BlackNurse has a fairly simple mitigation already, there are likely to be others that are not so simple to mitigate. And in a world where we depend as much on the apps inside the firewall as those outside it, we need to take a close looker look at the possibilities of such attacks.
If you haven’t yet, then it’s past time to evaluate how dependent your business is (or will be) on apps “in the cloud” and how to best protect access to them in the face of threats designed specifically to deny business from going about its daily, well, business.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
