In F5’s The State of Application Strategy in 2022 report, 90% of IT decision makers reported that their organizations manage between 200 and 1,000 apps, up 31% from five years ago. In another survey by Enterprise Strategy Group about how Modern App Security Trends Drive WAAP Adoption (May 2022, available courtesy of F5), the majority of IT decision makers said application security has become more difficult over the past 2 years, with 72% using a WAF to protect their web applications. As organizations continue their digital transformation and web applications continue to proliferate, so too does the need for increased WAF protection. But as with most tools, the more WAFs you have, the harder they are to manage consistently and effectively.
The challenges of managing WAFs at scale include:
- Lack of adequate visibility into application‑layer attack vectors and vulnerabilities, especially given the considerable number of them
- Balancing WAF configurations between overly permissive or overly protective; it’s time‑consuming to fix the resulting false positives or negatives, especially manually and at scale
- Ensuring consistent application policy management at high volumes, which is required to successfully identify suspicious code and injection attempts
- Potential longtail costs – some extremely damaging – of failure to maintain even a single WAF in your fleet, including monetary loss, damage to reputation and brand, loss of loyal customers, and penalties for regulatory noncompliance
- The need to support and update WAF configuration over time
WAF management at scale means both security and application teams are involved in setup and maintenance. To effectively manage WAFs – and secure applications properly – they need proper tooling that combines holistic visibility into attacks and WAF performance with the ability to edit and publish configurations on a global scale. In this blog, we explore the benefits of centralized security visualization and configuration management for your WAF fleet.
Actionable Security Insights at Scale with Centralized WAF Visibility
To easily manage WAFs at scale and gain the insight needed to make informed decisions, you need a management plane that offers visibility across your WAF fleet from a single pane of glass. You can view information about top violations and attacks, false positives and negatives, apps under attack, and bad actors. You can discover how to tune your security policies based on attack graphs – including geo‑locations – and drill down into WAF event logs.
How NGINX Can Help: F5 NGINX Management Suite Security Monitoring
