Over the years we've seen a lot of industry trends come and go. Two—cloud and mobility—fall into what we might call "mega trends." These are movements within the industry that have been disruptive and ultimately changed the face of computing.
Mobility was first, and it opened the eyes of consumers to the possibility of computing on the go. Our phones became our constant companions. The apps we relied on for entertainment and collaboration, however, were not as mobile.
Public cloud provided an answer to that, offering new locations and ways of deploying applications. Today, nearly nine in ten (87%) of organizations maintain an application presence in multiple public cloud properties.
With so many applications in the public cloud, application traffic patterns have shifted. Our customers now see traffic increasingly destined for a public cloud, whether that traffic is generated by employees or their customers.
What hasn't changed is the need to secure that traffic. Indeed, that need may be more pronounced now than it ever has been.
According to Sophos in its State of Cloud Security 2020 report, "multi-cloud organizations reported more security incidents in the last 12 months. Seventy-three percent (73%) of the organizations surveyed were using two or more public cloud providers and reported more security incidents than those using a single platform."
The challenge facing business today is that the corporate perimeter at which security controls are traditionally operated is gone. New control points must be implemented because security is not optional.
The challenge is combatting complexity. With some applications remaining in the data center and others moving to multiple cloud properties, one solution is to deploy the appropriate security controls in every cloud as well as within the data center. These multiple implementations lead to inconsistent policies, lack of full visibility of security threats, and significant operational overhead. As a result, many organizations abandon such a strategy, which leaves them open to attack.
Deploying these new security control points at a central location where users, public clouds, and data intersect is a winning strategy. It offers better visibility, consistent policy control, less operational overhead and more efficient use of resources. One such location is Equinix, which offers lightning fast, ultra-low latency connections to the public clouds already used by most organizations via their virtual interconnection solution, Equinix Cloud Exchange (ECX).
We've previously established the general benefits of BIG-IP as a cloud gateway co-located in Equinix. Today, as promised, we're going to dig into the specific use case for SSLO (SSL Orchestration) to improve business outcomes.
BIG-IP and SSLO in Equinix
The challenge organizations face with a multi-cloud application portfolio is significant. Moreover, our research indicates the most pressing challenge for the past three years with respect to multi-cloud has been enforcing consistent security policies across all applications, anywhere. Privacy and security concerns mean nearly all traffic today is encrypted. Mary Meeker notes that the share of encrypted traffic was already at 87% at the beginning of 2019, and Google’s latest transparency report shows nearly 90% of all web-based traffic is using encryption.
Most organizations use, on average, ten different application services to secure, deliver, and optimize applications. Choosing only one is not really an option. Security dominates the most frequently deployed services: DNSSEC, bot defense, and anti-fraud. There is no single application service that provides all the security capabilities an organization needs to protect its infrastructure and applications against extant and emerging threats. The need for these services across all environments leads to significant challenges with integration and orchestration in a seamless, easy to use fashion.
While you could chain multiple security services together, not all applications and traffic need to be evaluated by the same set of security services. Hand-crafting is great for gifts, not so much for managing security flows for every one of your applications.
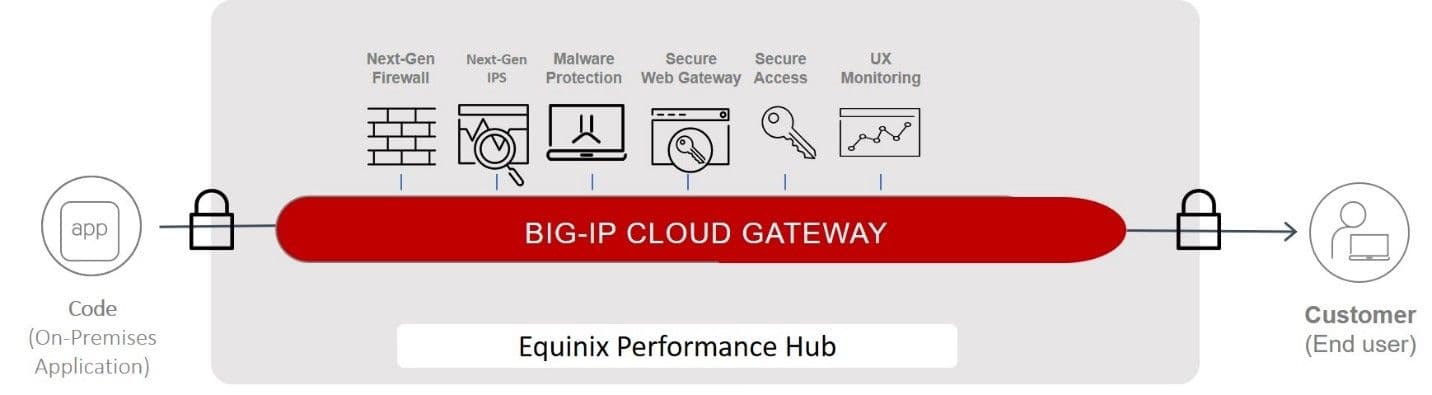
Using BIG-IP as a cloud gateway deployed on the Equinix Platform enables organizations to create a security control point while employing the capabilities of multiple security application services without the operational overhead of manually integrating and orchestrating security services on a per application basis. BIG-IP SSL Orchestrator (SSLO) ensures that traffic is correctly routed to the appropriate security services before that traffic is deemed safe to send on to its destination in a public cloud or in the data center. BIG-IP SSLO decrypts encrypted traffic and then, based on the type and source of traffic, steers it to the appropriate security services for inspection. This means dynamic service chaining that's based on logic and not manual directives. The result is enhanced visibility to mitigate threats while preserving existing security investments in malware, data-loss prevention, next-gen firewalls, and other security devices.
BIG-IP SSLO also integrates with Equinix SmartKeyTM, which provides a cloud-hardware security module (HSM) as a service to ensure dependable, multi-cloud security for sensitive cryptographic keys.
The benefits of using BIG-IP SSLO in Equinix to enforce centralized security policies include:
- Optimized Cost Efficiency. Cloud resources are not consumed unless the user and request has been inspected and cleared of malicious content/intent. Cloud costs are kept under control by refusing service to bad actors and bots.
- Simplified Operations. A single security control point along with a consistent set of security services reduce operational overload caused by multiple dashboards, consoles, logs, and policy languages.
- Improved Security Outcomes. The centralization of security while supporting a multi-cloud reality enables consistent security policies that cover all applications. Consistency of policy and enforcement is key to improving the security posture of the business and avoiding those all-too-common cloud security incidents.
There are more benefits to employing a cloud gateway in the Equinix environment and we're going to dive into more detail in subsequent posts, each focusing on a different capability―and the benefits―of a cloud gateway.
If you can’t wait and want to dive in now, here are some resources you can check out to learn more:
- Equinix Technology Alliance
- Equinix & F5: Taking Control Of Your Hybrid Cloud Security
- Improving Business Outcomes and Application Experiences with a Cloud Gateway in Equinix
Stay safe and stay tuned for more!
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
