With the new Transport Layer Security (TLS) 1.3 specification published by the IETF last August, many organizations are considering adoption plans for the new standard. F5 commissioned a research project with Enterprise Management Associates to better understand how enterprises are adapting to the growing use of encryption overall. While some industry groups have expressed serious reservations over the ability to decrypt and inspect traffic for troubleshooting and possible malware using TLS 1.3, the good news is that a healthy percentage of respondents in the survey are either already in the process of enabling TLS 1.3 or plan to enable it soon. Another good sign is that a clear majority of the respondents in the survey indicated familiarity with TLS 1.3 on a technical level.
Multiple factors have driven the quick adoption plans for the new standard. That major web server and browser vendors have already implemented TLS 1.3 within their products is one. Another is the perceived benefits in improved privacy and end-to-end data security that come with the TLS 1.3 enhancements. Cryptographic protocols like TLS exist to help prevent adversaries from eavesdropping and tampering with data. However, concerns around application security monitoring are giving caution.
The use of encryption over the internet has grown significantly over the last few years. F5 Labs 2017 TLS Telemetry Report notes that 81% of web pages are now loading via HTTPS. While the use of encryption for the data center and enterprise networks increased the most over the last 18 months, enterprises will turn their attention to internally developed applications and web services in the next 18 months.
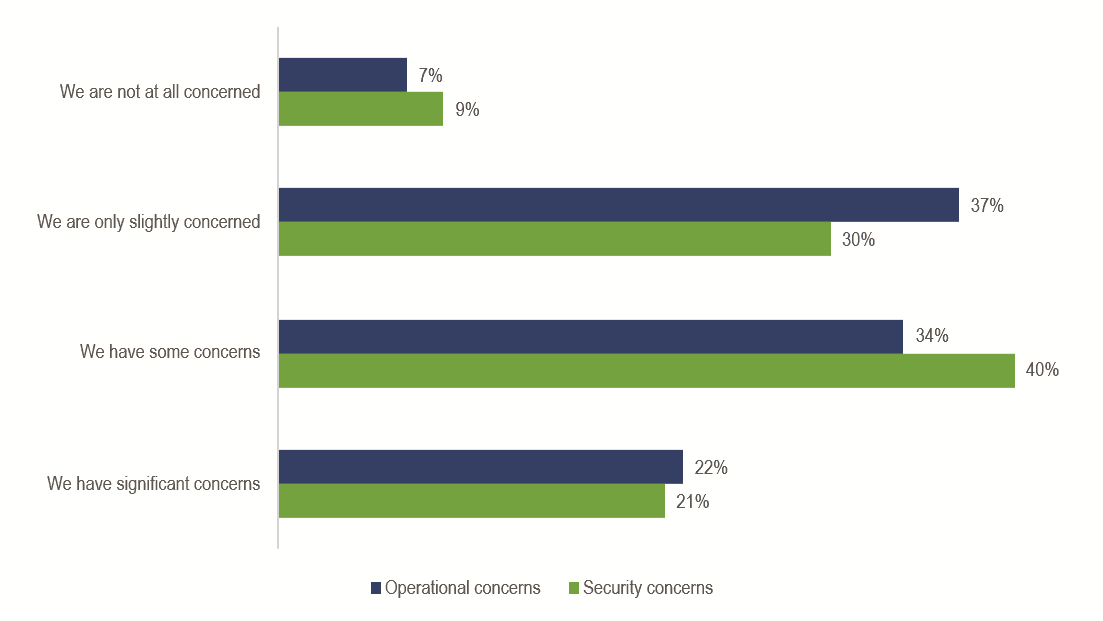
Given the implications of the TLS 1.3 specification, a clear majority of respondents expressed both operational and security concerns over implementing TLS 1.3 within their organizations. The survey found that 56% of all respondents expressed either some or significant operational concerns, while 61% expressed either some or significant security concerns.
The top security concern was Visibility into Application Security and the Data Center with 57% of respondents indicated the inability to monitor application security was their top concern.
