Two converged platforms now define how organizations secure and deliver their most critical assets: Secure Access Service Edge (SASE) for the hybrid workforce, and an Application Delivery and Security Platform (ADSP) for the hybrid application estate. Understanding how these platforms differ and why they complement each other is key to designing resilient architectures.
SASE vs. ADSP
In many ways, SASE and ADSP are similar. They are both converged networking and security platforms. Both are deployed via hardware, software, and SaaS. And both include the concept of a single console across everything serving NetOps, SecOps, PlatformOps, DevOps, and other operational teams. However, they are also very different technologies; one focuses on employees and the other on applications.
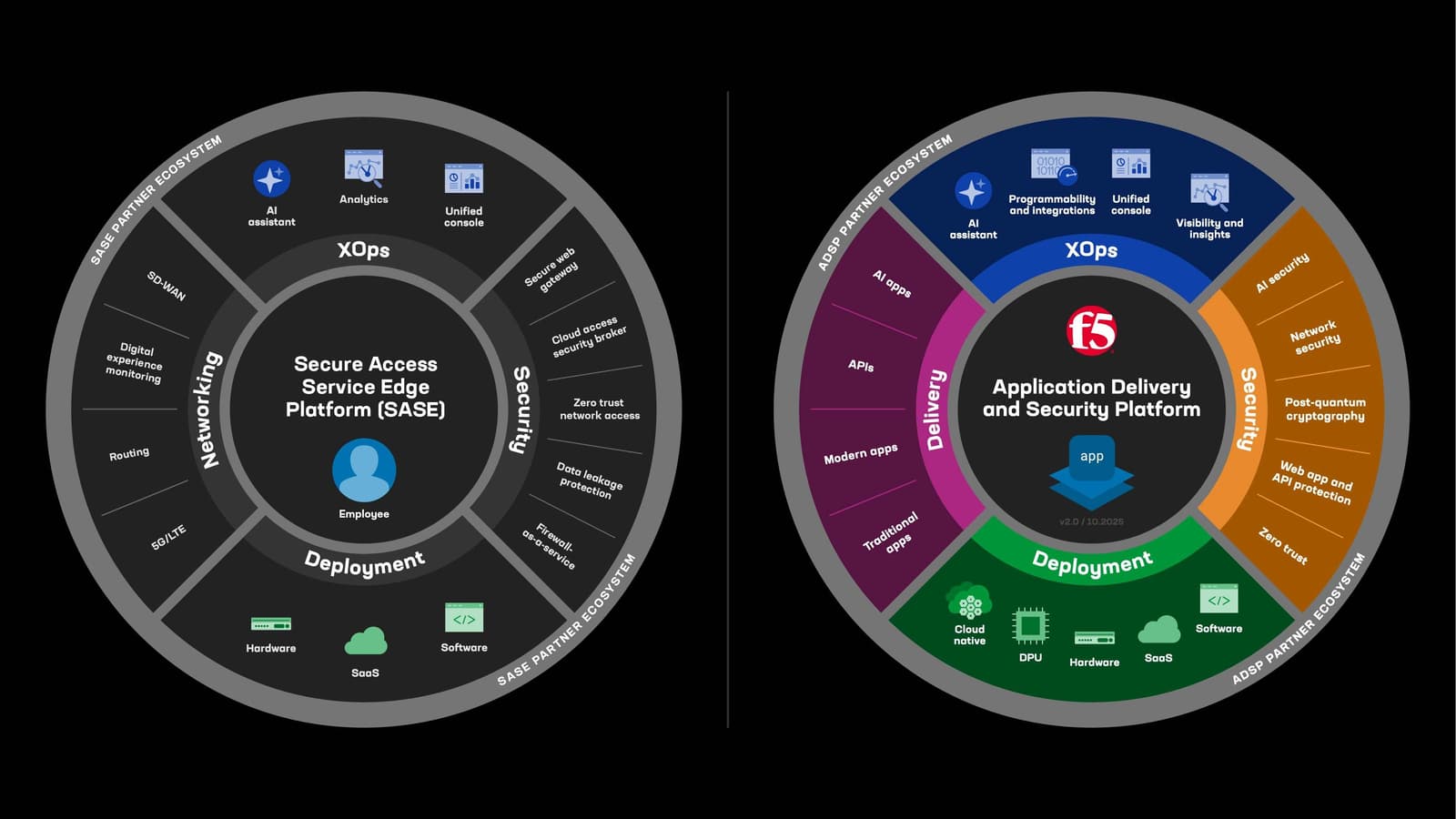
A SASE platform enforces consistent network access (SD-WAN/ZTNA) and security (security service edge) policies for enterprise employees, whether they connect from the main office or one of its branches, at home, or while traveling.
On the other hand, ADSP provides consistent application delivery through application delivery controllers (ADCs) and secures enterprise applications with web application and API protection (WAAP), regardless of whether those applications are located in a data center, across multicloud environments, or at the edge. ADSP also receives traffic from consumers connecting through a content delivery network (CDN).
So, how different are these two converged networking and security platforms?
Well, it may sound obvious, but SASE, with its emphasis on protecting employees, relies on a forward proxy to receive content from public and private applications, inspects it, and passes it to employees.
By contrast, ADSP is primarily a reverse proxy, and it intercepts traffic bound for an application, inspects it, and passes it to the appropriate server hosting the application. Fundamentally, SASE and ADSP are different core networking and security technologies with vastly different scale. Think about how many consumers access an application versus how many internal employees access a network.
SASE vs. ADSP: Differences in networking
Let’s examine the networking differences, starting with SASE. Software-Defined Wide Area Networking (SD-WAN) uses a combination of underlay to transport and overlay tunnels to deliver the most reliable path between users and the security service edge (SSE) cloud or another destination. It can dynamically steer traffic across MPLS, broadband, 5G/LTE, or satellite links based on real-time performance. Because SD-WAN is application-aware, it applies routing and traffic-engineering decisions that traditional IP routing cannot, such as selecting paths based on application identity, latency, jitter, or packet loss.
When employees connect from outside the corporate network, SD-WAN is typically not in the path. Off-network traffic relies on standard Internet routing, which provides no performance guarantees, no optimized path selection, and no enterprise QoS policies. In these cases, the cloud-based SSE functions as a forward proxy, terminating the employee's connection, inspecting outbound and inbound traffic, and then retrieving content on the employee's behalf.
ADSP addresses a different part of the networking stack. ADCs in ADSP are responsible for optimizing how requests reach applications, ensuring high performance, availability, and reliability. Operating at Layers 4–7, ADCs understand application protocols, session behavior, and traffic patterns, allowing them to perform advanced load balancing, TLS termination, health monitoring, and connection management.
Because ADSP operates as a reverse proxy, it sits in front of applications to inspect incoming traffic, enforce policies, and select the correct application instance or service. Although ADSP is closely associated with WAAP, it can also integrate with CDNs and other delivery layers to further optimize performance and global reach.
SASE vs. ADSP: Differences in security
What about security? In the SASE model, SSE protects employees, particularly their devices and browser sessions, against web and cloud-based threats. SSE originally centered on secure web gateway (SWG) capabilities but has since expanded to include cloud access security broker (CASB) controls, remote browser isolation (RBI), and data loss prevention (DLP).
By comparison, ADSP focuses on protecting applications and APIs. Its core security capabilities span web application and API protection (WAAP), including a web application firewall (WAF), Distributed Denial of Service (DDoS) mitigation, bot protection, API security, and client-side protection. Increasingly, DLP is also becoming relevant at the application edge as organizations seek to prevent sensitive data from being exposed through APIs and web applications.
Zero trust architectures
Both platforms contribute to a zero trust architecture, but they do so at different layers of the environment. SASE delivers Zero Trust Network Access (ZTNA), which validates employee identity, device posture, and contextual signals before granting access to an application. This prevents unverified users and unmanaged devices from ever reaching internal resources, dramatically reducing the attack surface at the user edge.
