The CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), was originally designed to prevent bots, malware, and artificial intelligence (AI) from interacting with a web page. In the 90s, this meant preventing spam bots. These days, organizations use CAPTCHA in an attempt to prevent more sinister automated attacks like credential stuffing.
Almost as soon as CAPTCHA was introduced, however, cybercriminals developed effective methods to bypass it. The good guys responded with “hardened” CAPTCHAs but the result remains the same: the test that attempts to stop automation is circumvented with automation.
There are multiple ways CAPTCHA can be defeated. A common method is to use a CAPTCHA solving service, which utilizes low-cost human labor in developing countries to solve CAPTCHA images. Cybercriminals subscribe to a service for CAPTCHA solutions, which streamline into their automation tools via APIs, populating the answers on the target website. These shady enterprises are so ubiquitous that many can be found with a quick Google search, including:
- DeathbyCAPTCHA
- 2Captcha
- Kolotibablo
- ProTypers
- Antigate
This article will use 2Captcha to demonstrate how attackers integrate the solution to orchestrate credential stuffing attacks.
2Captcha
Upon accessing the site 2Captcha.com, the viewer is greeted with the image below, asking whether the visitor wants to 1) work for 2Captcha or 2) purchase 2Captcha as a service.

Option 1 – Work for 2Captcha
To work for 2Captcha, simply register for an account, providing an email address and PayPal account for payment deposits. During a test, an account was validated within minutes.
New workers must take a one-time training course that teaches them how to quickly solve CAPTCHAs. It also provides tips such as when case does and doesn’t matter. After completing the training with sufficient accuracy, the worker can start earning money.
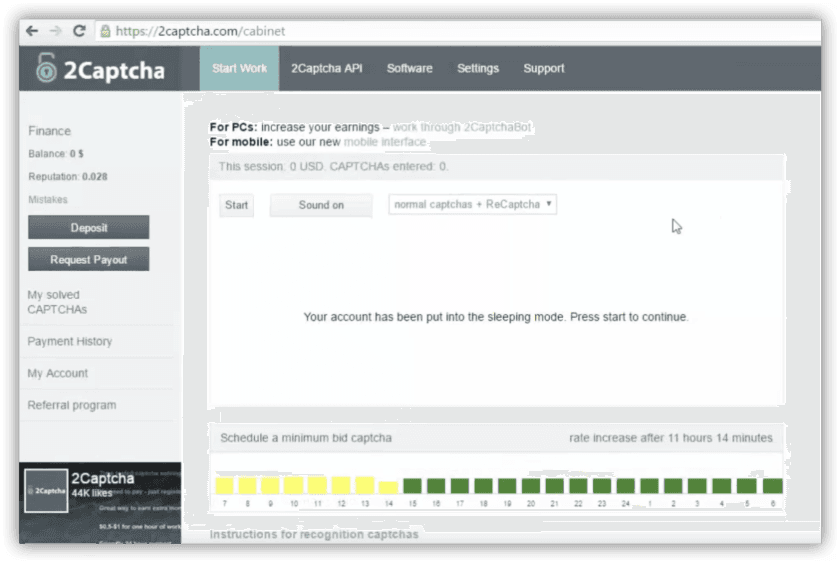
After selecting “Start Work,” the worker is taken to the workspace screen, which is depicted above. The worker is then provided a CAPTCHA and prompted to submit a solution. Once solved correctly, money is deposited into an electronic “purse,” and the worker can request payout whenever they choose. There is seemingly no end to the number of CAPTCHAs that appear in the workspace, indicating a steady demand for the service.
