For five years we've asked thousands of respondents across every role in IT and around the world a simple question: What one thing would you never deploy an application without? In other words, what's the most important thing you can provide for your applications?
If you weren't part of the nearly 2000 respondents to our State of Application Services 2019 survey, I'll give you a moment to answer the question yourself so you can compare.
“The worst thing I could do is deploy an application without _____________________!”
Please select one response.
- Availability (such as load balancing and global server load balancing)
- Security (such as network firewall, web application firewall)
- Identity/Access (such as SSL VPN and Identity)
- Performance (such as caching and compression)
- Mobility (such as VDI and IOT gateway)
Go ahead, fix your answer firmly in your mind. Got it? Good.
If you answered "Security" then you're on board with the 60% of respondents who answered the same way. Security has become the most critical application service category in IT.
That wasn't always true.
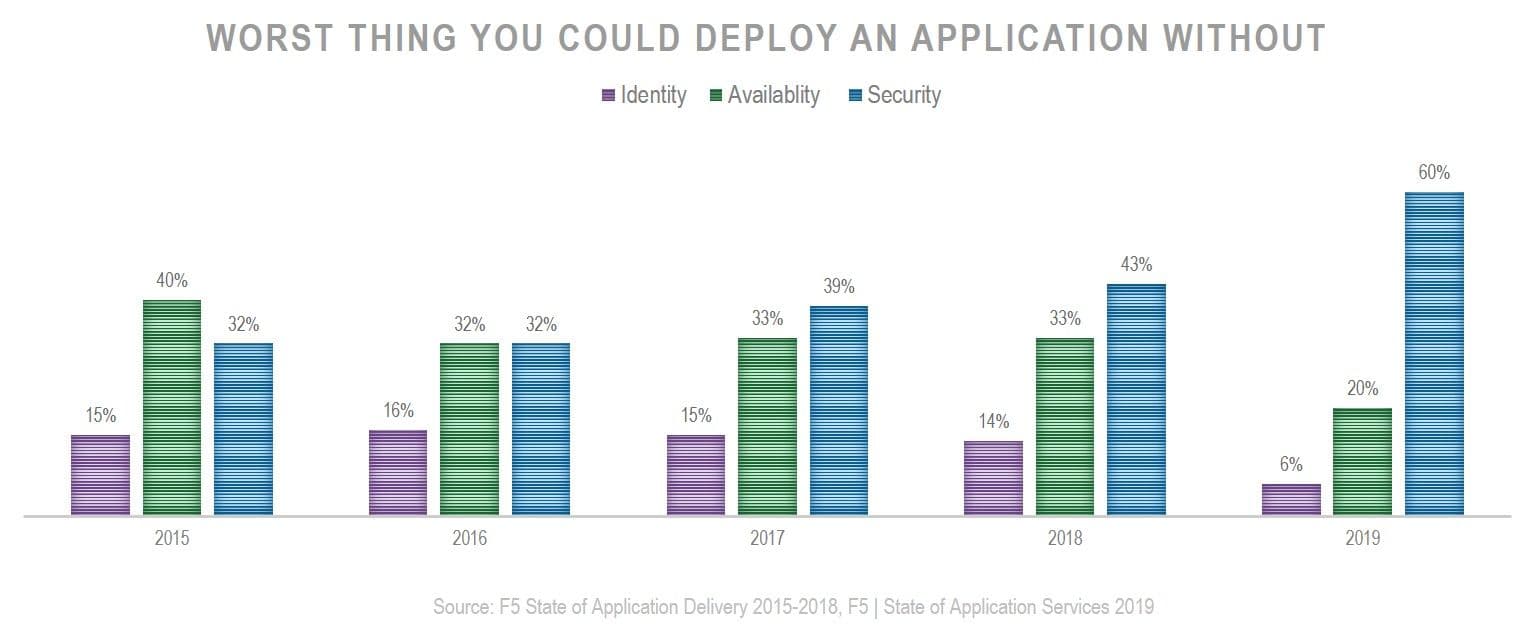
Availability took top honors back in 2015 and tied with security in 2016, but since then it's been all security all the way. Performance and mobility have never managed to threaten identity and access services, let alone security or availability. And now identity and access - and availability - are losing ground to security as well.
That isn't entirely surprising given the rather dramatic impact of security - or lack thereof - that's dominated headlines and twitter feeds for the past few years. While outages certainly can cause consternation amongst consumers, nothing compares to the angry feeding frenzy that takes place after a security breach is disclosed.
A security breach is a resume-generating incident. Outages rarely rise to that level of life-changing consequences. Outages are noted and used as anecdotes to promote availability by others. Outages are treated with the same patience and empathy associated with the "no blame" culture inherent to DevOps. We look for the cause and try to address it in blameless post mortems. Then we're transparent to the consumers impacted, noting details in blogs about "what went wrong" and "what we're doing to fix it."
