There are at least three good answers and some not so good ones.
Strategy, particularly when it comes to technology, is often laid on the shoulders of executives. When it comes to security-related strategies, that’s often the CISO or, if there is no such role, the CIO.
But some organizations delegate responsibility for driving API security strategies to other roles. Developers, SREs, and even network professionals might own the strategy for securing APIs today.
Perhaps that’s because there’s no real research into what the results of those decisions might be. There are, after all, good reasons for developers to drive an API security strategy, just as there are good reasons to lay that responsibility on everyone who might touch an API is some way, whether during development, testing, or production.
In our recent research digging into API security, we asked each of our respondents—all API security decision makers—which roles in their organization were responsible for driving API security strategy. We found a mix of responses, from developers to network professionals to cross-organizational approaches.
But we also asked some nitty-gritty details about the types of security services organizations use to secure APIs. These are services like DDoS protection, access control, mTLS, and SSL. We used deployment of these services as a tangible representation of strategic execution because they are some of the controls needed to enforce policies derived from a security strategy. Then we looked at which of those services were deployed based on who drives API security strategy.
Quite frankly, we were stunned by the results.
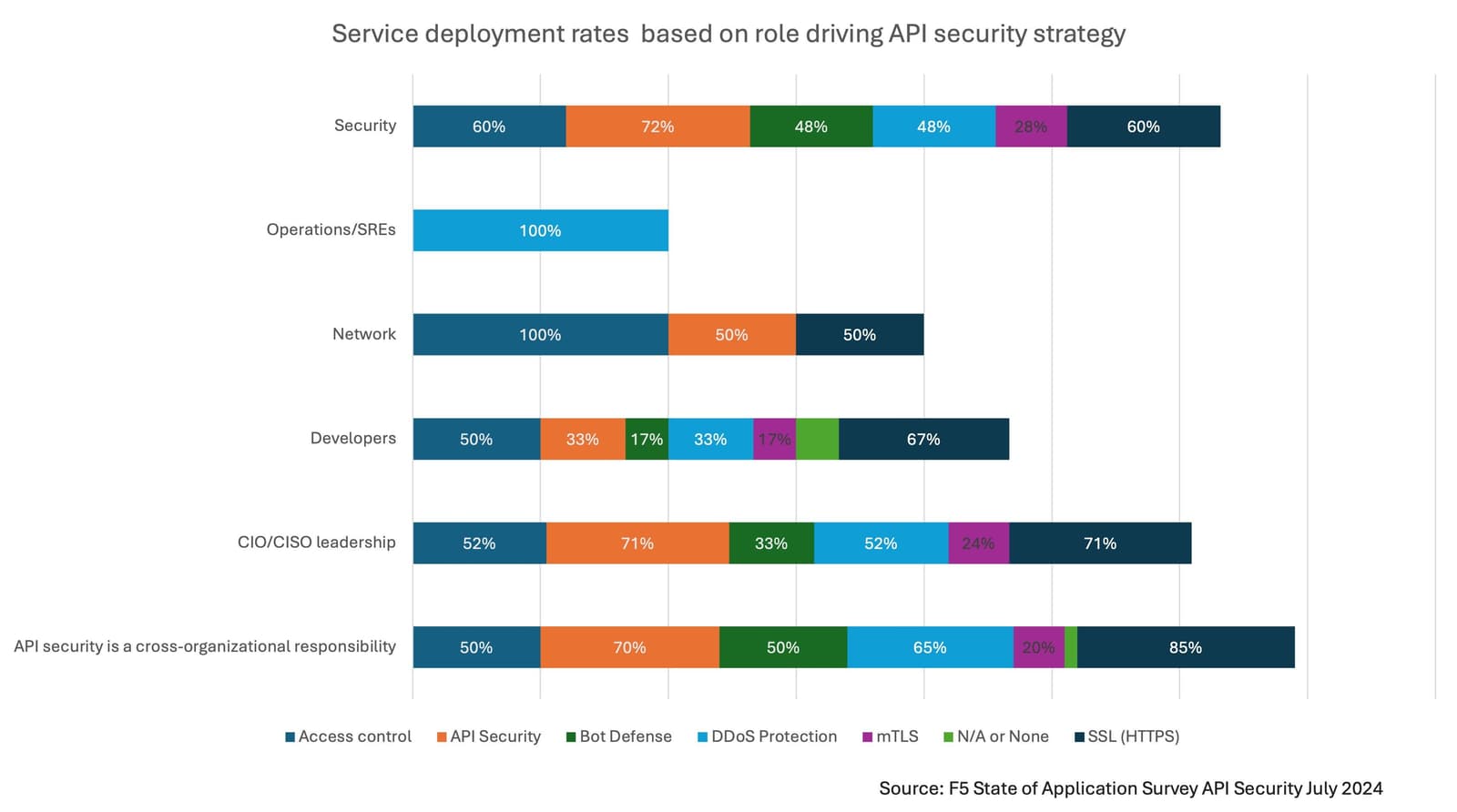
It turns out that the most comprehensive set of services was deployed when API security strategy is a cross-organizational responsibility, closely followed by the more general Security organization, and the CIO/CISO leadership.
Perhaps more distressing is that when SREs drive security strategy, API security is not incorporated until the test phase of the API lifecycle. When other choices for leading API security strategy are made, incorporation of API security largely begins either in the design or development phases. Even when network teams drive API security strategy, they tell us development is the phase in which to incorporate API security.
Now, the good news is that most organizations designate responsibility for defining API security strategy to one of those three. A mere 8% hand it off to developers, even fewer (3%) expect network professionals to handle it, and only 1% assign this task to SREs.
This closely aligns with the domain to which API security is assigned. Because that decision is largely influenced by who drives the strategy. When API security strategy is driven by CIO/CISO leadership or considered cross-organizational, API security winds up being distributed across four typical domains: API management, application security, network, and in security but separate from application security. Given that the services that defend and protect APIs can span multiple domains, that makes sense.
So if your organization assigns API security strategy to the CIO/CISO leadership, Security, or considers it a cross-organizational responsibility, congratulations! Your strategic approach is leading to comprehensive security controls through security services that defend and protect APIs from a wide variety of attacks.
You can dig even deeper into the secret lives of APIs by reading today’s press release and grabbing our latest report. Inside you’ll find more scary statistics, but also learn more about the ways that APIs are actually used inside the enterprise as well as the security capabilities organizations consider important to keeping APIs safe.
About the Author

Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.