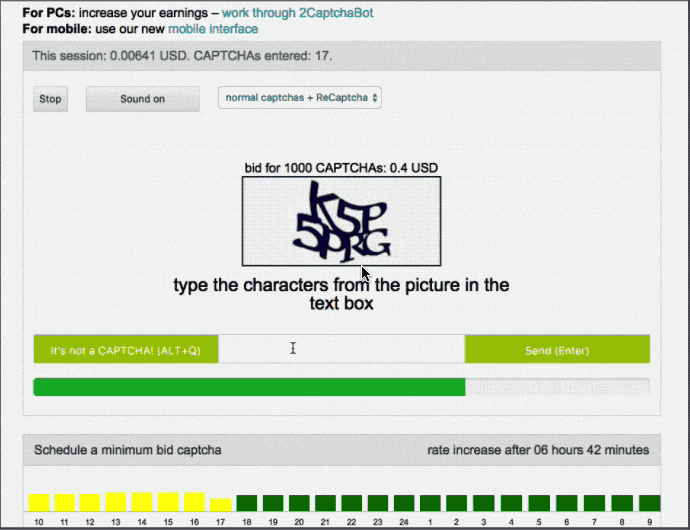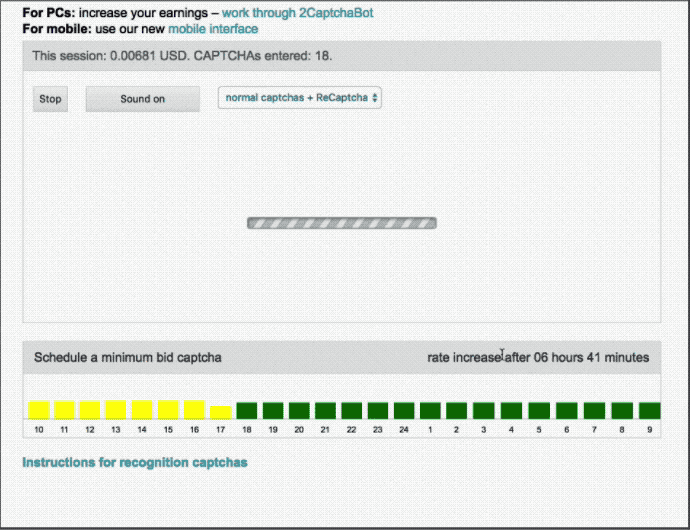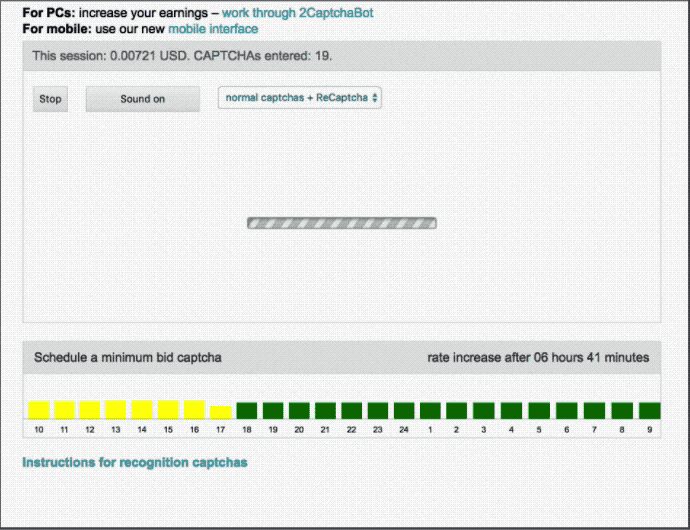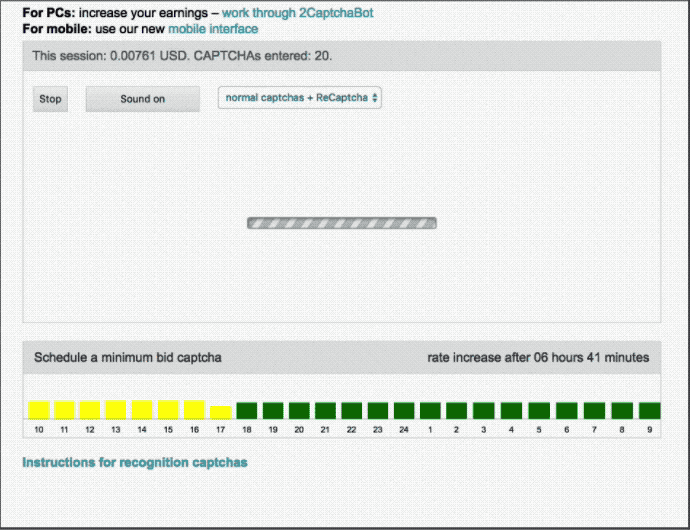
2Captcha workers are incentivized to submit correct solutions much like an Uber driver is incentivized to provide excellent service—customer ratings. 2Captcha customers rate the accuracy of the CAPTCHA solutions they received. If a 2Captcha worker’s rating falls below a certain threshold, she will be kicked off the platform. Conversely, workers with the highest ratings will be rewarded during times of low demand by receiving priority in CAPTCHA distribution.
Option 2 – 2Captcha as a service
To use 2Captcha as a service, a customer (i.e., an attacker) integrates the 2Captcha API into her attack to create a digital supply chain, automatically feeding CAPTCHA puzzles from the target site and receiving solutions to input into the target site.