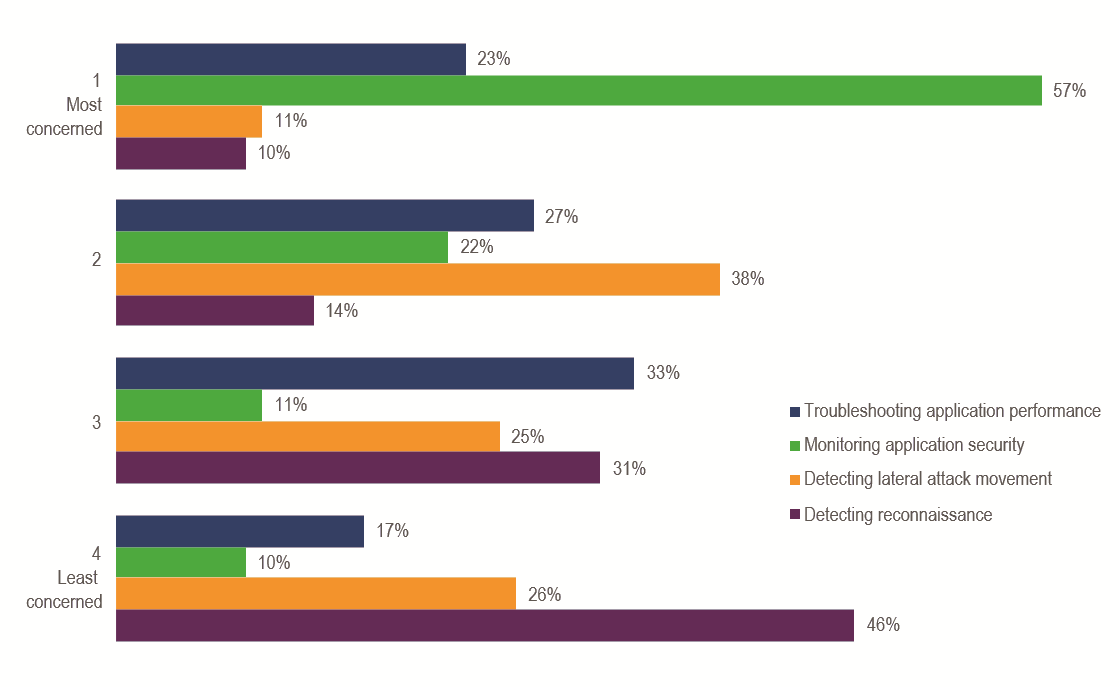
What are they afraid of?
Missing malicious behavior hidden in legitimate traffic. Only 6% were not at all concerned.
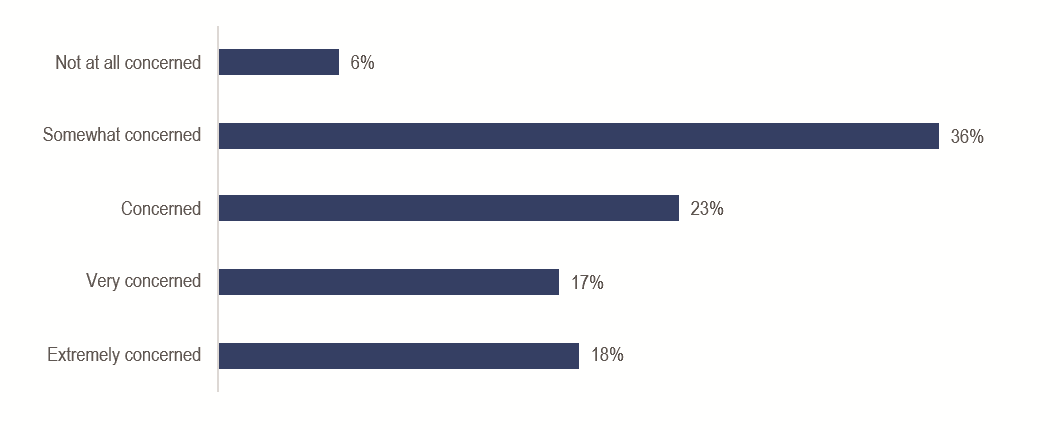
Despite those concerns, there is no going back. From a policy perspective, enterprises are clearly mandating the use of transport encryption to protect data, and TLS is the protocol of choice.
To understand how organizations are going to handle TLS 1.3 deployments along with strategies, policies, practices and concerns, access the full TLS 1.3 Adoption in the Enterprise Report here.
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.