Back in the old days, there was a near 1:1 relationship between network ports and applications. Port 53? That’s DNS. Port 22? SSH. Port 23? Telnet. Port 80? That’s the web site.
Note the singular, there. “The” web site. Not “one of two-hundred or so web applications delivered via HTTP.”
That’s an important distinction, as it helps to understand the shifting of the app perimeter from the edge (the network firewall) to somewhere closer to the app, on the interior of the data center (that’s the inner ward for those of you still working on the “castle” analogy for security).
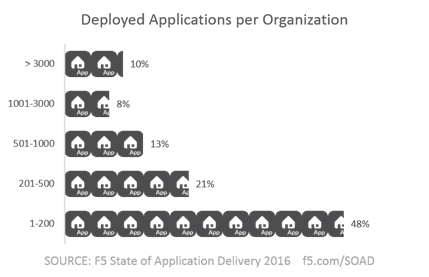
Our latest data shows that 65% of the applications delivered are HTTP-based. The remainder include the typical suspects: SSH, FTP, SMTP, and DNS, among other perhaps lesser known protocols. And how many applications are there in a typical enterprise? Our 2016 State of Application Delivery says a lot. Nearly half have between 1 and 200 apps deployed. The other half? Well, more than 200. A somewhat startling 10% have more than 3000 applications running right now.
More than half of those applications are HTTP. All of them traversing the same port on the stalwart defender of the data center: the network firewall. A network firewall that, more than likely, can’t tell the difference between those applications. That doesn’t care one whit whether it’s delivering JSON or HTML, whether it’s corporate or consumer facing, whether it should be accessed from a mobile device while you’re at home or not.
Those are increasingly important to securing apps. Whether it’s understanding how to determine whether an app payload is compromised or not (JSON is not HTML is not XML) and whether or not access should be allowed from a given location or device.

These are the kinds of questions application access control services care (much more than one whit) about. Like other application-affine services, application access control services are increasingly important in the overarching security strategy precisely because they can differentiate between applications and apply the appropriate policies. They aren’t just looking at protocols and ports, they’re digging deep in the entire conversation, evaluating a variety of variables (we call that context) in order to make a decision whether Bob should actually be allowed to access that highly sensitive app from his living room.
Organizations are aware of this, according to our research. 87% have 4 or more identity and access services deployed today. And unsurprisingly (to me, at least), it’s the faster growing category of app services in 2016, with 50% planning on deploying one of them in the next 12 months. I say unsurprising, because access to applications today necessarily includes cloud, where network firewalls aren’t able to extend control over access to applications. But identity and access services can.
Now, it’s certainly true that network firewalls remain the top service deployed by organizations, and I don’t expect that to change any time soon. They have and will continue to serve as a significant player in every organization’s security strategy. But as the cloud, mobile, and Internet of Things continues to expand the application landscape that must be protected, we’re going to continue to see an increase in the role and importance of application access control. Not only because network firewalls no longer have the visibility required to differentiate between apps delivered via the same protocol (HTTP) but because they’re no longer the only point of entry into those applications when a significant number of them are deployed out there, in the cloud.
For more details don’t forget to grab the full 2016 State of Application Delivery report.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
