This article has been compiled based on contributions across the F5 Office of the CTO
Since we started surveying customers about their usage of application services, SSL VPN has maintained a spot in the "top five." More commonly referred to as remote access today, this application service provides secure access to corporate resources from anywhere via a client.
Right now, it's serving to enable hundreds of thousands of new remote employees working from home.
Based on our research, a significant percentage of remote access implementations have been in place for years. Thus, they were likely configured and tuned to optimize access based on traffic patterns and common application usage at the time. They have not necessarily been updated to reflect changes in those patterns and usage.
At least that's what we're seeing right now.
As COVID-19 continues its march across the globe, no industry has stressed remote access as much as healthcare. The use of remote access by hospital staff—especially in larger hospitals—has seen exponential growth in past weeks from a handful to ten thousand and more concurrent users. Hospital staff are working furiously on the frontlines and from home to help us through this pandemic. They suffer from long hours, lack of resources, and in many cases, isolation from their own families.
They should not have to suffer poor performance or inability to access critical apps too.
One way to increase capacity and improve performance for remote users is to update your remote access configuration to reflect the modern makeup of application traffic. Internet traffic today is largely video, with a healthy mix of live and on-demand. The rise of telemedicine—the use of live video by medical staff to discuss health with the community—during this pandemic is increasing and along with it, live video traffic.
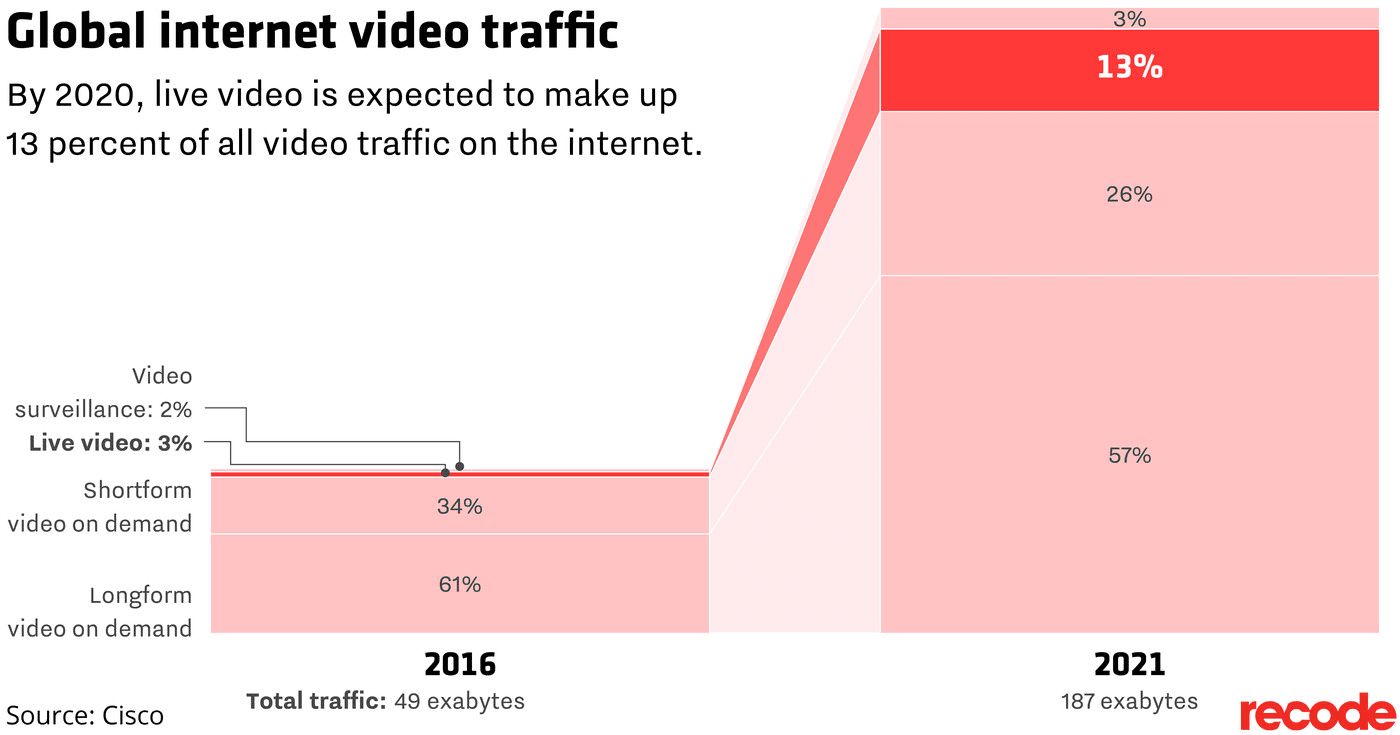
Also impinging on capacity and performance of remote access is our reliance on SaaS applications. Twenty-two percent (22%) of the corporate app portfolio today comprises SaaS applications such as Office 365, Teams, Salesforce, and G-Suite.
