It seems as though HTTP/2 was the technology equivalent of a flash in the pan. The ratified standard was released in 2015 with great fanfare. It was the first significant change to the lingua franca of the Internet since 1999.
And then, just as suddenly, it was quiet. The HTTP/2 Dashboard, created and maintained by researchers at several well-respected universities, fell quiet at the end of 2016. There hasn't been an update in adoption statistics since then. No one talks about it anymore. Its 15 minutes of fame have apparently passed.
Yet it has continued to gain traction in the background. Slowly but surely, HTTP/2 is making its way into the app stack.
HTTP/2 STILL OUTPACING IPv6
As an organization whose existence relies on applications - and in particular applications that run over HTTP variants - we have watched closely the adoption of HTTP/2. We started tracking HTTP/2 Gateway services in 2018 in our State of Application Services research. In 2018, 40% of respondents said they had deployed an HTTP/2 gateway. In 2019 that dropped to 33%. In the public cloud, 19% of respondents use an HTTP/2 gateway for some of their applications. It has managed to make the list of top five application services that will be deployed in the coming year for two straight years with 25% of respondents in 2019 planning to deploy.
The HTTP/2 Dashboard noted that just over 250,000 domains had announced support for HTTP/2 on Nov 16, 2016. There are over 1.8 billion sites on the Internet according to Netcraft, which tracks these sorts of things. W3Techs measures HTTP/2 usage at 33% of all websites, which tracks well against the 250,000 domains noted in 2016 if we limit the Internet to the top 1 million sites. Given that restriction, the numbers seem to all fall around 25-35% of sites that have adopted HTTP/2.
If you think that’s not fast enough, consider that IPv6 has been around far longer and only managed to gather 13.4% of websites as of January 2019.
HERE COMES HTTP/3
And now HTTP/3 is on the way with even more dramatic changes under the hood. If you aren't familiar with HTTP/3, you'll want to check out the IETF accepted proposal to rebrand Google's HTTP-over-QUIC as HTTP/3. Much in the same way that SPDY became the foundation for HTTP/2, QUIC is the foundation for HTTP/3.
But if you thought the changes to HTTP/2 were dramatic, you ain't seen nothing yet.
You see, QUIC - and therefore HTTP/3 - is based on UDP. Which is a rather drastic change from relying on good old reliable TCP. And unlike HTTP/2, which caved in and removed the requirement for encryption (a moot point as browser builders decided they'd only support encrypted HTTP/2 anyway), HTTP/3 will require it.
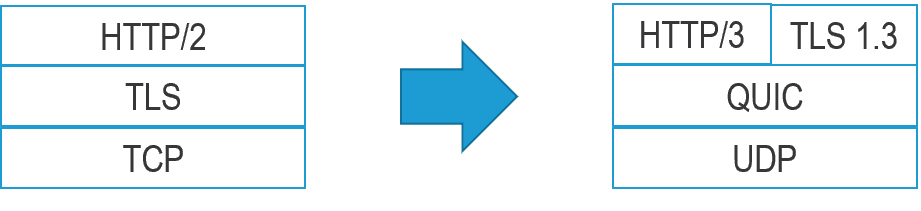
And while that's certainly a valid and perhaps even noble intention, the implications will have resounding impacts on infrastructure and architecture - especially for service providers. The movement of encryption up the stack to include pretty much everything combined with the move from TCP to UDP changes everything. Most security systems are not accustomed to examining the content carried by UDP very closely. Most of the traffic that makes use of UDP are utility and infrastructure services like DNS, and NTP. In the new world of HTTP/3, failure to closely inspect payloads could be dangerous. After all, the content being passed through might very well be malicious. It could be bots. It could be an attack. It could be anything.
Encryption requirements too, make it more difficult for “middle boxes” to inspect traffic. Such inspection is critical to maintain application and data security. The change in transport layer protocols may also prove problematic. Security services are often built based on the premise that application (HTTP for the most part) traffic will be transported over TCP. TCP is a reliable, connection-oriented protocol. The change to UDP could have a significant impact on the ability of security infrastructure to parse and analyze application traffic simply because UDP is a datagram-based (packet) protocol and can be, well, unreliable.
A SLOW ROAD TO ADOPTION
Adoption of HTTP/3 will likely be slow while HTTP/2 continues its slow but steady spread. After all, most of the web continues to rely on good old HTTP/1.x. It will be some time before HTTP/2 overtakes HTTP/1.x and the likelihood of migrating entire infrastructure and application stacks against so soon is low.
The impact on security infrastructure, too, is likely to keep adoption slow until security service providers are able to adapt. Zero trust initiatives, which incorporate greater context from clients - like device id and reputation - may ultimately prove to be a boon here as security migrates to a more comprehensive strategy to protect applications. Maturation and adoption of zero trust technologies may provide an answer to dealing with the security challenges of HTTP/3. As security services become more reliant on identifying bad actors in real-time it mitigates the risk of being unable to easily peruse payloads for malicious activity.
HTTP/3 isn't expected to be released until the summer of 2019. Given the slow but steady adoption of HTTP/2 and the security challenges posed by HTTP/3, the latter is likely to face a long, uphill road to adoption for the foreseeable future.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
