As early as 2009, when cloud was just beginning to rise ascendant as the technology most likely to disrupt, well, everything, many of us began looking at the problem of consistency at the infrastructure level. Under the moniker of “infrastructure 2.0” we looked at the role of programmability – APIs, templates, configuration models – and the issue of achieving consistent policy provisioning and enforcement in what we then called an “intercloud” world.
Today we call that hybrid or multi-cloud, and the issue still remains: how do we achieve consistency of policy in an environment that incorporates traditional infrastructure models with cloud computing?

And it is still an issue. CloudPassage, a managed cloud security provider, commissioned a survey that garnered over 1000 responses on the topic of cloud and security, finding that “consistency across IT infrastructure” and “continuous protection” were the most important factors for protecting cloud infrastructure, with 60% and 58% percent of respondents agreeing, respectively. When asked about methods for closing the cloud security gap that continues to plague organizations, the number one method cited was the “ability to enforce consistent, continuous security policies.”
This desire for policy parity between cloud and on-premises showed itself again when We (that’s the corporate We) conducted our annual State of Application Delivery survey this year, in which 48% of the more than 3000 respondents cited “security and audit parity with on-premises” as one of the top three security requirements for cloud adoption.
The problem we sought to address back in 2009 remains: how do we achieve parity of policies across infrastructure on-premises and in the cloud without stripping security down to its bare minimum so as to support the broadest set of options possible? After all, configuration models across vendors already varies widely. Adding cloud computing into the mix only increases the variety of models and methods used to manage and control security. A standard app security policy used to implement a web application firewall (WAF) policy on-premises, for example, cannot simply by reused by a cloud provider. A distinct policy must be created, which then must be maintained, managed, and audited. Achieving parity in such situations requires diligent attention to insuring both policies are enforcing the same security in both environments.
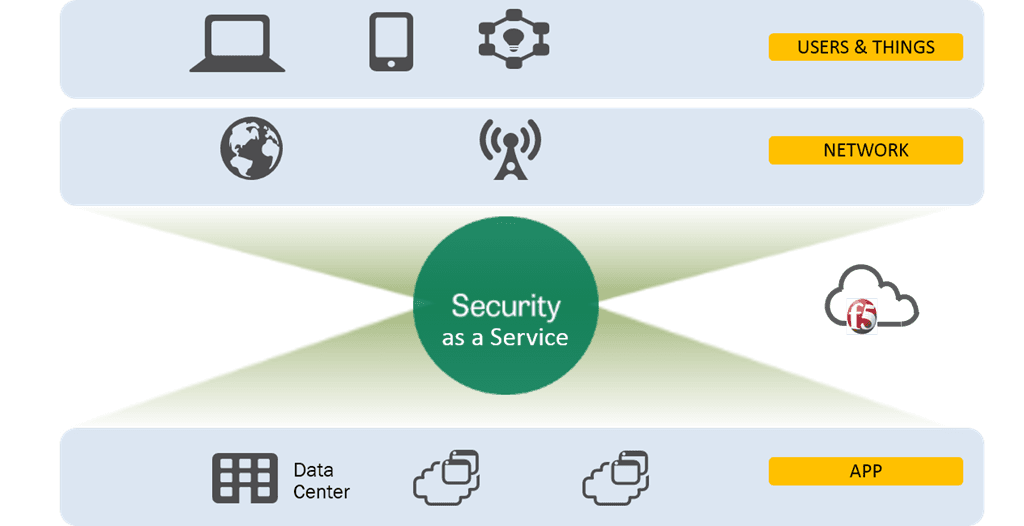
This is unsustainable. It is operationally difficult, administratively expensive, and fraught with the potential for errors. Costly errors.
One of the ways to achieve the consistency desired is actually to look to the cloud itself, to those security services that can be offered as a service, in the cloud. Such services can generally be identified as being upstream from the application and responsible for inspection and scrubbing before application requests are allowed to reach the application. DDoS prevention, WAF services, SPAM mitigation, and malware detection are all in the category of upstream application services that can be effectively offloaded to a cloud-based service to ensure consistency of policy across all applications, regardless of whether they’re in the cloud or on-premises. Much in the same way a CDN offloads caching services, these security-as-a-service options provide consistency for multi-cloud environments because they can use the same policies or base policies across multiple applications and environments.
The need for consistent policy enforcement, particularly those policies that relate to security, is only going to grow as the Internet of Things becomes more prevalent and organizations continue to expand their presence not just in the cloud, but in many clouds. Variety may be the spice of life, but for security, too many cooks spoil the soup. And if I could find one more idiom to mix in with my metaphors, I would because it’s existentially illustrating the challenge that needs to be addressed.
Security is hard enough as it is. Adding more environments, more systems, and more and differenter policies to the mix only makes it more difficult. And in a world where there’s a shortage of security talent, it makes sense to seek out and take advantage of any solution that makes it easier to not just deploy and manage but enforce security policies in an increasingly multi-everything-under-the-sun world.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