And we're ultimately forgiven.
But a security incident that exposes our personal, private information? Someone will shoulder the responsibility, often on their way out the door. Pitchforks are raised, torches are lit, and tweets are sent.
Given intensity of public reaction to breaches, it's no surprise that respondents tagged security as absolutely necessary when deploying applications.
It's also no surprise that confidence in protecting apps against application layer attacks continues to flag with expansion to the cloud. In 2018, those with a low confidence (measured on a scale of 1 to 5 with 1 being low confidence and 5 being high confidence) in protecting against application layer attacks was at 17% of respondents. In 2019, that rose to one in five (20%). Those with high confidence decreased from 41% in 2018 to 37% in 2019.
The difference between confidence in protecting apps in the public cloud versus those on-premises is striking. More than half (53%) were more confident they could protect apps on-premises than they were about those in the public cloud (38%).
Interestingly, the importance placed on security services is not just hand wringing over fear of a breach. The deployment of security services to protect applications has a significant impact on confidence levels. Just under one-third (32%) of respondents who were not deploying a WAF were confident they could protect apps in the public cloud. That jumped to 41% for those who did employ the services of a WAF. On-premises showed even greater results. While 43% of those without a WAF on-premises had a high degree of confidence, that skyrocketed to 58% for those that did deploy a WAF.
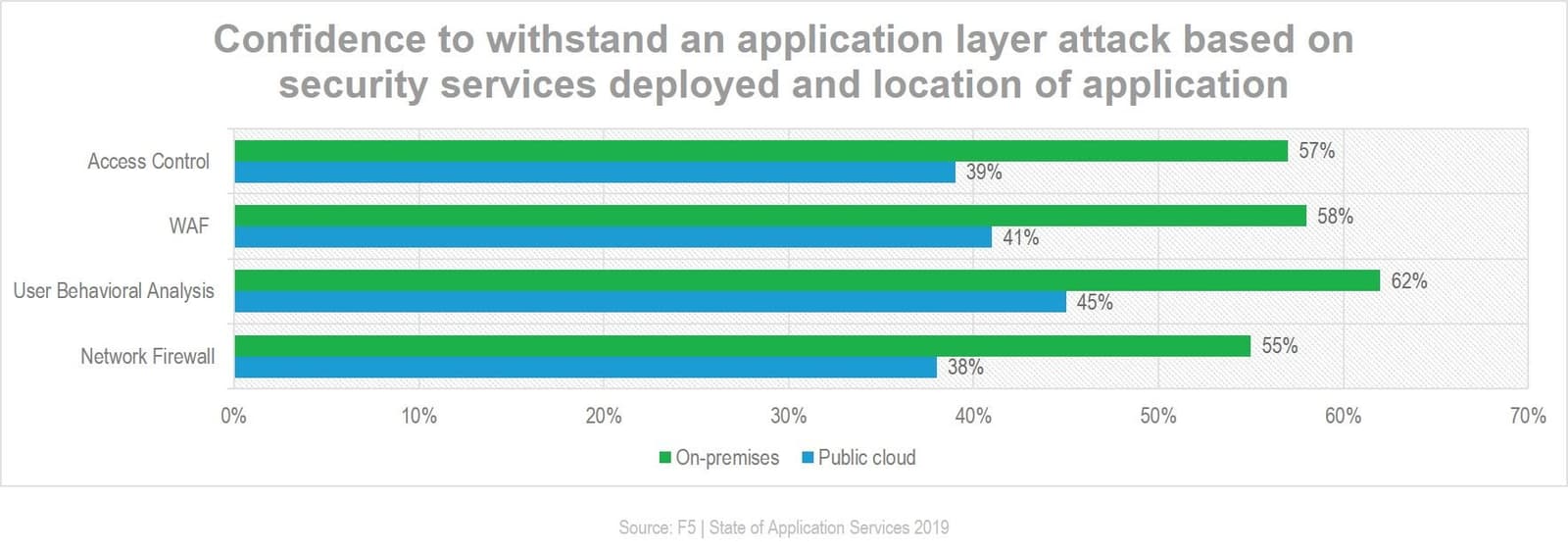
The security service with the biggest impact on confidence overall, however, was user behavioral analysis. Forty-five (45%) percent of respondents deploying user behavioral analysis in the public cloud were more confident they could protect apps against an application layer attack. While other security services showed similar gains in confidence when deployed in the public cloud, user behavioral analysis showed the biggest boost in confidence overall.
Security services remain a critical component of both confidence and an organization's strategy to preventing breaches and defending against attacks. The State of Application Services continues to show that security-related services are continuing to grow across all properties - on-premises and in the public cloud - as a way to combat the damage of doing business in a digital economy.
For more insights on security, cloud, digital transformation, and the exciting world of automation and orchestration, be sure to check out the State of Application Services 2019 report.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