We are happy to announce the general availability of the Security Monitoring module in F5 NGINX Management Suite, the unified traffic management and security solution for your NGINX fleet which we introduced in August 2022. Security Monitoring is a visualization tool for F5 NGINX App Protect WAF that’s easy to use out of the box. It not only reduces the need for third‑party tools, but also delivers unique, curated insights into the protection of your apps and APIs. Your security, development, and Platform Ops teams gain the ability to analyze threats, view protection insights, and identify areas for policy tuning – making it easier for them to detect problems and quickly remediate issues.
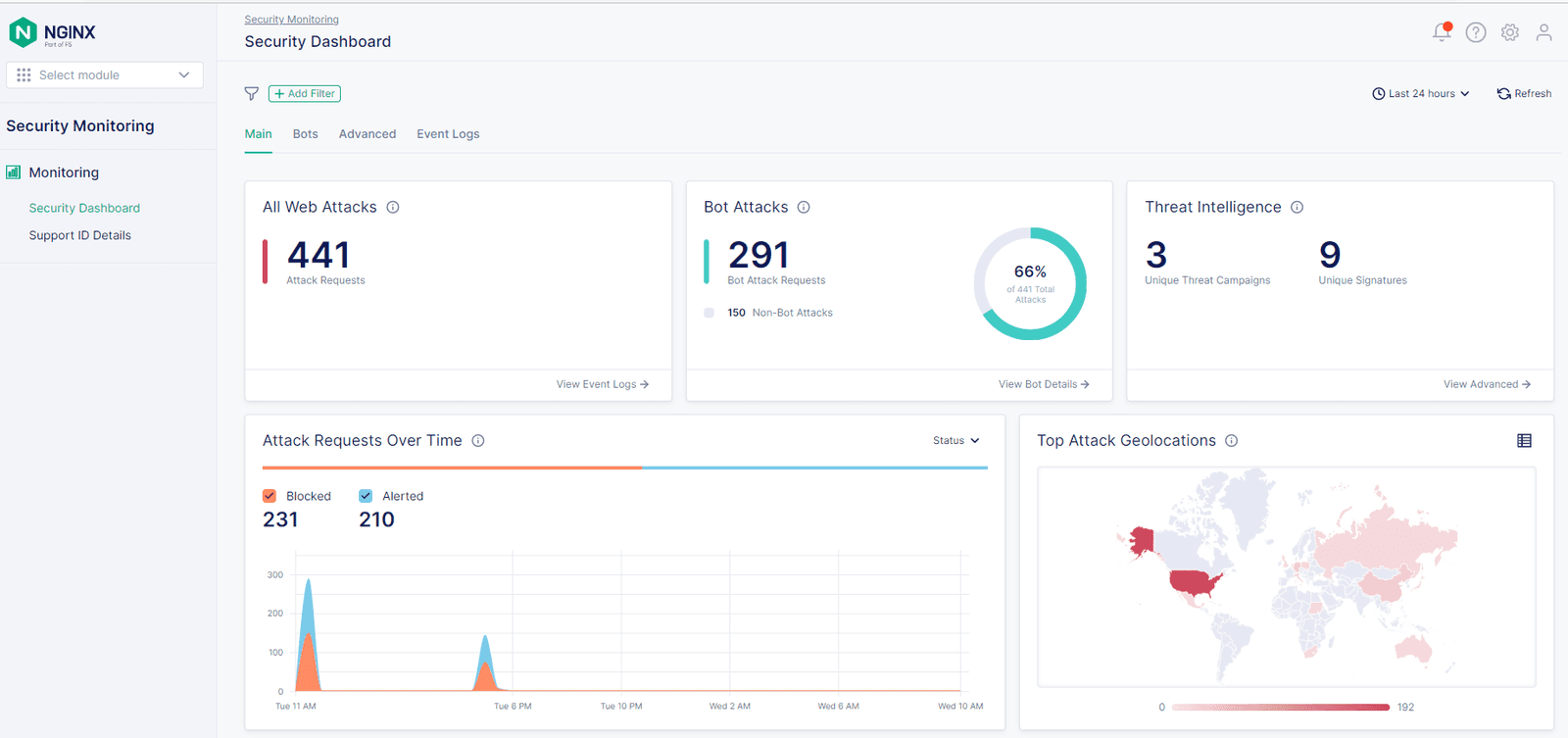
With the Security Monitoring module, you can:
- Use dashboards to quickly see top violations, bot attacks, signatures, attacked instances, CVEs, and threat campaigns triggered per app or in aggregate. Filter across various security log parameters for more detailed analysis.
- Make tuning decisions with insights into signature‑triggered events, including information about accuracy, level of risk, and what part of the request payload triggered signatures for enforcement.
- Discover top attack actors (client IP addresses), geolocation vectors, and attack targets (URLs) per app or in aggregate.
- See WAF events with details about requests and violations, searchable by request identifiers and other metrics logged by NGINX App Protect WAF.
 
Configuration Management for Your Entire NGINX App Protect WAF Fleet
While awareness and visibility are vital to identifying app attacks and vulnerabilities, they’re of little value if you can’t also act on the insights you gain by implementing WAF policies that detect and mitigate attacks automatically. The real value of a WAF is defined by the speed and ease with which you can create, deploy, and modify policies across your fleet of WAFs. Manual updates require vast amounts of time and accurate recordkeeping, leaving you more susceptible to attacks and vulnerabilities. And third‑party tools – while potentially effective – add unnecessary complexity.
A centralized management plane enables configuration management with the ability to update security policies and push them to one, several, or all your WAFs with a single press of a button. This method has two clear benefits:
- You can quickly deploy and scale policy updates in response to current threats across your total WAF environment.
- Your security team has the ability to control the protection of all the apps and APIs your developers are building.
How NGINX Can Help: F5 NGINX Management Suite Instance Manager – Configuration Management
You can now manage NGINX App Protect WAF at scale with the Instance Manager module in NGINX Management Suite. This enhancement gives you a centralized interface for creating, modifying, and publishing policies, attack signatures, and threat campaigns for NGINX App Protect WAF, resulting in more responsive protection against threats and handling of traffic surges.