ADSP complements this with Zero Trust Application Access (ZTAA), which enforces access decisions at the reverse proxy that directly fronts the application. Unlike ZTNA, which governs who can attempt to connect, ZTAA oversees what they can actually do once traffic arrives. By inspecting requests, enforcing granular policies, and mediating every transaction, ZTAA protects the application itself from compromised identities, malicious payloads, and lateral movement attempts that traditional network-layer controls cannot detect.
Together, ZTNA and ZTAA provide a layered zero trust model: one secures access to the application and the other secures the application once access is granted.
How SASE and ADSP work together
SASE and ADSP address different but highly complementary challenges and both are essential to modern digital operations. Industry analysts consistently note that SASE is optimized for securing and connecting the hybrid workforce. It delivers ZTNA, SWG, CASB, and DLP capabilities at the user edge, ensuring that access to corporate resources begins with strong identity, device, and content controls.
ADSP, by contrast, is optimized for delivering and protecting the applications themselves. It provides ADC, WAAP, DDoS mitigation, Zero Trust Application Access, and API security at the app edge, where performance, resilience, and application-specific threat defenses are critical. As enterprises continue shifting to hybrid work and hybrid multicloud architectures, these two edges must operate in concert to maintain consistent performance, security, and policy enforcement across widely distributed environments.
In practice, SASE ensures that only the right employees and compliant devices can reach internal or private applications. ADSP then ensures that those applications remain fast, reliable, and protected once traffic arrives. For example, remote developers or employees access internal tools through SASE’s ZTNA controls, while customer-facing portals, APIs, and AI-powered services depend on ADSP for efficient delivery, advanced threat protection, and application-aware security.
Together, the two platforms create a holistic zero trust architecture that spans employees, networks, and applications. Neither platform can deliver this outcome alone, but together they provide the end-to-end security and performance foundation required for modern digital business.
Will SASE and ADSP ever be one platform?
For small and midsize businesses, it is reasonable to imagine SASE and ADSP delivered through a single, consolidated platform. These organizations often favor simplicity, have smaller IT teams, and benefit from consuming networking and security as one unified cloud service. In such environments, the distinction between user-edge security and application-edge delivery is less critical.
Enterprises, however, operate at a different scale. SASE and ADSP rely on different technologies, solve different problems, and are owned by distinct networking and security teams. These operational boundaries, combined with higher performance, compliance, and architectural requirements, make full convergence impractical. Large organizations gain the most value when the two platforms remain specialized yet work together seamlessly.
Gartner AI Security Platform
As enterprises increasingly adopt AI-driven workflows, the need for robust AI security strategies is growing. To address this, Gartner defines a new category called AI Security Platform (AISP)—a framework designed to secure both third-party and custom AI applications. AISP consists of two core pillars:
- AI Usage Control (AIUC): Focused on governing enterprise use of external AI tools, such as generative AI platforms or data analysis engines, by enforcing policies around data protection, IP governance, and privacy.
- AI Application Security (AIAS): Designed to safeguard custom-built AI applications from threats like adversarial AI, improperly trained models, and API abuse.
SASE and ADSP can play complementary roles within this framework. With its employee-centric, proxy-based enforcement model, SASE naturally aligns with AIUC by securing human-AI interactions and third-party integrations. ADSP, on the other hand, is well-suited to supporting AIAS, leveraging its strengths in protecting applications, APIs, and backend infrastructures at enterprise scale.
Benefits of a platform approach
Converged network and security platforms such as SASE and ADSP deliver several benefits for enterprises. They consolidate point products, simplify operations, and sync policies across networking and security functions.
Whether these two major converged platform categories can be combined is open to debate. Yet while it’s sometimes difficult for enterprises to break out of siloed ownership, the benefits of a platform approach are too big to ignore.
Explore the benefits in detail and learn how the F5 Application Delivery and Security Platform (ADSP) delivers and secures applications across every environment by visiting our F5 ADSP webpage.
About the Author