2Captcha helpfully provides example scripts to generate API calls in different programming languages, including C#, JavaScript, PHP, Python, and more. The example code written in Python has been reproduced below:
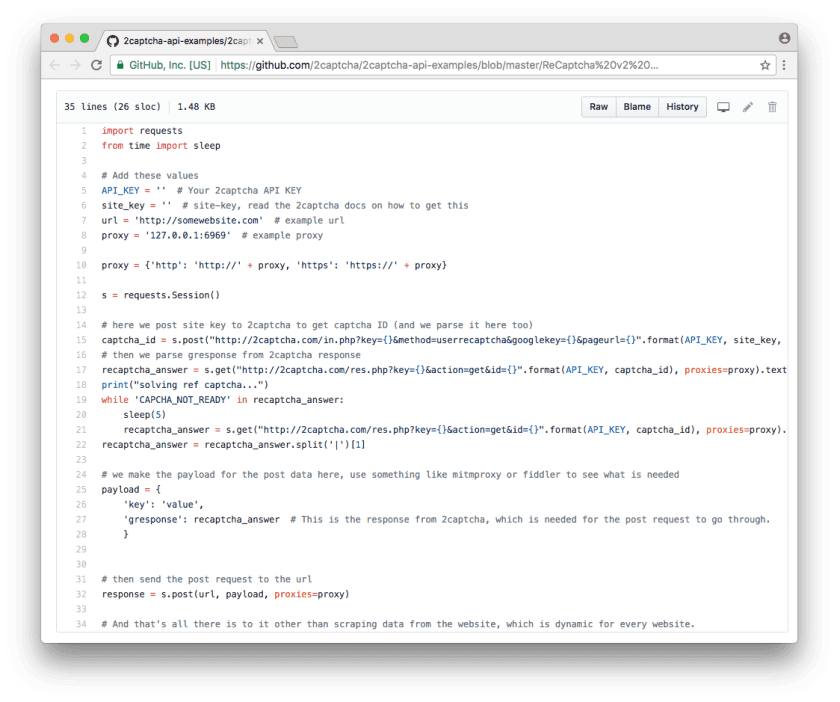
Integrating 2CAPTCHA into an Automated Attack
How would an attacker use 2Captcha in a credential stuffing attack? The diagram below shows how the different entities interact in a CAPTCHA bypass process:
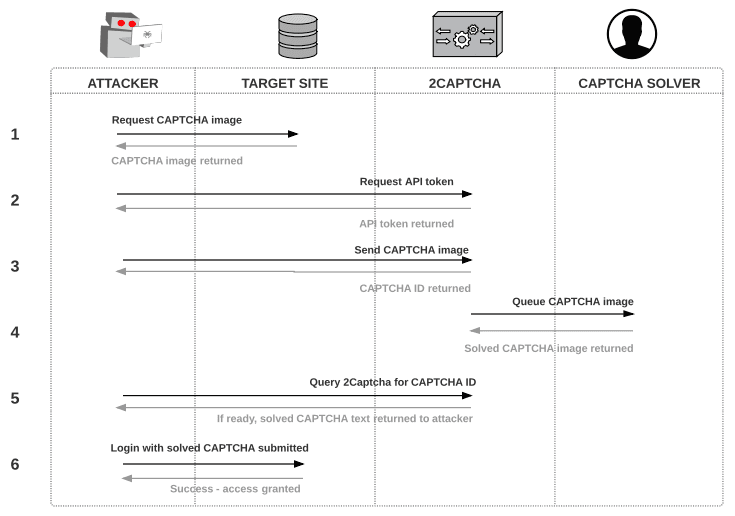
Technical Process:
- Attacker requests the CAPTCHA iframe source and URL used to embed the CAPTCHA image from the target site and saves it locally
- Attacker requests API token from 2Captcha website
- Attacker sends the CAPTCHA to the 2Captcha service using HTTP POST and receives a Captcha ID, which is a numerical ID attributed with the CAPTCHA image that was submitted to 2Captcha. The ID is used in step 5 for an API GET request to 2Captcha to retrieve the solved CAPTCHA.
- 2Captcha assigns the CAPTCHA to a worker who then solves it and submits the solution to 2Captcha.
- Attacker programs script to ping 2Captcha using CAPTCHA ID (every 5 seconds until solved). 2Captcha then sends the solved CAPTCHA. If the solution is still being solved, the attacker receives a post from 2Captcha indicating “CAPTCHA_NOT_READY” and the program tries again 5 seconds later.
- Attacker sends a login request to the target site with the fields filled out (i.e. a set of credentials from a stolen list) along with the CAPTCHA solution.
- Attacker iterates over this process with each CAPTCHA image.
Combined with web testing frameworks like Selenium or PhantomJS, an attacker can appear to interact with the target website in a human-like fashion, effectively bypassing many existing security measures to launch a credential stuffing attack.
Monetization & Criminal Ecosystem
With such an elegant solution in place, what does the financial ecosystem look like, and how do the parties each make money?