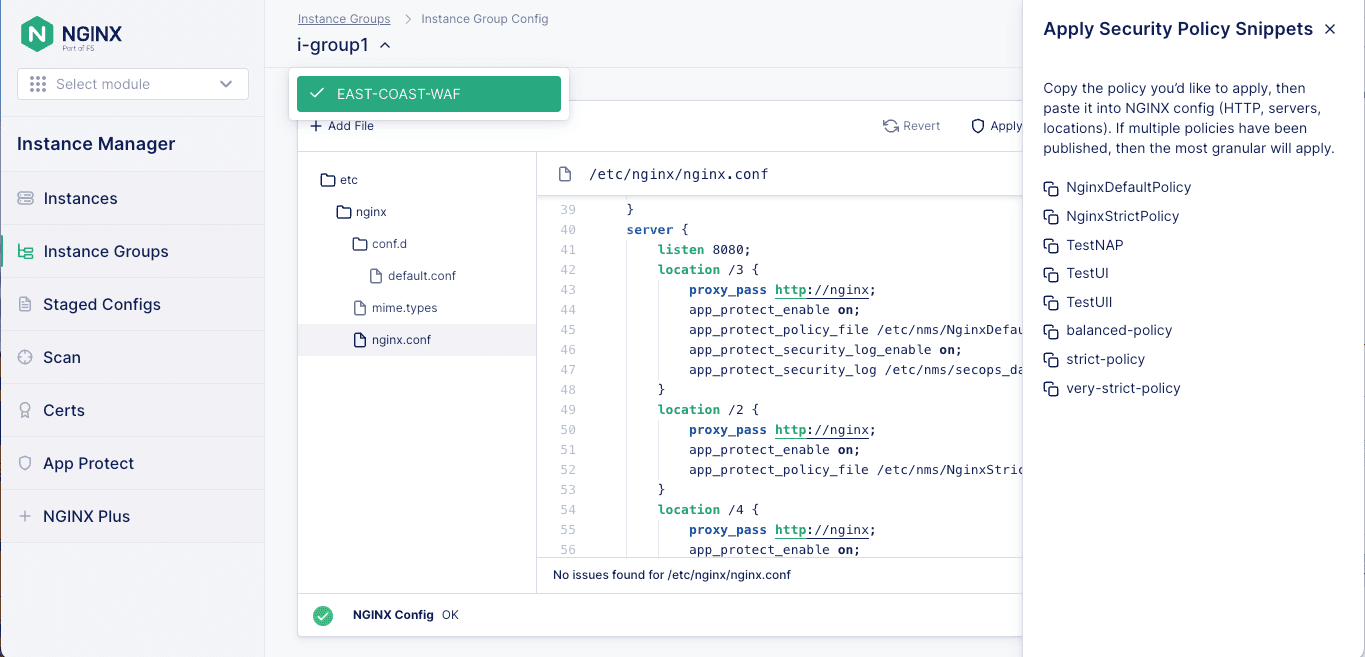
With the Instance Manager module, you can:
- Define configuration objects in a single location and push them out to the NGINX App Protect WAF instances of your choosing. The objects include security policies and deployments of attack signature updates and threat campaign packages.
- Choose a graphical user interface (GUI) or REST API for configuration management. With the API, you can deploy configuration objects in your CI/CD pipeline.
- See which policies and versions are deployed on different instances.
- Use a JSON visual editor to create, view, and edit NGINX App Protect WAF policies, with the option to deploy instantly.
- Compile NGINX App Protect WAF policies before deployment, to decrease the time required for updates on WAF instances.
- View WAF logs and metrics through NGINX Management Suite Security Monitoring.
 
Take Control of Your WAF Security with NGINX Management Suite
To learn more, visit NGINX Management Suite and Instance Manager on our website or check out our documentation:
Ready to try NGINX Management Suite for managing your WAFs? Request your free 30-day trial.
About the Author

Related Blog Posts
Automating Certificate Management in a Kubernetes Environment
Simplify cert management by providing unique, automatically renewed and updated certificates to your endpoints.

Secure Your API Gateway with NGINX App Protect WAF
As monoliths move to microservices, applications are developed faster than ever. Speed is necessary to stay competitive and APIs sit at the front of these rapid modernization efforts. But the popularity of APIs for application modernization has significant implications for app security.
How Do I Choose? API Gateway vs. Ingress Controller vs. Service Mesh
When you need an API gateway in Kubernetes, how do you choose among API gateway vs. Ingress controller vs. service mesh? We guide you through the decision, with sample scenarios for north-south and east-west API traffic, plus use cases where an API gateway is the right tool.
Deploying NGINX as an API Gateway, Part 2: Protecting Backend Services
In the second post in our API gateway series, Liam shows you how to batten down the hatches on your API services. You can use rate limiting, access restrictions, request size limits, and request body validation to frustrate illegitimate or overly burdensome requests.
New Joomla Exploit CVE-2015-8562
Read about the new zero day exploit in Joomla and see the NGINX configuration for how to apply a fix in NGINX or NGINX Plus.
Why Do I See “Welcome to nginx!” on My Favorite Website?
The ‘Welcome to NGINX!’ page is presented when NGINX web server software is installed on a computer but has not finished configuring