The dominance of video and SaaS traffic today is, in part, why remote access services are being overwhelmed.
How Remote Access Changes the Data Path
In a traditional remote access configuration, all traffic flows through the remote access service. All. Traffic. In the case of SaaS, this means app traffic bound for a cloud destination is routed through the remote access service.

This might not seem problematic until you consider that the remote access service might be located in Seattle but the SaaS application you're accessing is actually hosted in Virginia and you are in Minneapolis. Traffic has to traverse the country not once, but twice. This puts unnecessary stress on the remote access service and on users who spend more time waiting for the app to respond than they do working. We call this traffic pattern "backhauling" because all traffic is effectively "hauled" into the "back office" before it's sent to its intended destination.
This is also true for real-time video, which is largely provided by SaaS offerings today. All traffic is routed through the remote access service, which may contribute to stutters, stops, and garbled conversations. This is true for streaming video, as well. Many remote access clients send all traffic from the client through its complementary remote access service. For many folks right now, there is no distinction between "work" and "home" laptops. Relieving anxiety and stress with a quick video or an episode of a favorite comedy on Netflix or Hulu can be a necessary and helpful diversion. That traffic, too, can wind up traversing the remote access service and puts unnecessary stress on the service and the viewer.
Complicating the issue, web traffic today is often encrypted via SSL or TLS. Our service provider and enterprise customers see about 50% encrypted traffic, with a significant portion of non-encrypted traffic being video. Neither encrypted or video traffic benefit from compression capabilities offered by—and enabled on most—remote access services. The benefits of compression have largely been negated by the use of encryption as the process of encryption eliminates the repetitive strings most algorithms rely on to reduce content. By trying to compress such traffic, remote access services are effectively spinning their wheels and wasting cycles and time.
There are several configuration changes you can make to reduce the load on your remote access service and improve remote user experience.
Eliminating Backhaul for Non-Corporate Traffic
The purpose of remote access services is primarily to secure access and transmission to and from corporate network hosted applications. Basically, you don't want just anyone able to access internal apps and networks. SaaS and video conferencing—or streaming video, for that matter—doesn't reside on the corporate network and you can reduce the load on remote access by not processing it at a time like this.
To do that you can use a configuration option called split tunneling. This will allow you to specify that traffic bound for yourcompany.com should go through the remote access service while other traffic is handled normally. That is, it isn't backhauled through the remote access service. While we typically don't encourage this option for security reasons, it is particularly helpful right now to help boost performance of SaaS and real-time video applications if you've got a lot of employees working from home and your remote access service is overwhelmed.
