The video gaming business is booming. And not just booming, but mega booming.
Forced to stay inside, a broad and very diverse customer base has driven the video gaming market "in the US to increase 37% year-over-year to $3.3 billion, according to the market research firm NPD Group." (Source: Quartz)
This feeds an increasingly popular—and profitable—business model called "free to play." The game is free and offers the option to purchase in-game digital assets via microtransactions. Candy Crush, if you recall, was one of the first to make this model a reality. According to Gamestop, "the Candy Crush series of mobile games collectively made more than $1.5 billion in revenue from microtransactions in 2018 across iOS and Android. That works out to a staggering $4.2 million USD spent per day on average."
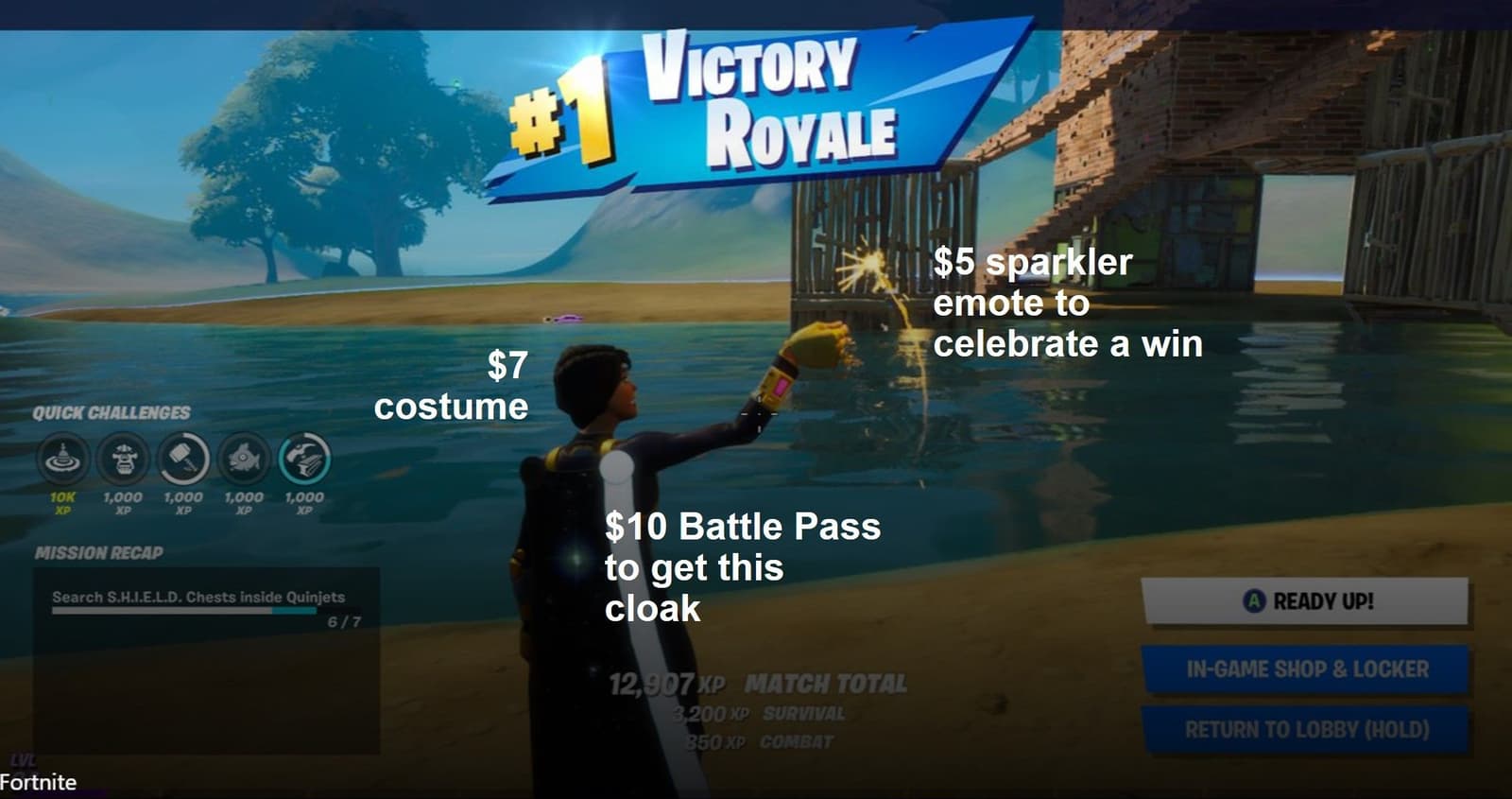
I will admit to contributing to this increase as our entire household spends our "entertainment" budget these days on in-game assets. Not games, necessarily, just in-game assets. Consider this screenshot. In it is about $22 worth of in-game, digital assets that have no impact on the game itself. They can't be used anywhere else. Most gamers have tens or hundreds of costumes and emotes and other digital cosmetics. The cost quickly adds up.
This model is increasingly profitable. In 2019, Epic Games' popular battle royale, Fortnite, "brought in revenues of $1.8 billion, according to data reported by SuperData Research, a Nielsen Company." (Source: Investopedia) Its business model is based entirely on microtransactions.
Microtransactions, of course, are backed by credit cards and payment processors like PayPal. That is theinformation attackers are really looking to get their hands on by gaining access to gaming accounts.
Which makes recent data analyzed by Atlas VPN both logical and terrifying. After all, "follow the money" is a phrase just as applicable to understanding motives of attackers as that of politicians. The firm found that "hackers attacked gamers a staggering 9.83 billion times from July 2018 to June 2020. In other words, players are hit with around 14 million attacks per day or 584 thousand attacks per hour." (Source: Information Security Buzz)
Gamers are not unaware of the potential impact. A survey on gamers' concerns conducted during the summer of 2020 found that they were most worried about their credit card information (49.1%) were their accounts to be hacked. (Source: Atlas VPN Blog) It should be noted that "access to their account" and "loss of in-game assets" were not far behind. The rise of competitive gaming and streaming gameplay as a source of income means these concerns are not as superficial as you might think.
These accounts are valuable to attackers, so it's no surprise to find such substantial attacks against them. Given that these accounts—like those in other industries—can be used across platforms (website, console, mobile phones) to gain access, they pose a lucrative target with multiple attack vectors for those savvy enough to go after them.
And if the account doesn’t have financial account data, they can always sell the digital account in the illicit game account market.
Yes. That's a thing that exists. It's against every game company's policy and terms of service, but it happens. Frequently.
Credential stuffing is a real threat to every industry with a digital presence—even video gaming. As we increasingly turn toward not just a digital economy, but a digital-first economy, this threat is one that needs to be addressed.
That's why it's important to continue to improve the technology used to detect and thwart fraud and abuse. Every industry can benefit from putting in place the best protection they can against credential stuffing attacks.
About the Author

Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.
