Applications have become essential to every aspect of our daily lives. To highlight a few examples, they enable us to:
- Order food—how we eat increasingly has to do with applications.
- Get around—how we arrange transportation has to do with applications.
- Meet people—how we connect is often enabled and powered by applications.
While these changes originated before COVID-19, the pandemic has undoubtedly accelerated our dependence on applications.
How we work is changed forever with hybrid or completely virtual teams. How we pay for things has changed with contactless payment technologies such as Apple Pay, Venmo, PayPal, etc. Furthermore, how we gain access to services in many countries today—restaurants, airplanes, cinemas—increasingly requires that we carry certain applications that (figuratively and literally) open doors. As a result, applications are booming.
Let's take a moment to quantify. In 2019, there were already 1 billion applications in use around the world. By 2025, that number is expected to increase fivefold (IDC, Workloads Forecast, October 2021).
The Growing Risk of Cyberattacks
As we increasingly depend on applications, it has become imperative to keep them protected from cyber threats and attacks. This is because even a single exploit or breach can result in dire consequences at great personal, organizational, and societal costs.
Have you ever found yourself frustrated with an application as its responsiveness slows to the point that it times-out, or becomes completely unresponsive? Have you had the unfortunate experience of having your personal credentials stolen and monetized?
Recent examples of cyberattacks are well documented. We have seen global brands such as Microsoft, Facebook, Walgreens, T-Mobile, and others negatively impacted or breached, with millions of their customers affected.
Unfortunately, as applications have modernized, securing them has become even more difficult. It is important, therefore, to understand the anatomy of an application, how it has evolved over time, and why the modern application design inherently expands the attack surface area.
So, let’s collectively embark on the journey to modern applications.
The Journey to Modern Applications
First, go back 25+ years to when applications where large, monolithic, single pieces of software. They were installed onto a single server (a large computer that provides functionality for the app) and an operating system such as Windows NT.
Years later, virtualization made it possible to install and run multiple application servers on a single piece of hardware and share its resources.
Next was the broad adoption of cloud—which afforded availability of on-demand, limitless computing infrastructure, while avoiding the need for capital-intensive upfront investments in data centers.
Despite all these advancements, app developers demanded greater agility and more granular development capabilities. This led to the birth of containers—the next iteration of virtualization. A container provides a small, lightweight piece of the overall application architecture to control and modularize app virtualization.
Let's use a typical retail mobile app as an example. From an app developer’s perspective, the development might break down into distinct components—e.g., login and account information, inventory, orders, and reporting and analytics. This helps the developer add, swap, or amend a piece of the application without having to make substantial changes to the application.
The overall application is modularized with services—often referred to as microservices—delivered in clusters. In addition, what links each of these app components, including their connection to third-party apps, is an application programming interface (API), which facilitates the service-to-service communication that connects applications (more on this in our fourth blog in this series.)
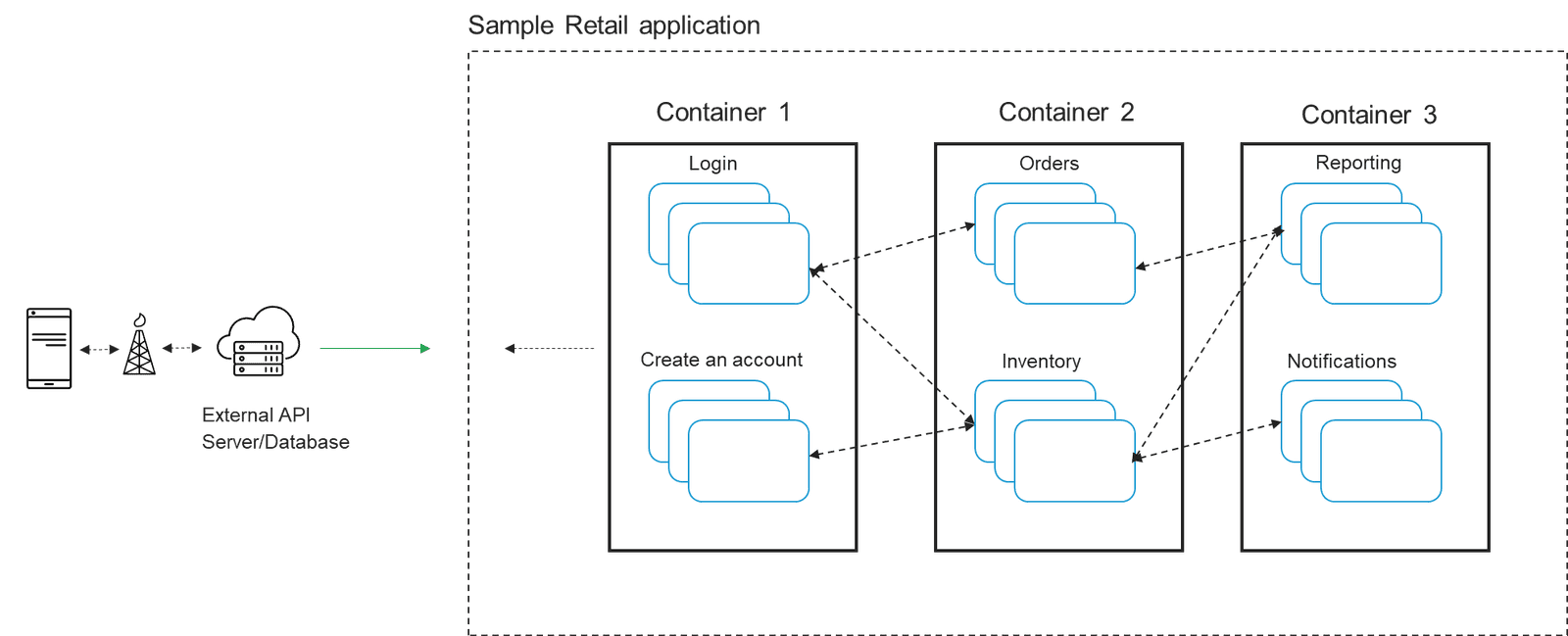
Meanwhile, however, as technology and architecture have evolved to enable more agile development and delivery of apps, complexity has become an issue.
Securing Apps and APIs in a Distributed World
Over the past quarter century, we have evolved from a world of monolithic apps tethered to a single piece of hardware in a server room or data center to containers and microservices-based modern applications that are built and deployed anywhere—in a data center, in multiple clouds, and at the edge (to bring app computation closer to a user or data source and minimize latency).
Obviously, a perimeter-approach to security is no longer feasible. Computing that was once contained to a single server, now happens literally anywhere. And while it all needs security (obviously), applying a unique security tool to each component is equally unfeasible. It would almost be akin to a global company empowering each employee to shop for their own insurance policy (and then paying for each individually) instead of having a flexible group policy that employees could opt into.
The resulting conundrum is that securing apps and APIs has never been more challenging. It is partly why today the average company invests twice as much money in security as it does in conventional IT (IDC, Workloads Forecast, October 2021). Moreover, the stakes have never been higher, as breaches can have ruinous effects for corporations and customers alike.
Watch the video below to learn how F5 is providing organizations with technology that ensures your favorite apps are protected and that your digital experiences are always secure.
Next in this four-part series for Cybersecurity Awareness Month, we will explore further attack and attacker schemes to exploit applications and APIs, and how organizations and app users can stay protected.
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.