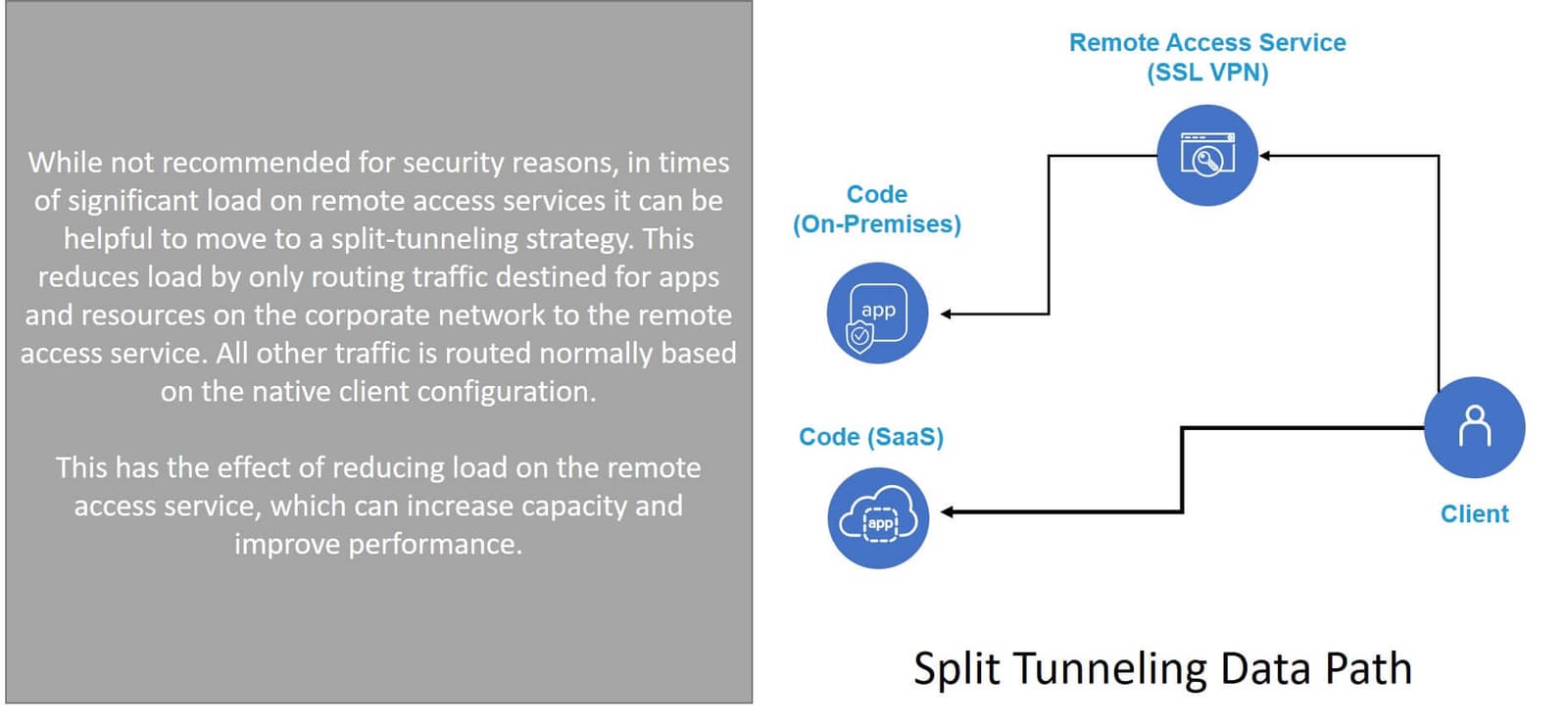
- If you're using F5 BIG-IP APM, you can find detailed instructions on how to enable and configure split tunneling in this knowledge base article (K55104964).
Turn Off Compression
The second thing you can do is to turn off compression options in your remote access service. This eliminates the problem of wasting cycles and effort and decreases load on the remote access service. That, in turn, will improve overall performance and capacity to serve more remote workers.
- If you're using F5 BIG-IP APM, you can find detailed instructions on how to disable compression in this knowledge base article (K19681382).
Also note that if you're experiencing issues with an internal app you may want to have someone check if it's got compression enabled, too. If it is secure (HTTPS) (and it should be) and compression is turned on, you may want to try disabling it. If your apps are running on NGINX, you can find more about managing compression here.
Other Avenues to Pursue
Another option is to encourage users to turn down the resolution of their video streams from 1080p to something lower (e.g., 480p). In large video-based meetings this can be a big boost and help ensure voice quality remains high. While reducing resolution can impact quality, it's often worth the stability and smoother performance you gain. This is something to consider for anyone that's struggling with video issues at home, especially with everyone in the household streaming, gaming, and trying to work at the same time.
If you're using F5 BIG-IP APM and you still have issues with load causing performance or availability challenges, there are other options you can pursue including taking advantage of hardware acceleration for TLS ciphers, checking your lease pools and SNAT, optimizing and reducing ACLs, and enabling traffic shaping.
- A comprehensive list of options you can use to tweak BIG-IP APM can be found in this knowledgebase article (K46161759).
- Or, if you prefer a deeper dive into deploying, configuring, and optimizing BIG-IP APM, this video will be helpful.
- And I would be remiss if I didn't mention the expert (both F5 and customer) help available on DevCentral. The community is ready and able to assist 24/7 and it's absolutely free of charge.
- Finally, here's a compiled list of potential situations you might encounter with BIG-IP APM during the COVID-19 outbreak to help you quickly identify the right solution.
Not all challenges with the current situation revolve around remote access. We have resources available to help with other business continuity challenges too.
Don't hesitate to reach out to sales or support staff if you're struggling with your remote access solution. We are wholly committed to helping our customers and communities get through this unprecedented time together and we are here to help.
Above all, stay safe.
About the Author

Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.