John Maddison is F5’s Chief Marketing Officer. John has more than 30 years of experience leading product teams and corporate marketing functions in cybersecurity, cloud, and telecommunications. Prior to F5, John spent 12 years at Fortinet, most recently as Chief Marketing Officer and EVP of Product Strategy. He previously held leadership positions at Trend Micro, Vina Communications, and Octel Communications. John holds a B.S. in Engineering degree from Plymouth University in Devon, England.
More blogs by John MaddisonRelated Blog Posts

Responsible AI: Guardrails align innovation with ethics
AI innovation moves fast. But without the right guardrails, speed can come at the cost of trust, accountability, and long-term value.

Best practices for optimizing AI infrastructure at scale
Optimizing AI infrastructure isn’t about chasing peak performance benchmarks. It’s about designing for stability, resiliency, security, and operational clarity

Datos Insights: Securing APIs and multicloud in financial services
New threat analysis from Datos Insights highlights actionable recommendations for API and web application security in the financial services sector

Tracking AI data pipelines from ingestion to delivery
Enterprise data must pass through ingestion, transformation, and delivery to become training-ready. Each stage has to perform well for AI models to succeed.
Secrets to scaling AI-ready, secure SaaS
Learn how secure SaaS scales with application delivery, security, observability, and XOps.
How AI inference changes application delivery
Learn how AI inference reshapes application delivery by redefining performance, availability, and reliability, and why traditional approaches no longer suffice.