Monetization: CAPTCHA solver
Working as a CAPTCHA solver is far from lucrative. Based on the metrics provided on 2Captcha’s website, it’s possible to calculate the following payout:
Assuming it takes 6 seconds per CAPTCHA, a worker can submit 10 CAPTCHAs per minute or 600 CAPTCHAs per hour. In an 8 hour day that’s 4800 CAPTCHAs. Based on what was earned during our trial as an employee for 2Captcha (roughly $0.0004 per solution), this equates to $1.92 per day.
This is a waste of time for individuals in developed countries, but for those who live in locales where a few dollars per day can go relatively far, CAPTCHA solving services are an easy way to make money.
Monetization: Attacker
The attacker pays the third party, 2Captcha, for CAPTCHA solutions in bundles of 1000. Attackers bid on the solutions, paying anywhere between $1 and $5 per bundle.
Many attackers use CAPTCHA-solving services as a component of a larger credential stuffing attack, which justifies the expense. For example, suppose an attacker is launching an attack to test one million credentials from Pastebin on a target site. In this scenario, the attacker needs to bypass one CAPTCHA with each set of credentials, which would cost roughly $1000. Assuming a 1.5% successful credential reuse rate, the attacker can take over 15,000 accounts, which can all be monetized.
Monetization: 2Captcha
2Captcha receives payment from the Attacker on a per 1000 CAPTCHA basis. As mentioned above, customers (i.e. attackers) pay between $1 and $5 per 1000 CAPTCHAs. Services like 2Captcha then take a cut of the bid price and dole out the rest to their human workforce. Since CAPTCHA solving services are used as a solution at scale, the profits add up nicely. Even if 2Captcha only receives $1 per 1000 CAPTCHAs solved, they net a minimum of 60 cents per bundle. The owners of these sites are often in developing countries themselves, so the seemingly low revenue is substantial.
What about Google’s Invisible reCAPTCHA?
In March of this year, Google released an upgraded version of its reCAPTCHA called “Invisible reCAPTCHA.” Unlike “no CAPTCHA reCAPTCHA,” which required all users to click the infamous “I’m not a Robot” button, Invisible reCAPTCHA allows known human users to pass through while only serving a reCAPTCHA image challenge to suspicious users.
You might think that this would stump attackers because they would not be able to see when they were being tested. Yet, just one day after Google introduced Invisible reCAPTCHA, 2CAPTCHA wrote a blog post on how to beat it.
The way Google knows a user is a human is if the user has previously visited the requested page, which Google determines by checking the browser’s cookies. If the same user started using a new device or recently cleared their cache, Google does not have that information and is forced to issue a reCAPTCHA challenge.
For an attacker to automate a credential stuffing attack using 2Captcha, he needs to guarantee a CAPTCHA challenge. Thus, one way to bypass Invisible reCAPTCHA is to add a line of code to the attack script that clears the browser with each request, guaranteeing a solvable reCAPTCHA challenge.
The slightly tricky thing about Invisible reCAPTCHA is that the CAPTCHA challenge is hidden, but there is a workaround. The CAPTCHA can be “found” by using the “inspect element” browser tool. So the attacker can send a POST to 2Captcha that includes a parameter detailing where the hidden CAPTCHA is located. Once the attacker receives the CAPTCHA solution from 2Captcha, Invisible reCAPTCHA can be defeated via automation in one of two ways:
- JavaScript action that calls a function to supply the solved token with the page form submit
- HTML code change directly in the webpage to substitute a snippet of normal CAPTCHA code with the solved token input.
The fact that Invisible reCAPTCHA can be bypassed isn’t because there was a fatal flaw in the design of the newer CAPTCHA. It’s that any reverse Turing test is inherently beatable when the pass conditions are known.
As long as there are CAPTCHAs, there will be services like 2Captcha because the economics play so well into the criminal’s hands. Taking advantage of low cost human labor minimizes the cost of doing business and allows cybercriminals to reap profits that can tick upwards of millions of dollars at scale. And there will always be regions of the world with cheap labor costs, so the constant demand ensures constant supply on 2Captcha’s side.
The world doesn’t need to develop a better CAPTCHA, since this entire approach has fundamental limitations. Instead, we should acknowledge those limitations and implement defenses where the pass conditions are unknown or are at least difficult for attackers to ascertain.
Sources
Holmes, Tamara E. “Prepaid Card and Gift Card Statistics.” CreditCards.com. Creditcards.com, 01 Dec. 2015. Web.
Hunt, Troy. “Breaking CAPTCHA with Automated Humans.” Blog post. Troy Hunt. Troy Hunt, 22 Jan. 2012. Web.
Motoyama, Marti, Kirill Levchenko, Chris Kanich, and Stefan Savage. Re: CAPTCHAs–Understanding CAPTCHA-solving Services in an Economic Context. Proc. of 19th USENIX Security Symposium, Washington DC. Print.
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.